Common Data Security Architecture (CDSA) White Paper
Cryptography Service Provider (CSP) API
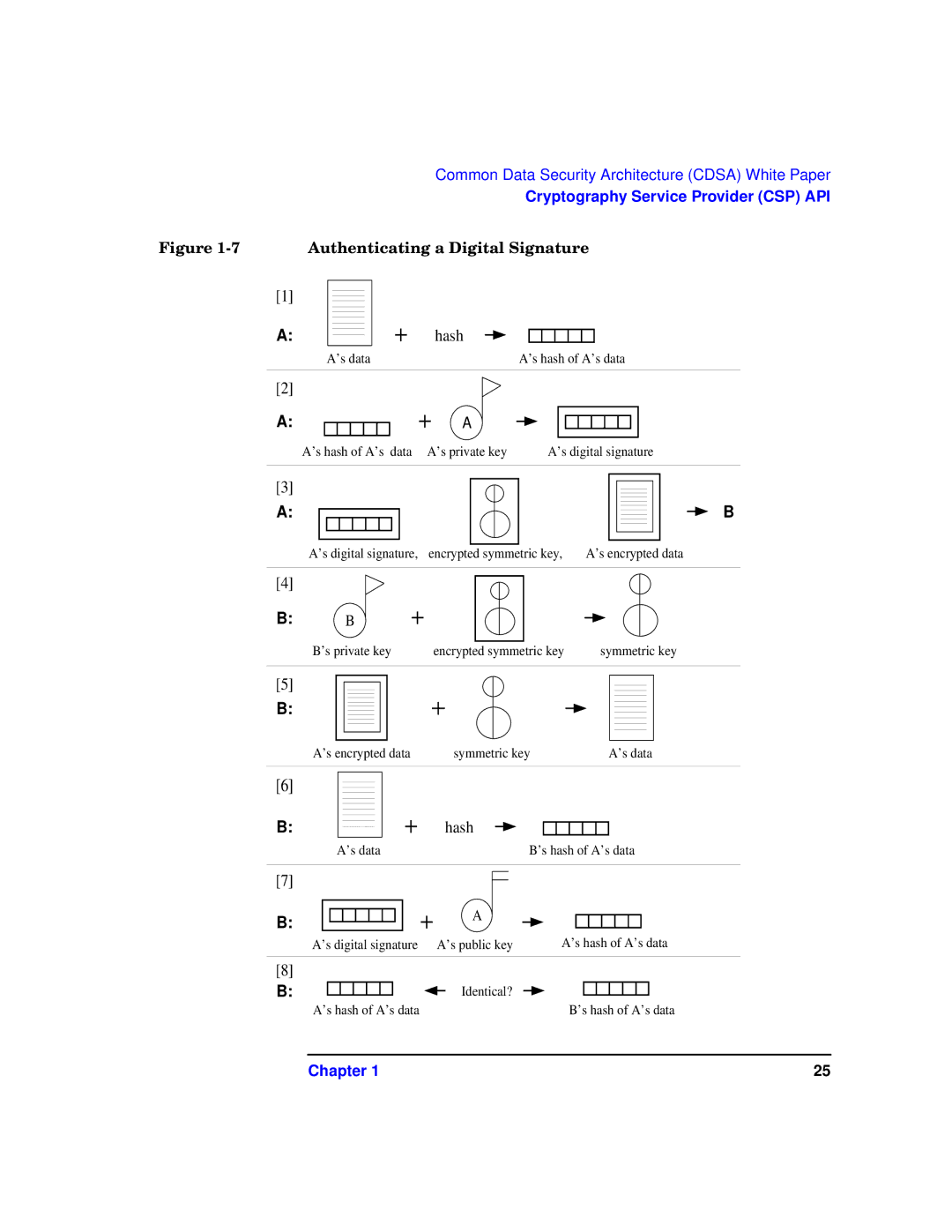
Figure | Authenticating a Digital Signature |
[1]
A:
A's data
hash
A's hash of A's data
[2]
A:
A
A's hash of A's data A's private key | A's digital signature |
|
|
[3]
A:
B
A's digital signature, encrypted symmetric key, | A's encrypted data |
|
|
[4]
B: B
B's private key | encrypted symmetric key | symmetric key |
|
|
|
[5]
B:
A's encrypted data | symmetric key | A's data |
|
|
|
[6]
B:
A's data
hash
B's hash of A's data
[7]
B:
A's digital signature
A
A's public key | A's hash of A's data |
[8]
B: |
|
|
|
|
|
|
| Identical? |
|
|
|
|
|
|
|
|
|
| |||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ||
A's hash of A's data |
|
|
| B's hash of A's data | ||||||||||||
Chapter 1 | 25 |