ProSafe 5 AP Wireless Management Software WMS105
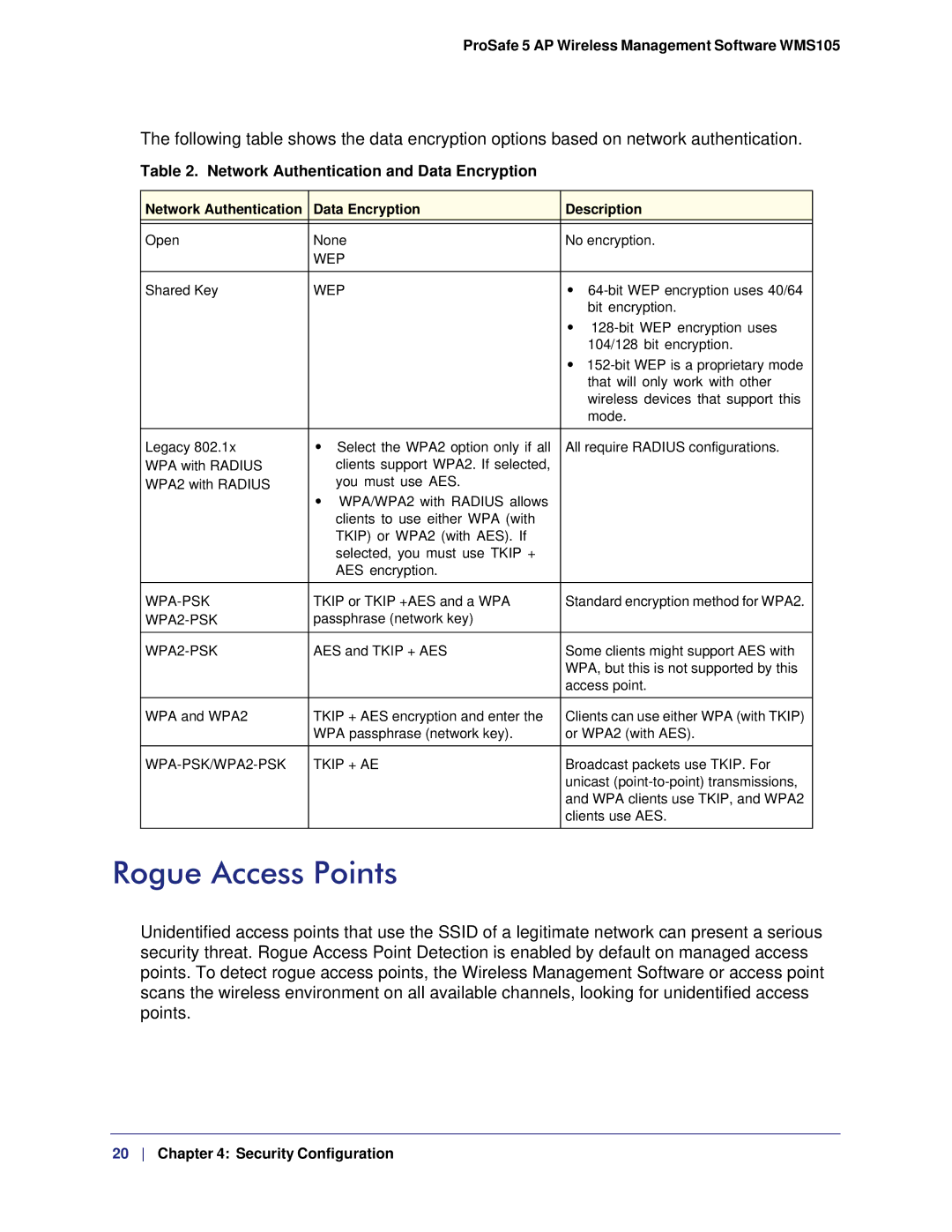
The following table shows the data encryption options based on network authentication.
Table 2. Network Authentication and Data Encryption
| Network Authentication | Data Encryption | Description |
|
|
|
|
| Open | None | No encryption. |
|
| WEP |
|
|
|
|
|
| Shared Key | WEP | • |
|
|
| bit encryption. |
|
|
| • |
|
|
| 104/128 bit encryption. |
|
|
| • |
|
|
| that will only work with other |
|
|
| wireless devices that support this |
|
|
| mode. |
|
|
|
|
| Legacy 802.1x | • Select the WPA2 option only if all | All require RADIUS configurations. |
| WPA with RADIUS | clients support WPA2. If selected, |
|
| WPA2 with RADIUS | you must use AES. |
|
|
| • WPA/WPA2 with RADIUS allows |
|
|
| clients to use either WPA (with |
|
|
| TKIP) or WPA2 (with AES). If |
|
|
| selected, you must use TKIP + |
|
|
| AES encryption. |
|
|
|
|
|
| TKIP or TKIP +AES and a WPA | Standard encryption method for WPA2. | |
| passphrase (network key) |
| |
|
|
|
|
| AES and TKIP + AES | Some clients might support AES with | |
|
|
| WPA, but this is not supported by this |
|
|
| access point. |
|
|
|
|
| WPA and WPA2 | TKIP + AES encryption and enter the | Clients can use either WPA (with TKIP) |
|
| WPA passphrase (network key). | or WPA2 (with AES). |
|
|
|
|
|
| TKIP + AE | Broadcast packets use TKIP. For |
|
|
| unicast |
|
|
| and WPA clients use TKIP, and WPA2 |
|
|
| clients use AES. |
|
|
|
|
Rogue Access Points |
| ||
Unidentified access points that use the SSID of a legitimate network can present a serious security threat. Rogue Access Point Detection is enabled by default on managed access points. To detect rogue access points, the Wireless Management Software or access point scans the wireless environment on all available channels, looking for unidentified access points.
20 Chapter 4: Security Configuration