i n t e l l i g e n t | w i r e l e s s | p l a t f o r m |
|
|
|
|
|
| Figure: |
|
|
| Table |
|
|
|
|
| Page Items |
| Descriptions |
|
|
| |
|
|
| automatically changed (called rekeying) and authenticated between |
|
|
| devices after a specified period of time, or after a specified number of |
|
|
| packets has been transmitted. |
|
|
| |
|
|
| |
|
|
| the home/SOHO user for two reasons. The process used to generate the |
|
|
| encryption key is very rigorous and the rekeying (or key changing) is |
|
|
| done very quickly. This stops even the most determined hacker from |
|
|
| gathering enough data to break the encryption. |
|
|
| This is used by the clients to become authenticated with the Root |
|
| Bridge/Remote Router/Remote NAT. | |
|
|
|
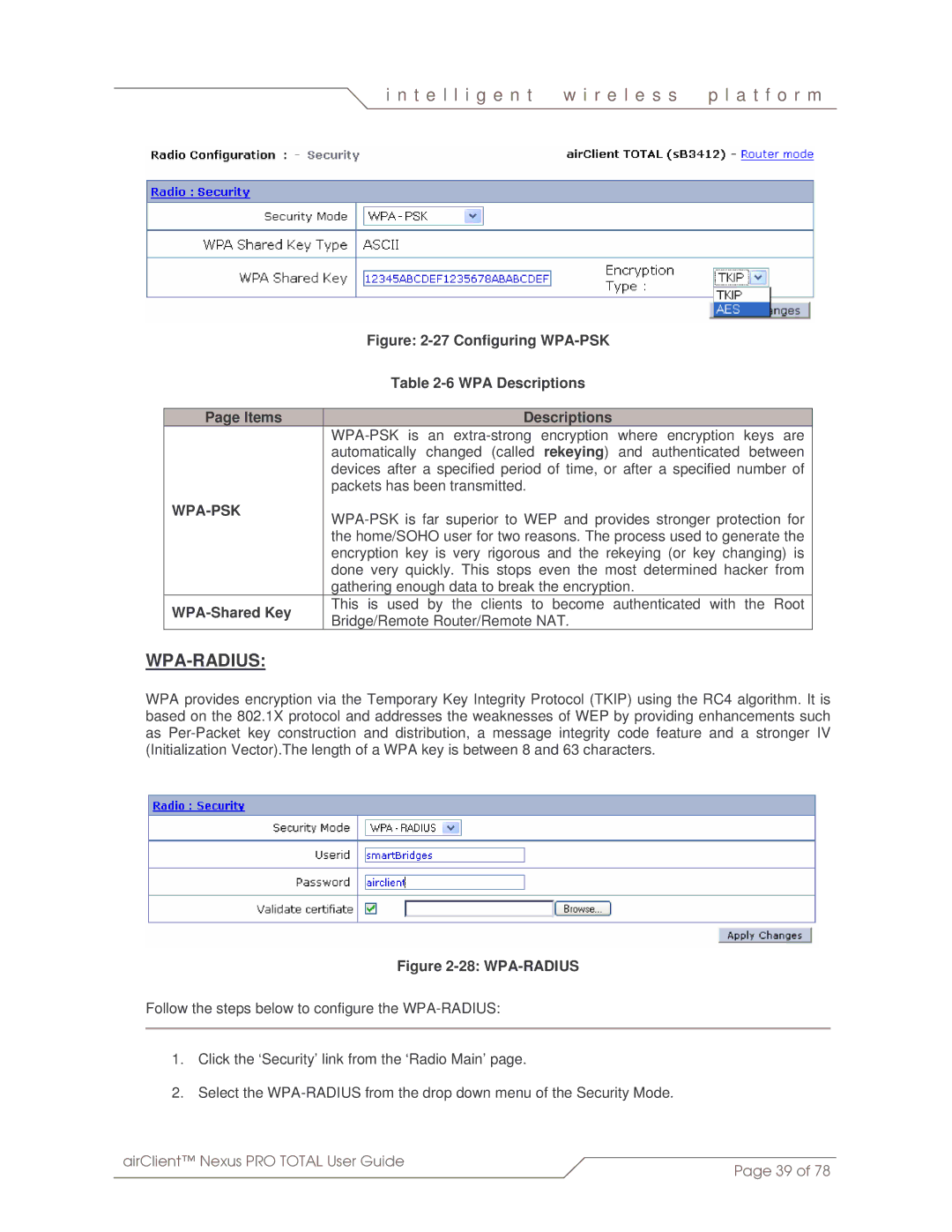
WPA-RADIUS:
WPA provides encryption via the Temporary Key Integrity Protocol (TKIP) using the RC4 algorithm. It is based on the 802.1X protocol and addresses the weaknesses of WEP by providing enhancements such as
Figure 2-28: WPA-RADIUS
Follow the steps below to configure the
1.Click the ‘Security’ link from the ‘Radio Main’ page.
2.Select the
airClient™ Nexus PRO TOTAL User Guide | Page 39 of 78 |
|