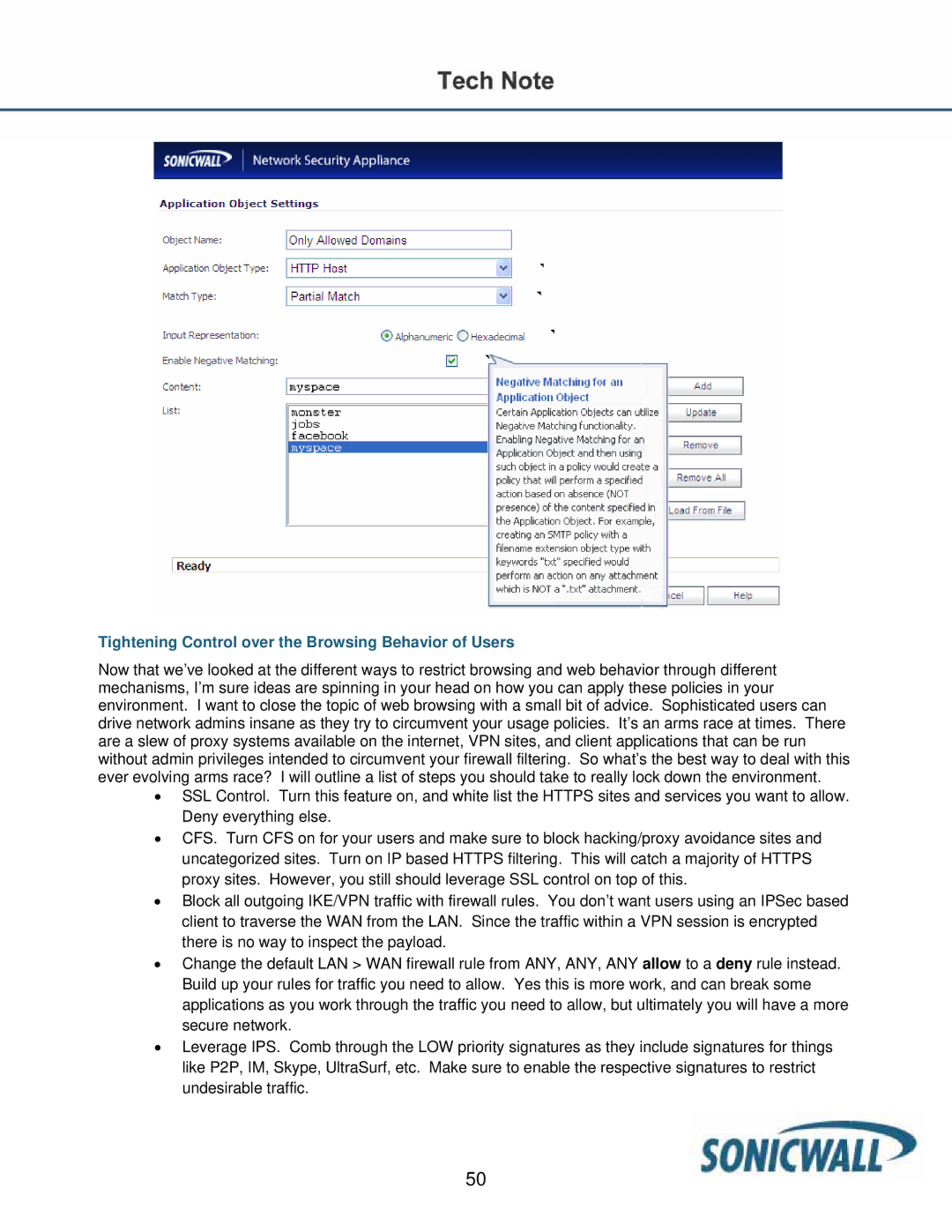
Tightening Control over the Browsing Behavior of Users
Now that we’ve looked at the different ways to restrict browsing and web behavior through different mechanisms, I’m sure ideas are spinning in your head on how you can apply these policies in your environment. I want to close the topic of web browsing with a small bit of advice. Sophisticated users can drive network admins insane as they try to circumvent your usage policies. It’s an arms race at times. There are a slew of proxy systems available on the internet, VPN sites, and client applications that can be run without admin privileges intended to circumvent your firewall filtering. So what’s the best way to deal with this ever evolving arms race? I will outline a list of steps you should take to really lock down the environment.
•SSL Control. Turn this feature on, and white list the HTTPS sites and services you want to allow. Deny everything else.
•CFS. Turn CFS on for your users and make sure to block hacking/proxy avoidance sites and uncategorized sites. Turn on IP based HTTPS filtering. This will catch a majority of HTTPS proxy sites. However, you still should leverage SSL control on top of this.
•Block all outgoing IKE/VPN traffic with firewall rules. You don’t want users using an IPSec based client to traverse the WAN from the LAN. Since the traffic within a VPN session is encrypted there is no way to inspect the payload.
•Change the default LAN > WAN firewall rule from ANY, ANY, ANY allow to a deny rule instead. Build up your rules for traffic you need to allow. Yes this is more work, and can break some applications as you work through the traffic you need to allow, but ultimately you will have a more secure network.
•Leverage IPS. Comb through the LOW priority signatures as they include signatures for things like P2P, IM, Skype, UltraSurf, etc. Make sure to enable the respective signatures to restrict undesirable traffic.
50