Common Data Security Architecture (CDSA) White Paper
Validating the CSP Credentials
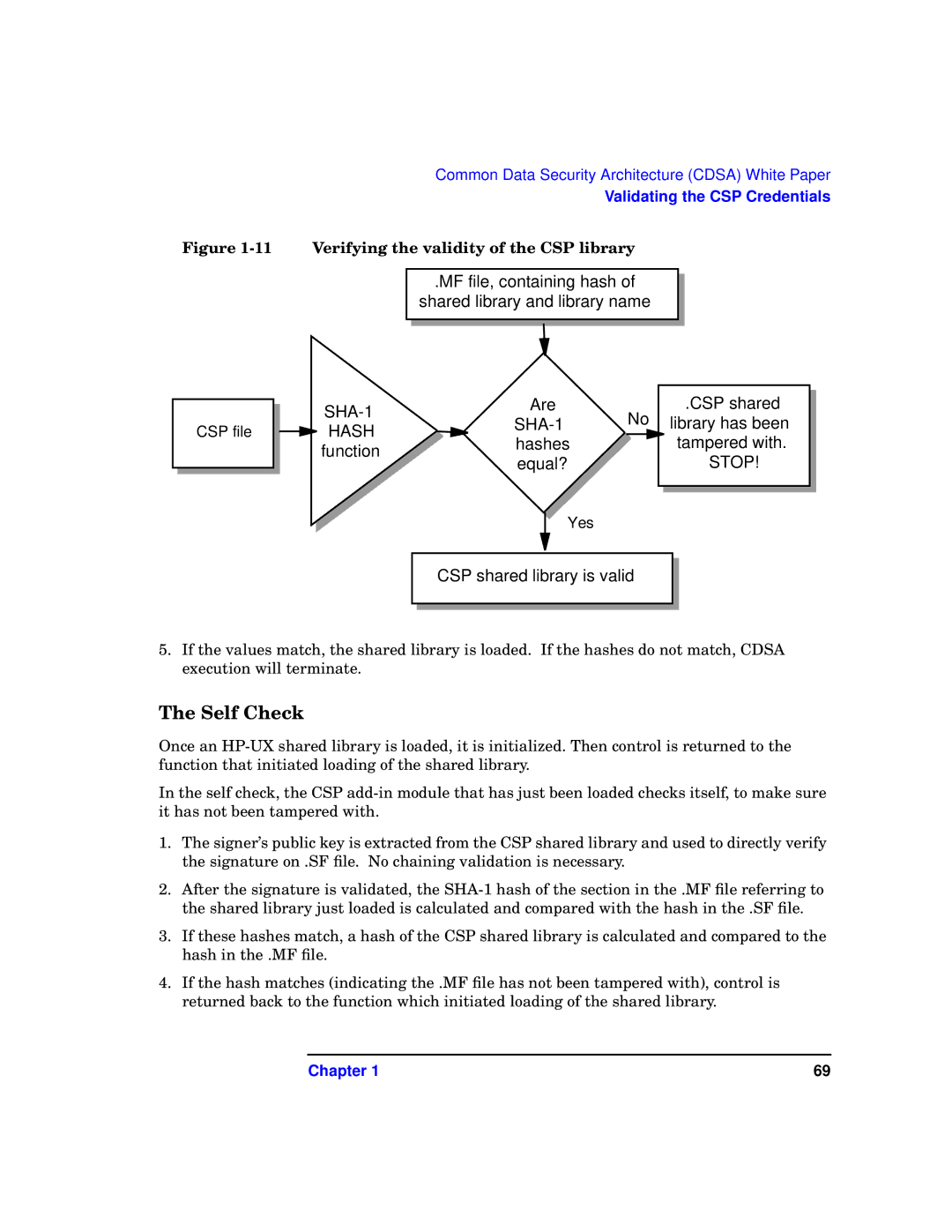
Figure 1-11 Verifying the validity of the CSP library
.MF file, containing hash of
shared library and library name
CSP file
| Are | .CSP shared | |
| No library has been | ||
HASH | |||
hashes | tampered with. | ||
function | |||
equal? | STOP! | ||
|
Yes
CSP shared library is valid
5.If the values match, the shared library is loaded. If the hashes do not match, CDSA execution will terminate.
The Self Check
Once an
In the self check, the CSP
1.The signer’s public key is extracted from the CSP shared library and used to directly verify the signature on .SF file. No chaining validation is necessary.
2.After the signature is validated, the
3.If these hashes match, a hash of the CSP shared library is calculated and compared to the hash in the .MF file.
4.If the hash matches (indicating the .MF file has not been tampered with), control is returned back to the function which initiated loading of the shared library.
Chapter 1 | 69 |