Reference Manual for the ADSL Modem Router DG834 v3
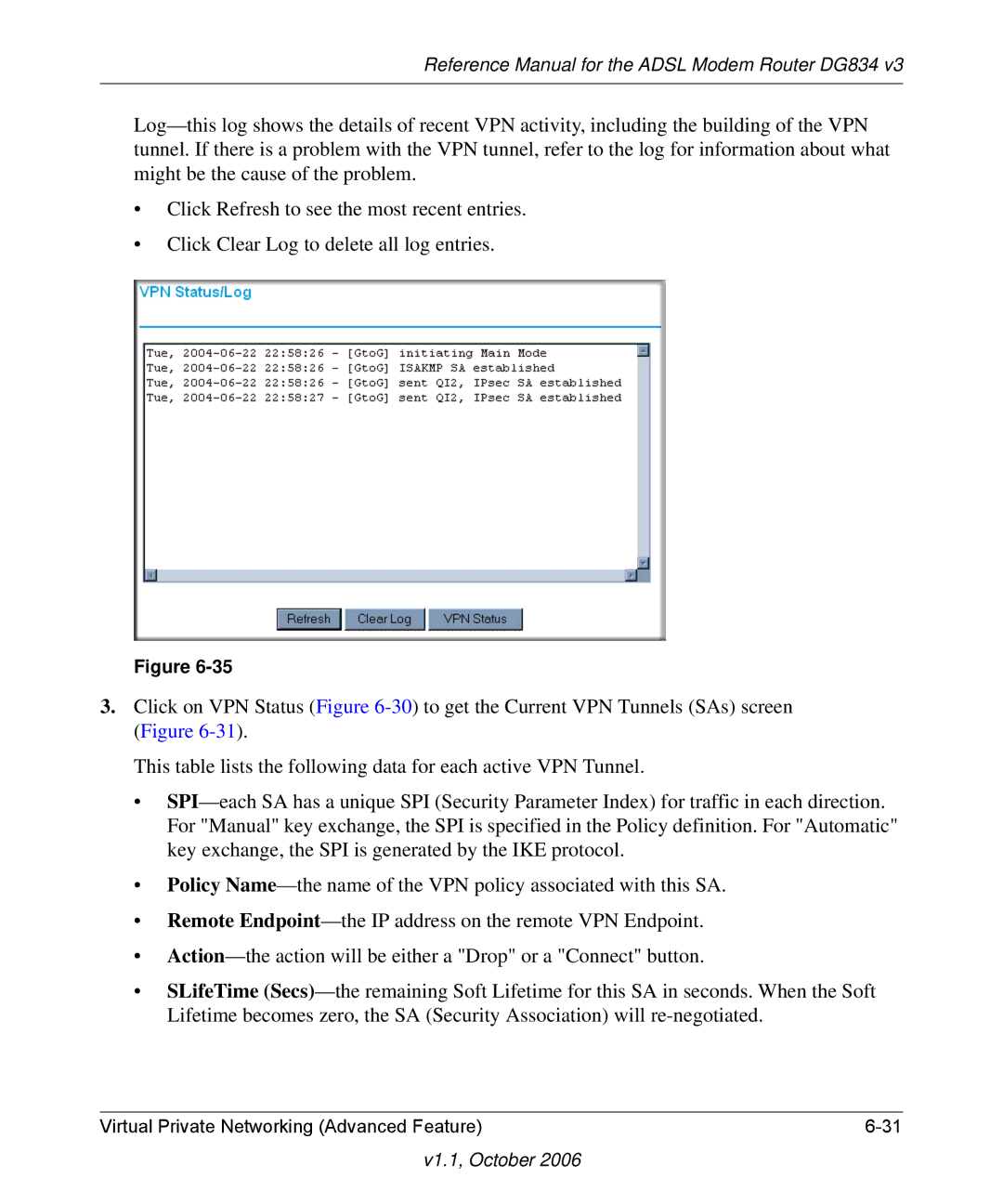
Log—this log shows the details of recent VPN activity, including the building of the VPN tunnel. If there is a problem with the VPN tunnel, refer to the log for information about what might be the cause of the problem.
•Click Refresh to see the most recent entries.
•Click Clear Log to delete all log entries.
Figure 6-35
3.Click on VPN Status (Figure 6-30) to get the Current VPN Tunnels (SAs) screen (Figure 6-31).
This table lists the following data for each active VPN Tunnel.
•SPI—each SA has a unique SPI (Security Parameter Index) for traffic in each direction. For "Manual" key exchange, the SPI is specified in the Policy definition. For "Automatic" key exchange, the SPI is generated by the IKE protocol.
•Policy Name—the name of the VPN policy associated with this SA.
•Remote Endpoint—the IP address on the remote VPN Endpoint.
•Action—the action will be either a "Drop" or a "Connect" button.
•SLifeTime (Secs)—the remaining Soft Lifetime for this SA in seconds. When the Soft Lifetime becomes zero, the SA (Security Association) will re-negotiated.
Virtual Private Networking (Advanced Feature) | 6-31 |
v1.1, October 2006