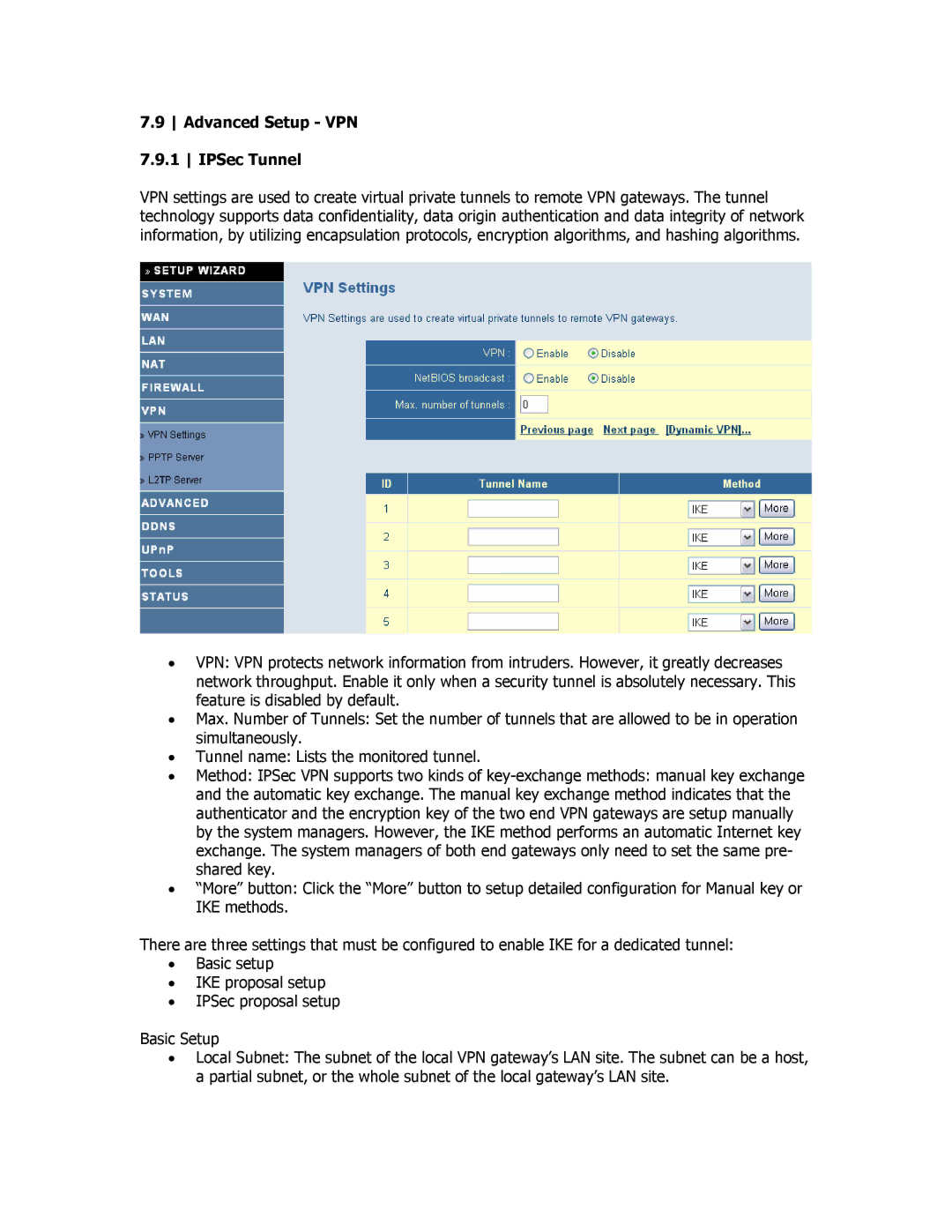
7.9 Advanced Setup - VPN 7.9.1 IPSec Tunnel
VPN settings are used to create virtual private tunnels to remote VPN gateways. The tunnel technology supports data confidentiality, data origin authentication and data integrity of network information, by utilizing encapsulation protocols, encryption algorithms, and hashing algorithms.
•VPN: VPN protects network information from intruders. However, it greatly decreases network throughput. Enable it only when a security tunnel is absolutely necessary. This feature is disabled by default.
•Max. Number of Tunnels: Set the number of tunnels that are allowed to be in operation simultaneously.
•Tunnel name: Lists the monitored tunnel.
•Method: IPSec VPN supports two kinds of
•“More” button: Click the “More” button to setup detailed configuration for Manual key or IKE methods.
There are three settings that must be configured to enable IKE for a dedicated tunnel:
•Basic setup
•IKE proposal setup
•IPSec proposal setup
Basic Setup
•Local Subnet: The subnet of the local VPN gateway’s LAN site. The subnet can be a host, a partial subnet, or the whole subnet of the local gateway’s LAN site.