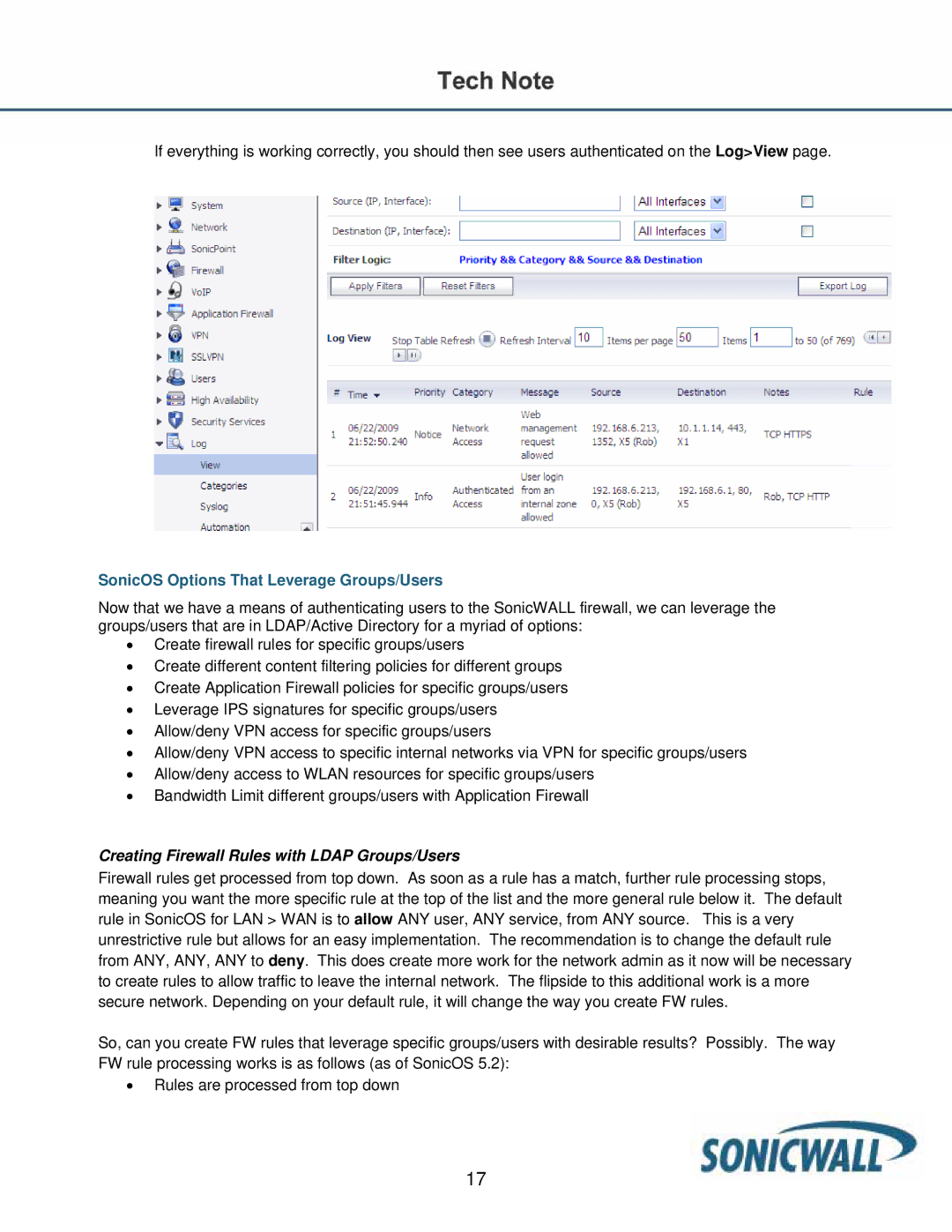
If everything is working correctly, you should then see users authenticated on the Log>View page.
SonicOS Options That Leverage Groups/Users
Now that we have a means of authenticating users to the SonicWALL firewall, we can leverage the groups/users that are in LDAP/Active Directory for a myriad of options:
•Create firewall rules for specific groups/users
•Create different content filtering policies for different groups
•Create Application Firewall policies for specific groups/users
•Leverage IPS signatures for specific groups/users
•Allow/deny VPN access for specific groups/users
•Allow/deny VPN access to specific internal networks via VPN for specific groups/users
•Allow/deny access to WLAN resources for specific groups/users
•Bandwidth Limit different groups/users with Application Firewall
Creating Firewall Rules with LDAP Groups/Users
Firewall rules get processed from top down. As soon as a rule has a match, further rule processing stops, meaning you want the more specific rule at the top of the list and the more general rule below it. The default rule in SonicOS for LAN > WAN is to allow ANY user, ANY service, from ANY source. This is a very unrestrictive rule but allows for an easy implementation. The recommendation is to change the default rule from ANY, ANY, ANY to deny. This does create more work for the network admin as it now will be necessary to create rules to allow traffic to leave the internal network. The flipside to this additional work is a more secure network. Depending on your default rule, it will change the way you create FW rules.
So, can you create FW rules that leverage specific groups/users with desirable results? Possibly. The way FW rule processing works is as follows (as of SonicOS 5.2):
•Rules are processed from top down
17