Common Data Security Architecture (CDSA) White Paper
Validating the CSP Credentials
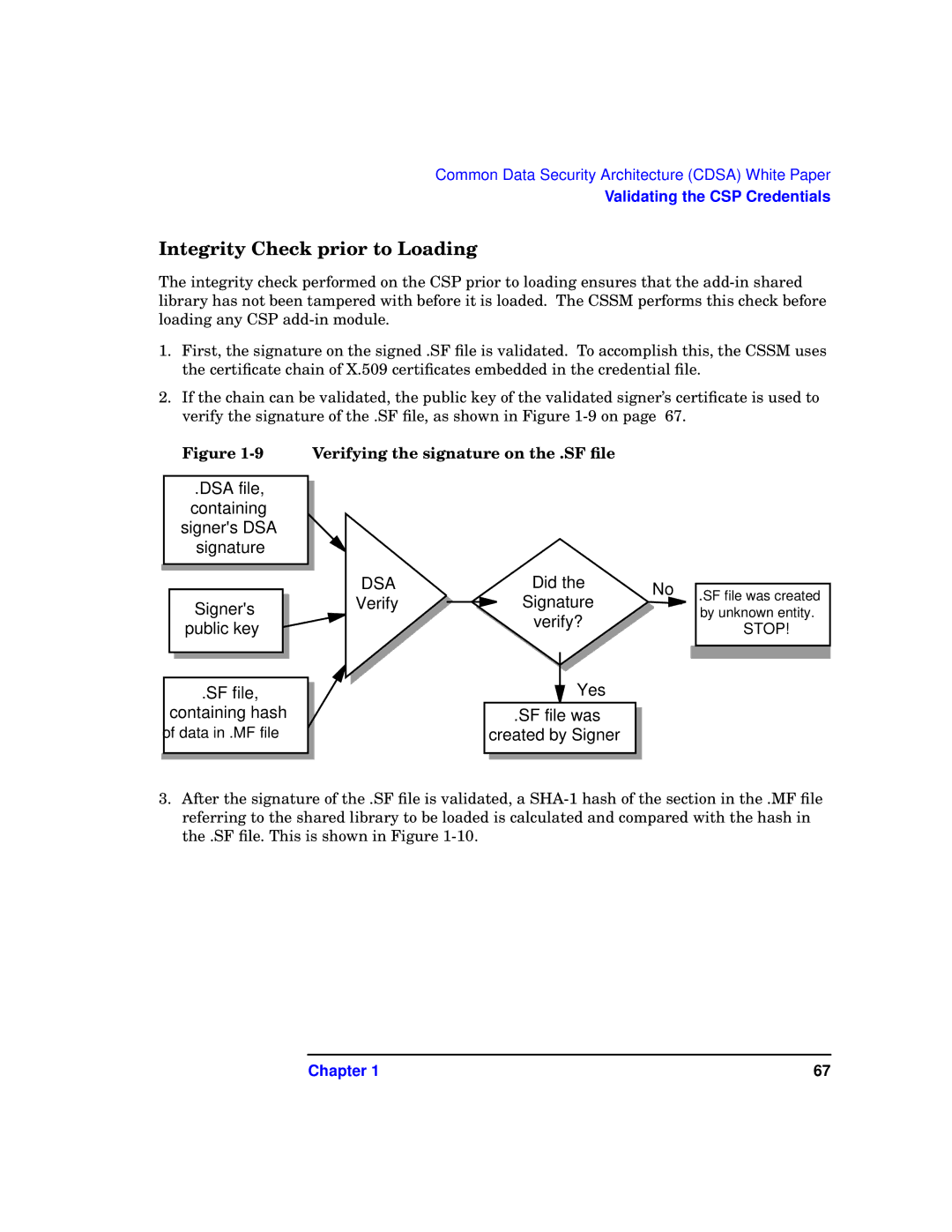
Integrity Check prior to Loading
The integrity check performed on the CSP prior to loading ensures that the
1.First, the signature on the signed .SF file is validated. To accomplish this, the CSSM uses the certificate chain of X.509 certificates embedded in the credential file.
2.If the chain can be validated, the public key of the validated signer’s certificate is used to verify the signature of the .SF file, as shown in Figure
Figure
.DSA file, containing signer's DSA signature
Verifying the signature on the .SF file
Signer's public key
.SF file, containing hash
of data in .MF file
DSA | Did the | No | |
Verify | Signature | ||
| |||
| verify? |
| |
| Yes |
| |
| .SF file was |
| |
| created by Signer |
|
.SF file was created by unknown entity.
STOP!
3.After the signature of the .SF file is validated, a
Chapter 1 | 67 |