Common Data Security Architecture (CDSA) White Paper
Validating the CSP Credentials
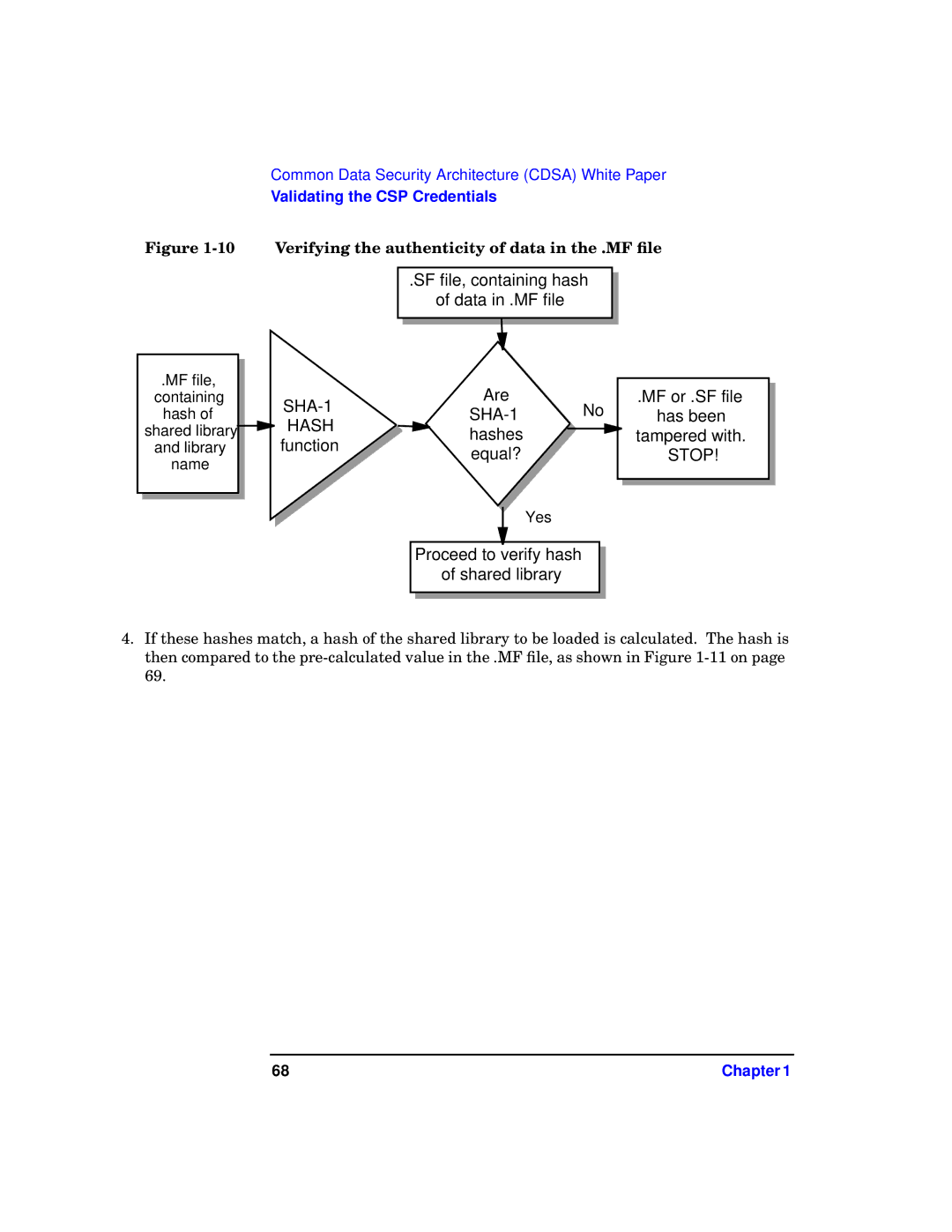
Figure 1-10 Verifying the authenticity of data in the .MF file
.SF file, containing hash of data in .MF file
.MF file, containing hash of shared library and library name
| Are | No |
HASH | hashes |
|
function |
| |
equal? |
| |
|
| |
| Yes |
|
| Proceed to verify hash |
|
| of shared library |
|
.MF or .SF file has been tampered with. STOP!
4.If these hashes match, a hash of the shared library to be loaded is calculated. The hash is then compared to the
68 | Chapter 1 |