7.9.5 PPTP/L2TP Server
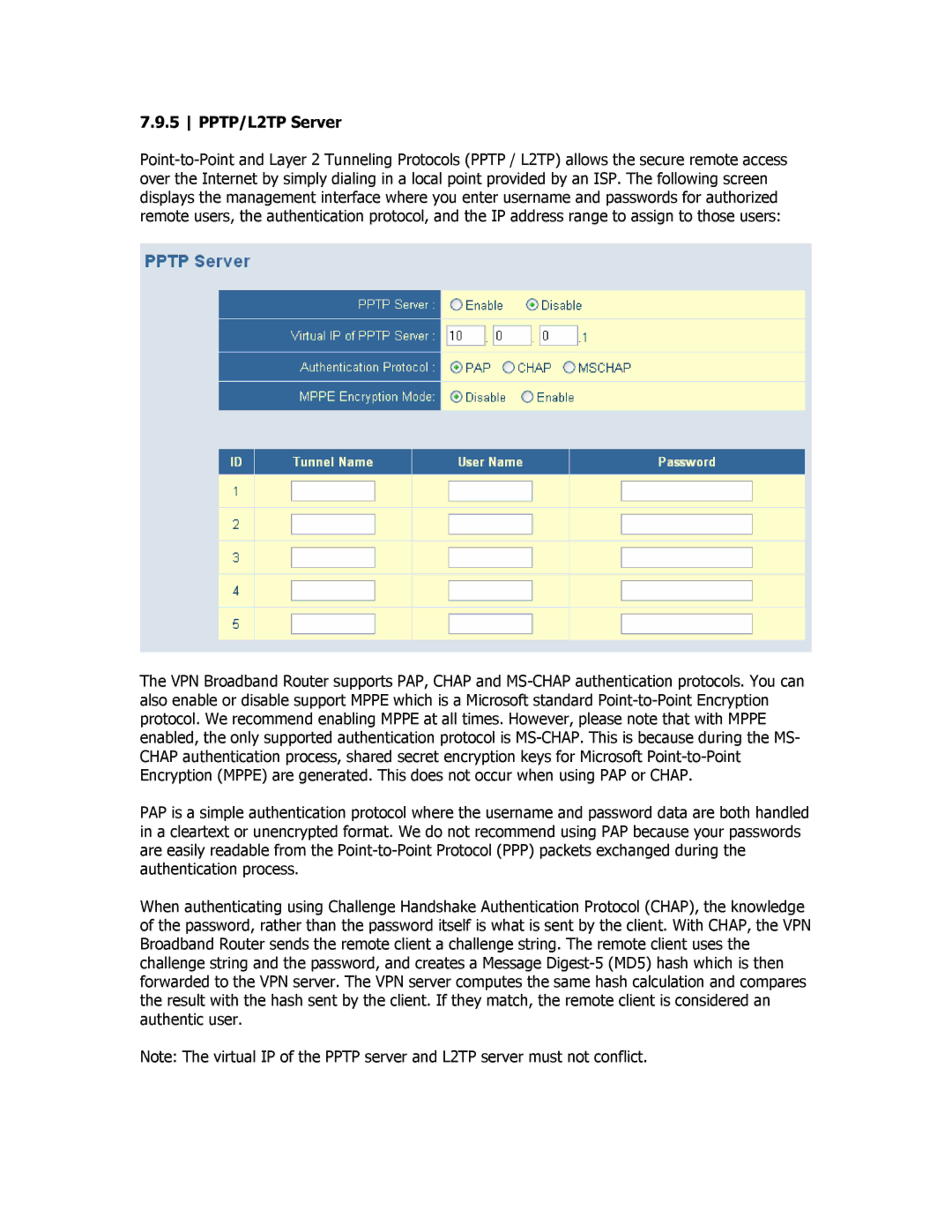
Point-to-Point and Layer 2 Tunneling Protocols (PPTP / L2TP) allows the secure remote access over the Internet by simply dialing in a local point provided by an ISP. The following screen displays the management interface where you enter username and passwords for authorized remote users, the authentication protocol, and the IP address range to assign to those users:
The VPN Broadband Router supports PAP, CHAP and MS-CHAP authentication protocols. You can also enable or disable support MPPE which is a Microsoft standard Point-to-Point Encryption protocol. We recommend enabling MPPE at all times. However, please note that with MPPE enabled, the only supported authentication protocol is MS-CHAP. This is because during the MS- CHAP authentication process, shared secret encryption keys for Microsoft Point-to-Point Encryption (MPPE) are generated. This does not occur when using PAP or CHAP.
PAP is a simple authentication protocol where the username and password data are both handled in a cleartext or unencrypted format. We do not recommend using PAP because your passwords are easily readable from the Point-to-Point Protocol (PPP) packets exchanged during the authentication process.
When authenticating using Challenge Handshake Authentication Protocol (CHAP), the knowledge of the password, rather than the password itself is what is sent by the client. With CHAP, the VPN Broadband Router sends the remote client a challenge string. The remote client uses the challenge string and the password, and creates a Message Digest-5 (MD5) hash which is then forwarded to the VPN server. The VPN server computes the same hash calculation and compares the result with the hash sent by the client. If they match, the remote client is considered an authentic user.
Note: The virtual IP of the PPTP server and L2TP server must not conflict.