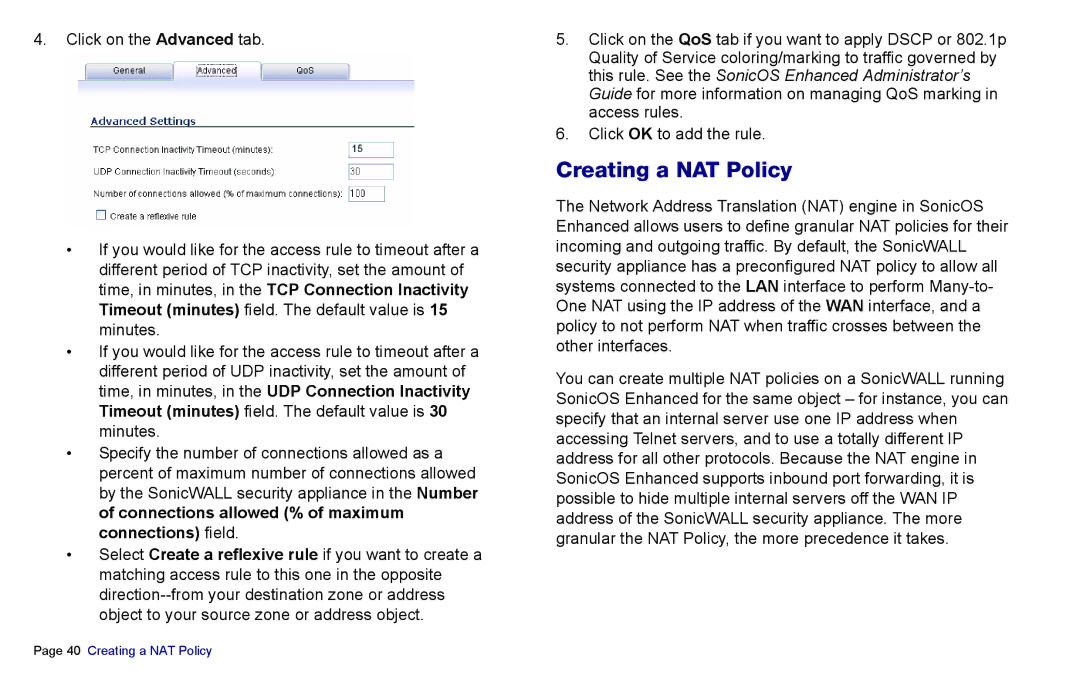
4.Click on the Advanced tab.
•If you would like for the access rule to timeout after a different period of TCP inactivity, set the amount of time, in minutes, in the TCP Connection Inactivity Timeout (minutes) field. The default value is 15 minutes.
•If you would like for the access rule to timeout after a different period of UDP inactivity, set the amount of time, in minutes, in the UDP Connection Inactivity Timeout (minutes) field. The default value is 30 minutes.
•Specify the number of connections allowed as a percent of maximum number of connections allowed by the SonicWALL security appliance in the Number of connections allowed (% of maximum connections) field.
•Select Create a reflexive rule if you want to create a matching access rule to this one in the opposite
5.Click on the QoS tab if you want to apply DSCP or 802.1p Quality of Service coloring/marking to traffic governed by this rule. See the SonicOS Enhanced Administrator’s Guide for more information on managing QoS marking in access rules.
6.Click OK to add the rule.
Creating a NAT Policy
The Network Address Translation (NAT) engine in SonicOS Enhanced allows users to define granular NAT policies for their incoming and outgoing traffic. By default, the SonicWALL security appliance has a preconfigured NAT policy to allow all systems connected to the LAN interface to perform
You can create multiple NAT policies on a SonicWALL running SonicOS Enhanced for the same object – for instance, you can specify that an internal server use one IP address when accessing Telnet servers, and to use a totally different IP address for all other protocols. Because the NAT engine in SonicOS Enhanced supports inbound port forwarding, it is possible to hide multiple internal servers off the WAN IP address of the SonicWALL security appliance. The more granular the NAT Policy, the more precedence it takes.
Page 40 Creating a NAT Policy