Americas Headquarters
Text Part Number
Copyright 2007-2009 Cisco Systems, Inc. All rights reserved
RPR
Startup Configuration File
Configuring POS Interface Framing Mode
Iii
Understanding VLANs
Configuring Encapsulation over EtherChannel or POS Channel
IP ACLs
Role of Sonet Circuits
Vii
Configuration Guidelines
Viii
Using Technical Support C-1
Page
11-5
11-3
11-4
11-7
14-18
14-13
14-17
14-22
11-11
10-5
10-6
11-12
13-3
17-7
17-8
This section provides the following information
Preface
Revision History
Date
Document Objectives
Audience
Related Documentation
Boldface
Document Conventions
Convention Application
Italic
Bewaar Deze Instructies
Warnung Wichtige Sicherheitshinweise
Avvertenza Importanti Istruzioni Sulla Sicurezza
Aviso Instruções Importantes DE Segurança
Page
GEM Disse Anvisninger
Viii
Where to Find Safety and Warning Information
Obtaining Optical Networking Information
Cisco Optical Networking Product Documentation CD-ROM
Page
Overview of the ML-Series Card
ML-Series Card Description
ML-Series Feature List
IRB
Bundling the two POS ports LEX encapsulation only
GFP-F Framing
Key ML-Series Features
Cisco IOS
Cisco IOS Release 12.228SV
Link Aggregation FEC and POS
Rmon
TL1
ML-Series POS Statistics Fields and Buttons
CTC Operations on the ML-Series Card
Displaying ML-Series POS Statistics in CTC
Refresh
Displaying ML-Series Ethernet Statistics in CTC
Button Description
ML-Series Ethernet Statistics Fields and Buttons
CTC
Displaying Sonet Alarms
Displaying J1 Path Trace
Provisioning Sonet Circuits
78-18133-01
Page
Initial Configuration of the ML-Series Card
Hardware Installation
Cisco IOS on the ML-Series Card
Opening a Cisco IOS Session Using CTC
Telnetting to the Node IP Address and Slot Number
Telnetting to a Management Port
CTC Node View Showing IP Address
RJ-11 to RJ-45 Console Cable Adapter
Connecting a PC or Terminal to the Console Port
ML-Series IOS CLI Console Port
RJ-11 Pin RJ-45 Pin
Startup Configuration File
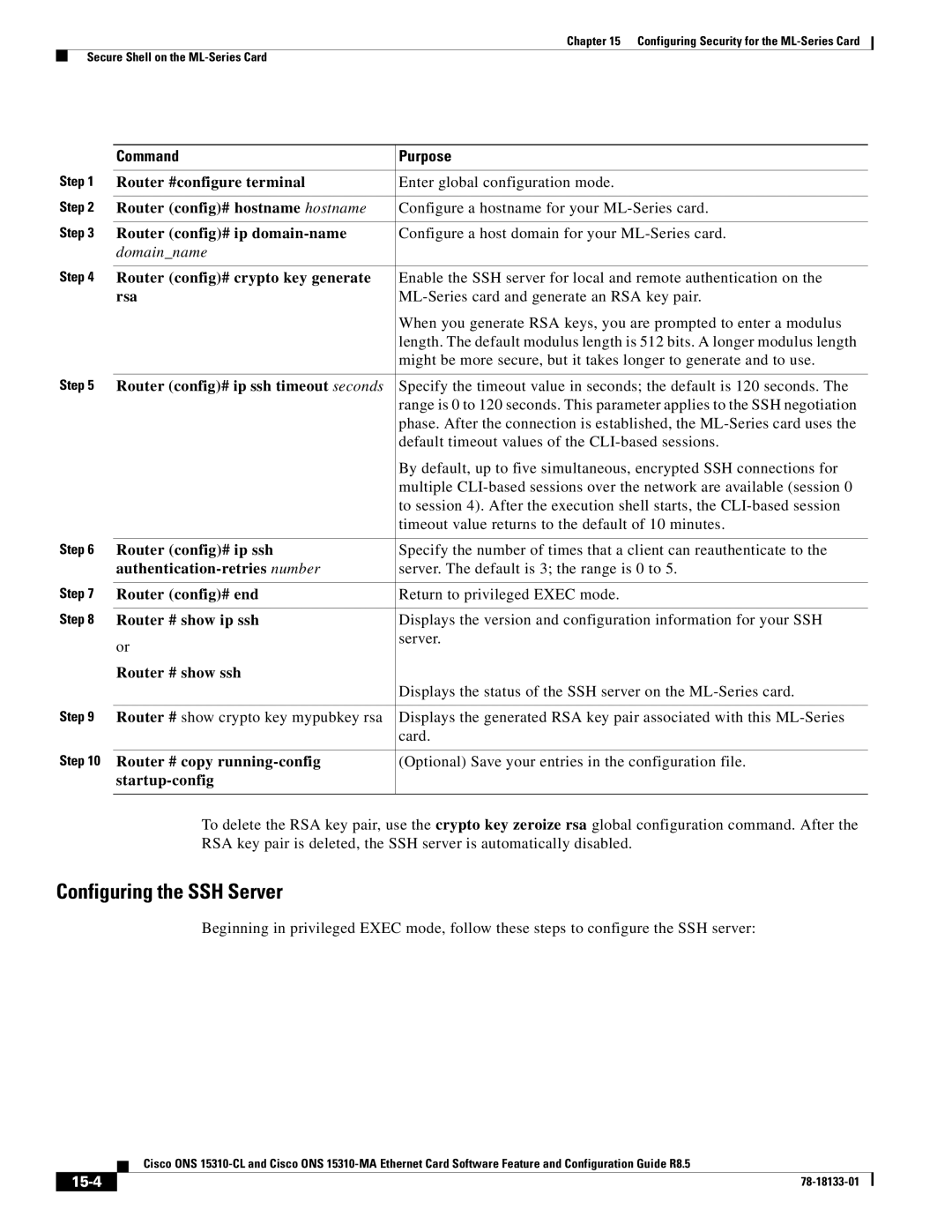
Command Purpose
Passwords
Configuring the Management Port
Router enable
Configuring the Hostname
Nvram
Loading a Cisco IOS Startup Configuration File Through CTC
Click the IOS startup config button
Cisco IOS Command Modes
Database Restore of the Startup Configuration File
Interface fastethernet 0 for
Mode What You Use It For How to Access Prompt
Enter the configure terminal
Enter the line console
Exit
Using the Command Modes
Router# configure ?
Getting Help
Page
Configuring Interfaces on the ML-Series Card
General Interface Guidelines
MAC Addresses
Interface Port ID
MLSeries# show interfaces fastethernet
Basic Interface Configuration
MLSeries# configure terminal
MLSeriesconfig# interface fastethernet number
Basic Fast Ethernet and POS Interface Configuration
Configuring the Fast Ethernet Interfaces
Configuring the POS Interfaces
Monitoring Operations on the Fast Ethernet Interfaces
Hdlc
Example 4-3 show controller Command Output
FCR
Example 4-4 show run interface Command Output
Daytona# show run interface fastethernet
Configuring POS on the ML-Series Card
Understanding POS on the ML-Series Card
Available Circuit Sizes and Combinations
Ccat High Order Vcat High Order
J1 Path Trace, and Sonet Alarms
Lcas Support
Mbps STS-1 STS-1-1v STS-1-2v
CRC Sizes Bit default None FCS disabled
Configuring the POS Interface
Encapsulations LEX default Cisco Hdlc
GFP-F Framing Hdlc Framing
Allowed only when the interface is shut down
Configuring POS Interface Framing Mode
Framing mode changes on POS ports are
Admindown
Form of the command sets the framing mode
Sets the framing mode employed by the ONS
Not a keyword choice in the command. The no
GFP default-The ML-Series card supports
Sonet Alarms
Configuring Sonet Alarms
Configuring Sonet Delay Triggers
All -All alarms/signals
Monitoring and Verifying POS
Hdlc
Page
Configuring STP and Rstp on the ML-Series Card
STP Features
These sections describe how the spanning-tree features work
STP Overview
Supported STP Instances
Bridge Protocol Data Units
Election of the Root Switch
Switch Priority Value
Bridge ID, Switch Priority, and Extended System ID
Spanning-Tree Timers
Bit
Creating the Spanning-Tree Topology
Spanning-Tree Interface States
Blocking State
Spanning-Tree Interface States
Learning State
Disabled State
Listening State
Forwarding State
Spanning-Tree Address Management
STP and Ieee 802.1Q Trunks
Spanning Tree and Redundant Connectivity
Rstp Features
Accelerated Aging to Retain Connectivity
Supported Rstp Instances
Port Roles and the Active Topology
Is Port Included
Port State Comparison
Rapid Convergence
Synchronization of Port Roles
Proposal and Agreement Handshaking for Rapid Convergence
Bridge Protocol Data Unit Format and Processing
Bit Function
Rstp Bpdu Flags
Topology Changes
Processing Superior Bpdu Information
Processing Inferior Bpdu Information
Configuring STP and Rstp Features
Interoperability with Ieee 802.1D STP
Default STP and Rstp Configuration
Feature Default Setting
Disabling STP and Rstp
Configuring the Root Switch
Configuring the Port Priority
Port-channel-number
Configuring the Path Cost
Configuring the Switch Priority of a Bridge Group
Configuring the Hello Time
Configuring the Forwarding-Delay Time for a Bridge Group
Configuring the Maximum-Aging Time for a Bridge Group
Verifying and Monitoring STP and Rstp Status
Displays detailed STP or Rstp information
Commands for Displaying Spanning-Tree Status
Example 6-1 show spanning-tree Commands
Displays brief summary of STP or Rstp information
Page
Configuring VLANs on the ML-Series Card
Understanding VLANs
Configuring Ieee 802.1Q Vlan Encapsulation
Optional Saves your configuration changes to
Ieee 802.1Q Vlan Configuration
Returns to privileged Exec mode
MLSeriesconfig-subif# end
Bridging Ieee 802.1Q VLANs
Example 7-2 Output for show vlans Command
Monitoring and Verifying Vlan Operation
ML-Series#show vlans
Page
Understanding Ieee 802.1Q Tunneling
Ieee 802.1Q Tunnel Ports in a Service-Provider Network
FCS
Configuring Ieee 802.1Q Tunneling
Ieee 802.1Q Tunneling and Compatibility with Other Features
Configuring an Ieee 802.1Q Tunneling Port
Optional Saves your entries in the configuration file
Untagged will be switched based on this bridge-group. Other
Displays the tunnel ports on the switch
Ieee 802.1Q Example
VLAN-Transparent Services VLAN-Specific Services
Example 8-2 MLSeries B Configuration
VLAN-Transparent Service Versus VLAN-Specific Services
Example 8-3 ML-Series Card a Configuration
Example 8-3applies to ML-Series card a
Example 8-4applies to ML-Series card B
Example 8-4 ML-Series Card B Configuration
Example 8-5 ML-Series Card C Configuration
Example 8-5applies to ML-Series card C
Configuring Layer 2 Protocol Tunneling
Understanding Layer 2 Protocol Tunneling
2shows the default Layer 2 protocol tunneling configuration
Default Layer 2 Protocol Tunneling Configuration
Layer 2 Protocol Tunneling Configuration Guidelines
Default Layer 2 Protocol Tunneling Configuration
Configuring Layer 2 Tunneling on a Port
Configuring Layer 2 Tunneling Per-VLAN
Monitoring and Verifying Tunneling Status
Configuring Link Aggregation on the ML-Series Card
Understanding Link Aggregation
Configuring Link Aggregation
Configuring Fast EtherChannel
EtherChannel Configuration Example
Cisco IOS Configuration Fundamentals Configuration Guide
Creates the POS channel interface. You can
Configuring POS Channel
Configure one POS channel on the ML-Series card
Assigns an IP address and subnet mask to the POS
POS Channel Configuration Example
Configuring Encapsulation over EtherChannel or POS Channel
Understanding Encapsulation over FEC or POS Channel
Example 9-5 MLSeries a Configuration
Configuration mode and enable other
Supported interface commands to meet
Encapsulation over EtherChannel Example
Example 9-6 MLSeries B Configuration
Monitoring and Verifying EtherChannel and POS
XOR Result Port Channel
Load Balancing on the ML-Series cards
For the Frame
Port
Frame
Used Member
Interface for
EtherChannel
Third
Second
First
Fourth
Used Member
Understanding Integrated Routing and Bridging
Configuring IRB on the ML-Series Card
Cisco IOS Command Reference publication
This chapter includes the following major sections
Configuring IRB
10-2
IRB Configuration Example
10-3
Monitoring and Verifying IRB
Example 10-1 Configuring MLSeries a
Example 10-2 Configuring MLSeries B
10-4
10-5
Field Description
10-6
Configuring Quality of Service on the ML-Series Card
11-1
Priority Mechanism in IP and Ethernet
IP Precedence and Differentiated Services Code Point
Understanding QoS
11-2
Ethernet CoS
11-3
ML-Series QoS
Classification
11-4
Policing
Marking and Discarding with a Policer
11-5
Queuing
Scheduling
11-6
Control Packets and L2 Tunneled Protocols
11-7
QinQ Implementation
Egress Priority Marking
Ingress Priority Marking
11-8
QoS on RPR
Flow Control Pause and QoS
11-9
Configuring QoS
Creating a Traffic Class
11-10
Creating a Traffic Policy
11-11
Class class-map-name no class class-map-name
Syntax of the class command is
Policy-map policy-nameno policy-map policy-name
Maximum of 40 alphanumeric characters
11-13
Command
11-14
Attaching a Traffic Policy to an Interface
11-15
Displays all configured traffic policies
Monitoring and Verifying QoS Configuration
Configuring CoS-Based QoS
Traffic class
QoS Configuration Examples
11-17
Traffic Classes Defined Example
Traffic Policy Created Example
11-18
Example 11-8 Class Map SPR Interface Command Example
Example 11-6 Class Map Match All Command Example
Example 11-7 Class Map Match Any Command Example
Match spr1 Interface Example
ML-Series Policing Example
Example 11-9 ML-Series VoIP Commands
ML-Series VoIP Example
11-20
Routerconfig# policy-map policef0
Example 11-10 ML-Series Policing Commands
Routerconfig# class-map match-all policer
ML-Series CoS-Based QoS Example
11-22
ML-Series CoS Example
Default Multicast QoS
11-23
Configuring Multicast Priority Queuing QoS
Multicast Priority Queuing QoS Restrictions
11-24
11-25
QoS not Configured on Egress
ML-Series Egress Bandwidth Example
11-26
11-27
Bandwidth
Statistics Collected Interface Subinterface Vlan
Understanding CoS-Based Packet Statistics
Fast Ethernet
11-28
Configuring CoS-Based Packet Statistics
11-29
MLSeries# show interface fastethernet 0 cos
Understanding IP SLA
11-30
MLSeries# show interface pos0 cos
IP SLA on the ML-Series
IP SLA Restrictions on the ML-Series
11-31
11-32
Understanding the SDM
Understanding SDM Regions
12-1
Default Size
Configuring SDM
Configuring SDM Regions
Lookup Type
Monitoring and Verifying SDM
Configuring Access Control List Size in Tcam
Task Command
Entries
12-4
ML-Series ACL Support
Configuring Access Control Lists on ML-Series Card
Understanding ACLs
13-1
User Guidelines
IP ACLs
Named IP ACLs
13-2
Creating IP ACLs
Creating Numbered Standard and Extended IP ACLs
13-3
Applying the ACL to an Interface
Creating Named Standard IP ACLs
Creating Named Extended IP ACLs Control Plane Only
13-4
13-5
Controls access to an interface
Modifying ACL Tcam Size
Applying ACL to Interface
13-6
Configuring Resilient Packet Ring on ML-Series Card
Understanding RPR
14-1
Role of Sonet Circuits
Packet Handling Operations
14-2
Ring Wrapping
14-3
RPR Framing Process
14-4
14-5
DA-MAC and 0x00 for Unknown DA-MAC
RPR as the source
RPR Frame for ML-Series Card
RPR QoS
Configuring RPR
MAC Address and Vlan Support
CTM and RPR
Configuring CTC Circuits for RPR
CTC Circuit Configuration Example for RPR
14-7
14-8
Three-Node RPR Example
14-9
Immediate delayed
Configures a station ID. The user must configure a
Optional Sets the RPR ring wrap mode to either wrap
14-10
Assigning the ML-Series Card POS Ports to the SPR Interface
14-11
14-12
14-13
Example 14-2 SPR Station-ID 2 Configuration
RPR Cisco IOS Configuration Example
Example 14-1 SPR Station-ID 1 Configuration
14-14
CRC Threshold Configuration and Detection
Example 14-3 SPR Station-ID 3 Configuration
14-15
Example 14-4 Example of show interface spr 1 Output
Monitoring and Verifying RPR
14-16
Example 14-5 Example of show run interface spr 1 Output
Add an ML-Series Card into an RPR
14-17
14-18
Three-Node RPR After the Addition
Adding an ML-Series Card into an RPR
14-19
Endpoint of the first newly created circuit
Cisco ONS 15454 Procedure Guide
Enables the port
14-20
Endpoint of the second newly created circuit
Stop. You have completed this procedure
Delete an ML-Series Card from an RPR
14-21
14-22
Three-Node RPR Before the Deletion
Double-click the ML-Series card in Adjacent Node
Deleting an ML-Series Card from an RPR
Log into Adjacent Node 1 with CTC
14-23
14-24
Cisco Proprietary RPR KeepAlive
Configuring Cisco Proprietary RPR KeepAlive
Configuring Shortest Path and Topology Discovery
Cisco Proprietary RPR Shortest Path
Redundant Interconnect is only supported on 454 platforms
Redundant Interconnect
Monitoring and Verifying Shortest Path andTopolgy Discovery
14-26
Configuring Security for the ML-Series Card
Understanding Security
15-1
Secure Shell on the ML-Series Card
Secure Login on the ML-Series Card
Disabling the Console Port on the ML-Series Card
Understanding SSH
Setting Up the ML-Series Card to Run SSH
Configuring SSH
Configuration Guidelines
This section has configuration information
Configuring the SSH Server
15-4
Router config# ip ssh version 1
Displaying the SSH Configuration and Status
Router # configure terminal
Router config# ip ssh timeout
Radius Relay Mode
Radius on the ML-Series Card
15-6
Radius Stand Alone Mode
Configuring Radius Relay Mode
15-7
Configuring Radius
Understanding Radius
15-8
Default Radius Configuration
Identifying the Radius Server Host
15-9
15-10
Router config# aaa new-model Enable AAA
Configuring AAA Login Authentication
Router# configure terminal Enter global configuration mode
Switchconfig# radius-server host host1
Router config# aaa authentication
Router config# line console tty
15-12
Defining AAA Server Groups
Router config# end Return to privileged Exec mode
Router# show running-config Verify your entries
15-13
Router config-sg-radius# end
Router config# aaa group server
Router config-sg-radius# server
Router # show running-config
Radius
15-15
Starting Radius Accounting
15-16
Configuring a nas-ip-address in the Radius Packet
Configuring Settings for All Radius Servers
15-17
Marked as dead, the skipping will not take place
Default is 0 the range is 1 to 1440 minutes
Deadtime minutes
15-18
Send accounting authentication
15-19
Displaying the Radius Configuration
15-20
Configuring Bridging on the ML-Series Card
Understanding Bridging
16-1
Configuring Bridging
16-2
For any statically configured forwarding entries
Monitoring and Verifying Bridging
16-3
To specific bridge groups
Displays detailed information about spanning tree
Bridge-group-number restricts the spanning tree information
Brief displays summary information about spanning tree
Sonet
CE-100T-8 Ethernet Operation
CE-100T-8 Overview
17-1
CE-100T-8 Ethernet Features
Autonegotiation, Flow Control, and Frame Buffering
17-2
Ethernet Link Integrity Support
17-3
Enhanced State Model for Ethernet and Sonet Ports
Ieee 802.1Q CoS and IP ToS Queuing
17-4
17-5
IP ToS Priority Queue Mappings
CoS Priority Queue Mappings
Statistics and Counters
CE-100T-8 Sonet Circuits and Features
Rmon and Snmp Support
17-6
Maximum Number of STS-1-2v Circuits
Ccat High Order Vcat High Order Vcat Low Order
Number of STS-3c Circuits Maximum Number of STS-1 Circuits
17-7
7x=1-12 6x=1-14 5x=1-16 =1-21
CE-100T-8 Maximum Service Densities
CE-100T-8 STS/VT Allocation Tab
17-8
CE-100T-8 Vcat Characteristics
17-9
CE-100T-8 POS Encapsulation, Framing, and CRC
17-10
CE-100T-8 Loopback, J1 Path Trace, and Sonet Alarms
17-11
17-12
Command Reference for the ML-Series Card
Ieee
Related Commands bridge-group
Drpri-rstp
Rstp
Related Commands show interface
Clear counters
Router# clear counters
Clock summertime
Syntax Description Defaults Command Modes Usage Guidelines
No clock auto
Clock timezone
Defaults Command Modes
Interface spr
No pos mode gfp fcs-disabled
Related Commands shutdown
MLSeriesconfig-if # pos mode gfp fcs-disable
No pos pdi holdoff time
No pos report alarm
Related Commands
Pos trigger defects
Syntax Description Defaults
Related Commands pos trigger delay
Non pos trigger defects condition
Default value is 200 milliseconds
No pos trigger delay time
Time Delay time in milliseconds, 200 to
Command is 50 milliseconds
Parameter Description
No pos vcat defect immediate delayed
Delayed
Immediate
Show controller pos interface-numberdetails
MLSeries# show controller pos 0 Interface POS0
Related Commands show interface pos Clear counters
Use this command to display the status of the POS interface
Related Commands show controller pos Clear counters
Show interface pos interface-number
Show ons alarm
MLSeries# show ons alarm
78-18133-01
Eqpt
Sts
Vcg
Related Commands show controller pos Show ons alarm failures
MLSeries# show ons alarm defect sts
MLSeries# show ons alarm failure eqpt
ML-Series#show ons alarm failure port
MLSeries# show ons alarm failure sts
Assigns the POS interface to the SPR interface
Interface spr Spr station-id Spr wrap
Auto
Related Commands interface spr
No spr load-balance auto port-based
Port-based
Following example sets an ML-Series card SPR station ID to
Configures a station ID
DefaultsN/A
Spr-intf-id Spr wrap
Spr wrap immediate delayed
Wraps RPR traffic after the carrier delay time expires
Interface spr Spr-intf-id Spr station-id
Unsupported CLI Commands for the ML-Series Card
Unsupported Privileged Exec Commands
Unsupported Global Configuration Commands
Page
Unsupported POS Interface Configuration Commands
Unsupported FastEthernet Interface Configuration Commands
Unsupported Port-Channel Interface Configuration Commands
Unsupported BVI Interface Configuration Commands
Rate-limit Random-detect Timeout Tx-ring-limit
Using Technical Support
Gathering Information About Your Internetwork
Getting the Data from Your ML-Series Card
Providing Data to Your Technical Support Representative
Page
IN-5
IS,AINS
IN-6
IN-7
SSH
RPR
Rstp SDM
CRC
Rstp STP
IN-9
See also framing
GFP-F
IN-10
Lcas
IN-11
POS
RPR SDM
IN-12
IN-13
Rmon
Rstp
IN-14
Snmp
See also Bpdu
IN-15
Tcam
Vcat
IN-16
SDM STP and Rstp status
Configuring as Layer 2 tunnel Configuring Ieee 802.1Q
Customer numbering in service-provider
VTP Layer 2 protocol tunneling Vty
IN-18