INSTALLATION | SECTION 2 |
|
|
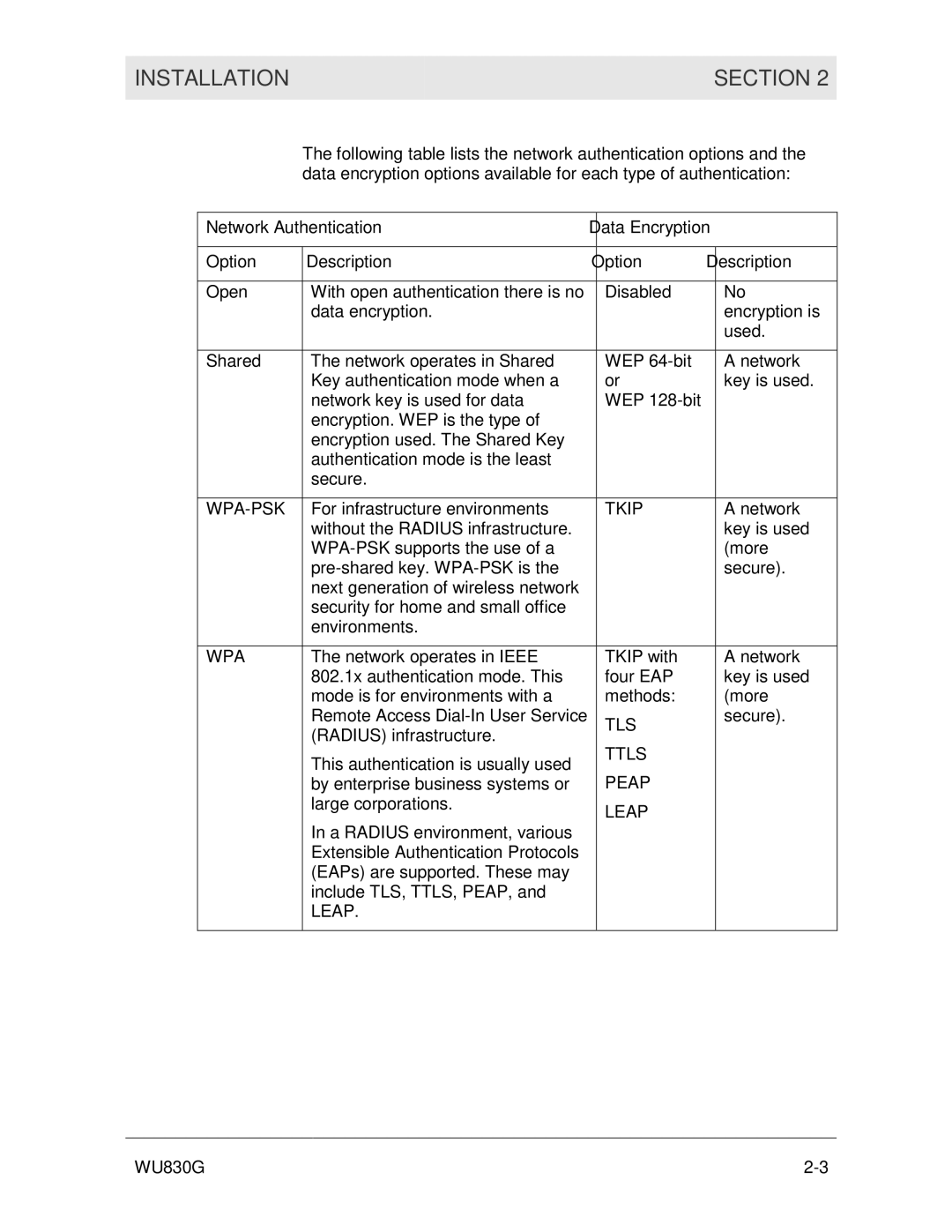
The following table lists the network authentication options and the data encryption options available for each type of authentication:
Network Authentication | Data Encryption | ||
|
|
|
|
Option | Description | Option | Description |
|
|
|
|
Open | With open authentication there is no | Disabled | No |
| data encryption. |
| encryption is |
|
|
| used. |
|
|
|
|
Shared | The network operates in Shared | WEP | A network |
| Key authentication mode when a | or | key is used. |
| network key is used for data | WEP |
|
| encryption. WEP is the type of |
|
|
| encryption used. The Shared Key |
|
|
| authentication mode is the least |
|
|
| secure. |
|
|
|
|
|
|
For infrastructure environments | TKIP | A network | |
| without the RADIUS infrastructure. |
| key is used |
|
| (more | |
|
| secure). | |
| next generation of wireless network |
|
|
| security for home and small office |
|
|
| environments. |
|
|
|
|
|
|
WPA | The network operates in IEEE | TKIP with | A network |
| 802.1x authentication mode. This | four EAP | key is used |
| mode is for environments with a | methods: | (more |
| Remote Access | TLS | secure). |
| (RADIUS) infrastructure. | TTLS |
|
| This authentication is usually used |
| |
| PEAP |
| |
| by enterprise business systems or |
| |
| large corporations. | LEAP |
|
| In a RADIUS environment, various |
| |
|
|
| |
| Extensible Authentication Protocols |
|
|
| (EAPs) are supported. These may |
|
|
| include TLS, TTLS, PEAP, and |
|
|
| LEAP. |
|
|
|
|
|
|
WU830G |