Wireless-G Business USB Network Adapter with RangeBooster
The following table is a summary of the various alert descriptions and advice.
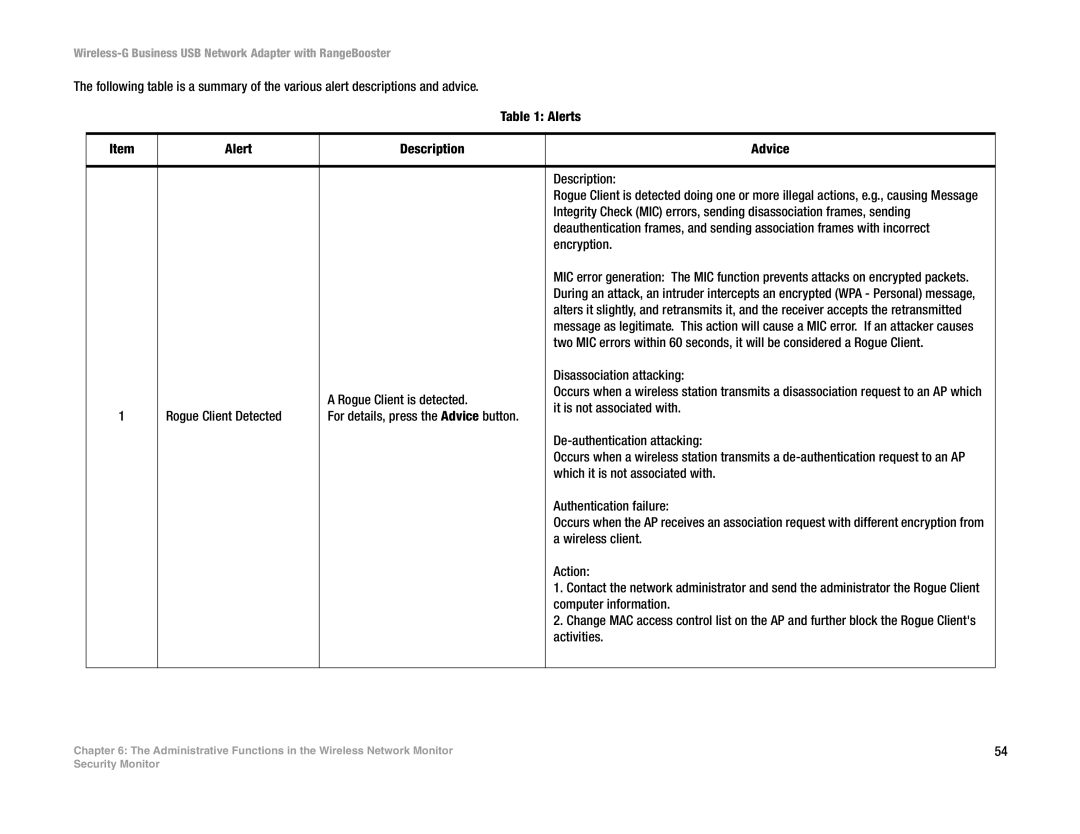
Table 1: Alerts
Item | Alert | Description | Advice | |
|
|
|
| |
|
|
| Description: | |
|
|
| Rogue Client is detected doing one or more illegal actions, e.g., causing Message | |
|
|
| Integrity Check (MIC) errors, sending disassociation frames, sending | |
|
|
| deauthentication frames, and sending association frames with incorrect | |
|
|
| encryption. | |
|
|
| MIC error generation: The MIC function prevents attacks on encrypted packets. | |
|
|
| During an attack, an intruder intercepts an encrypted (WPA - Personal) message, | |
|
|
| alters it slightly, and retransmits it, and the receiver accepts the retransmitted | |
|
|
| message as legitimate. This action will cause a MIC error. If an attacker causes | |
|
|
| two MIC errors within 60 seconds, it will be considered a Rogue Client. | |
|
|
| Disassociation attacking: | |
|
| A Rogue Client is detected. | Occurs when a wireless station transmits a disassociation request to an AP which | |
|
| it is not associated with. | ||
1 | Rogue Client Detected | For details, press the Advice button. | ||
| ||||
|
|
| ||
|
|
| Occurs when a wireless station transmits a | |
|
|
| which it is not associated with. | |
|
|
| Authentication failure: | |
|
|
| Occurs when the AP receives an association request with different encryption from | |
|
|
| a wireless client. | |
|
|
| Action: | |
|
|
| 1. Contact the network administrator and send the administrator the Rogue Client | |
|
|
| computer information. | |
|
|
| 2. Change MAC access control list on the AP and further block the Rogue Client's | |
|
|
| activities. | |
|
|
|
|
Chapter 6: The Administrative Functions in the Wireless Network Monitor | 54 |
Security Monitor