Edition
Manufacturing Part Number T1417-90009 E0905
Legal Notices
Copyright Notices
Page
Page
Contents
Configuring the Kerberos Server with Ldap
Administering the Kerberos Server
Contents
Contents
Propagating the Kerberos Server
Managing Multiple Realms
Contents
Tables
Table A-2. Configuration Worksheet Explanation
Figures
Figures
What Is in This Document
Intended Audience
Interoperability with Windows 2000, on
Glossary
Typographic Conventions
Index
Bold fixed
Width
Publishing History
HP-UX Release Name and Release Identifier
Related Software Products
Related Documentation
Accessing the World Wide Web
Related Request for Comments RFCs
HP Encourages Your Comments
Overview
Overview
Introduction
How the Kerberos Server Works
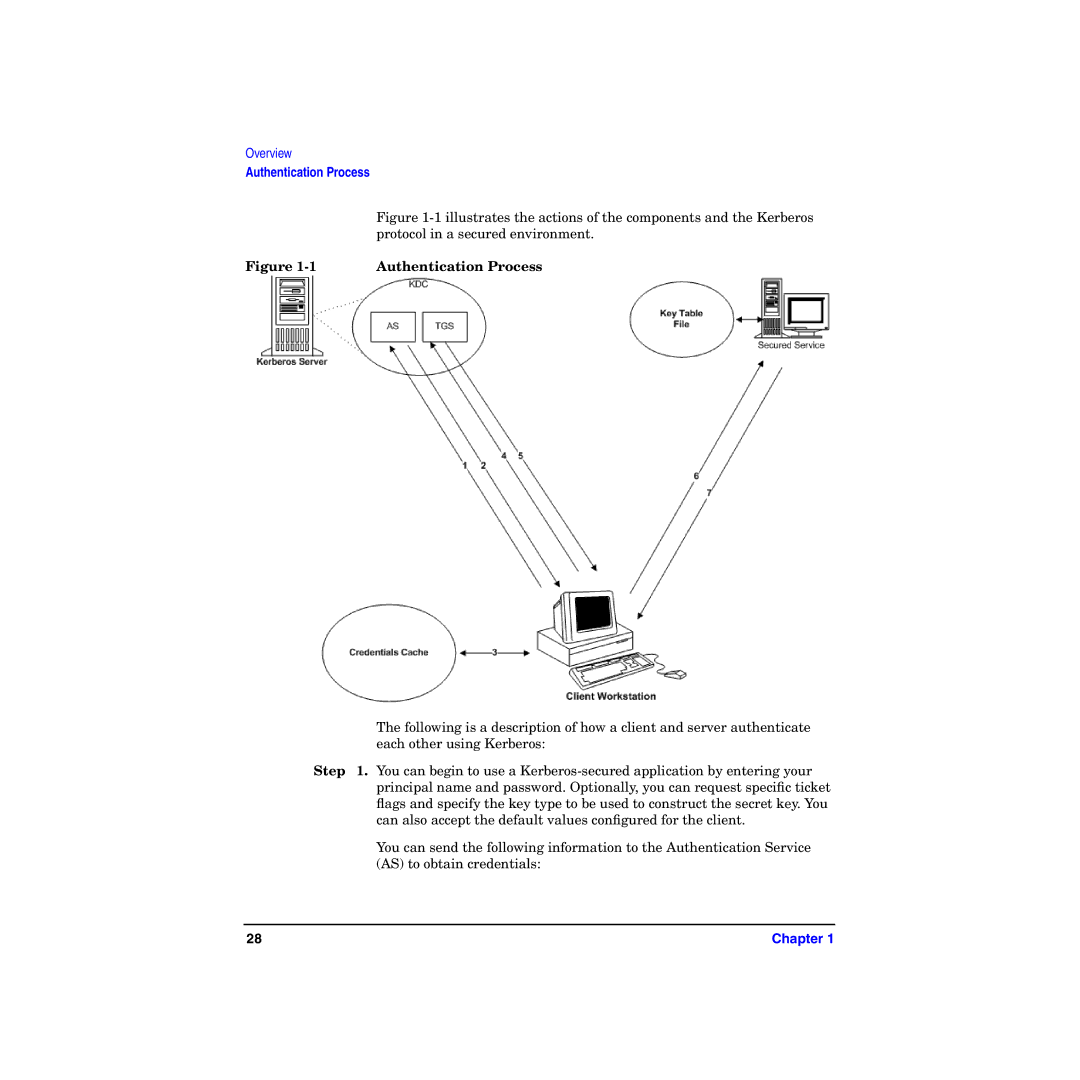
Authentication Process
Authentication Process
Illustrates the actions of the components and the Kerberos
Step
Authentication Process
DES Versus 3DES Key Type Settings
Introduction to Ldap
Ldap Advantages
Integrating Kerberos Server v3.1 with Ldap
Integrating a Kerberos Principal in to the Ldap Directory
Installing the Kerberos Server
Installing the Kerberos Server
Prerequisites
System Requirements
Hardware Requirements
Software Requirements
Version Compatibility
Installing the Server
Installing the Server Chapter
Migrating to a Newer Version
Migrating to a Newer Version of the Kerberos Server
Migrating from Kerberos Server Version 1.0 to
Copy the dump file to the new system where you are installing
Upon success, the following message appears
Migrating from Kerberos Server Version 1.0 to
Migrating from Kerberos Server Version 2.0 to
Version
Copy the dump file to the system on which you are installing
Migrating from Kerberos Server Version 3.0 to Version
Migrating to a Newer Version of the Kerberos Server
Interoperability with Windows
Interoperability with Windows
Understanding the Terminology
Table of Analogous Terms Kerberos Server Windows
Kerberos Server and Windows 2000 Interoperability
Scenario
Establishing Trust Between Kerberos Server and Windows
Fqdn qualifier specifies the fully qualified domain name
Single Realm Domain Authentication
Interrealm Interdomain Authentication
Special Considerations for Interoperability
Database Considerations
Encryption Considerations
Postdated Tickets
Special Considerations for Interoperability Chapter
Special Considerations for Interoperability Chapter
Configuring the Kerberos
Security Server Files That Require Configuration
Configuration Files for the Kerberos Server
Configuration File Function
Krb.conf File
Krb.conf File Format
Krb.realms File
Krb.realms File Format
Wildcard Characters
Wildcard Character Description
Autoconfiguring the Kerberos Server
To configure the server, select option
Configuring the Kerberos Server with C-Tree
Value, DES-MD5, is selected
Server with Ldap
Configuration Files for Ldap Integration
Krb5ldap.conf File
Ldap Configuration Files
File Function
Krb5ldap.conf File Format
Parameter Description
This line indicates a space
Krb5schema.conf File
Krb5schema.conf File Format
Ticket’ Syntax
Configuration Files for Ldap Integration
Krb5map.conf File
Krb5map.conf File Format
HpKrbAuthzData HpKrbKeyVersion HpKrbKeyData
Planning Your Ldap Configuration
Before You Begin
Setting up Your Ldap Configuration
For example, ou=people, o=bambi.com
For example, ou=accounts, ou=people, o=bambi.com
For example, uid. cn, homedirectory, gidnumber, uidnumber
Configuring the Kerberos Server with Ldap
Autoconfiguring the Kerberos Server With Ldap Integration
Step Select one of the following options
Qualified host name or the IP address
HpKrbKey
Autoconfiguring the Kerberos Server With Ldap Integration
Manually Configuring the Kerberos Server with Ldap
Editing the Configuration Files
Manually Configuring the Kerberos Server with Ldap
Manually Configuring the Kerberos Server with Ldap Chapter
Configuring the Primary
Create the Principal Database After Installation
Configuring the Primary Security Server
To add an Administrative Principal Using the HP Kerberos
Add an Administrative Principal
Administrator
To Add an Administrative Principal Through the Command Line
Start the Kerberos Daemons
Define Secondary Security Server Network Locations
Adminaclfile
Password Policy File
Security Policies
Starting the Security Server
Creating the Principal Database
Configuring the Secondary Security Servers with C-Tree
Copying the Kerberos Configuration File
Creating a host/fqdn Principal and Extracting the Key
Creating a stash file using the kdbstash utility
Configuring the Secondary Security Servers with Ldap
106
Using Indexes to Improve Database Performance
108
Administering the Kerberos
110
Administering the Kerberos Database
Configuration Files Required for kadmind
Kadmind Command
File Name Description
Adminaclfile File
Assigning Administrative Permissions
Chapter 115
Adding Entries to adminaclfile
Using Restricted Administrator
Creating Administrative Accounts
How the r/R Modifiers Work
118
Password Policy File
Editing the Default File
Default Password Policy Settings for the Base Group
Password Policy Setting Default Value
120
Principals
122
Adding New Service Principals
Adding User Principals
Reserved Service Principals
Chapter 125
126
Removing Special Privilege Settings
Removing User Principals
Removing Service Principals
Protecting a Secret Key
Chapter 129
Kadmin and kadminl Utilities
Administration Utilities
Administration Utilities Name Description
HP Kerberos Administrator
Standard Functionality of the Administrator
Function of OK, Apply, and Cancel Buttons
Cancel
Button Name Action
Local Administrator kadminlui
Using kadminlui
Chapter 135
Principals Tab
Principals Tab
Principals Tab Components
Component Name Description List All
Search String
Search
List of Principals
Principal Information Window
General Tab Principal Information Window
Principal Information Window Components
Password Tab
Field Name Description
General Tab
Attributes Tab
General Tab Components
Field Name Description Principal Expiration
Maximum Ticket Lifetime
Maximum Renew Time
Last Modified
Field Name Description Password Policy
Modified By
Adding Principals to the Database
Change Password Window
Adding Multiple Principals with Similar Settings
Creating an Administrative Principal
Administering the Kerberos Server
148
Search Criteria
Searching for a Principal
Character Description
150
Deleting a Principal
Loading Default Values for a Principal
Restoring Previously Saved Values for a Principal
Changing Ticket Information
Rules for Setting Maximum Ticket Lifetime
Rules for Setting Maximum Renew Time
Chapter 157
Changing Password Information
Chapter 159
Password Tab Principal Information
Password Tab Components
Window
Displays the Ldap DN that you are editing
Component Name Description Password
Password Last
Change Password
Expiration/Date
Change Password Window Password Tab
Entering a password
Change Password Window Components
Components Description New Password
Verification
Changing a DES-CRC or DES-MD5 Principal Key Type
Changing a Key Type
To 3DES
166
Changing Principal Attributes
12 describes the components of the Attributes tab
Attributes Tab Principal Information
Attributes Tab Components
Components Description
Allow Postdated
Allow Renewable
Tickets
170
Components Description Allow Forwardable
Allow Proxy
Allow Duplicate
Session Keys
Preauthentication
Require Password
Components Description Require
Change
Allow As Service
Components Description Lock Principal
Authentication
Set As Password
Change Service
Components Description Require Initial
Ldap Attributes Tab Prinicpal Information Window
176
Deleting a Service Principal
Extracting Service Keys
Chapter 179
Extracting a Service Key Table
Extract Service Key Table Components
Service Key
Component Description Principal
Table Type
Using Groups to Control Settings
Editing the Default Group
Chapter 183
Group Information Window Principal
Group Information Window Components
InformationEditEdit Default Group to display the Group
Component Description Group
Setting the Default Group Principal Attributes
Default Principal Attributes
Principal Attributes
Component Description
Chapter 187
Setting Administrative Permissions
Administrative Permissions
11 Administrative Permissions Window
Add Principals
Principals
Modify
Principals Inquire about
Override the Principal InformationEditEdit Group Default
Defaults
InformationEditEdit Default GroupGroup Information
Component Description Restricted
192
Realms Tab
Realms Tab
Realms Tab Components
Realm Information Window
Realm Information Window Components
Adding a Realm
Deleting a Realm
Remote Administrator kadminui
Logon screen displays as shown in Figure
Logon Screen
200
Chapter 201
Manual Administration Using kadmin
Chapter 203
Adding a New Principal
Specifying a New Password
Adding a Random Key
Changing Password to a New Randomly Generated
Deleting a Principal
Extracting a Principal
3DES
Listing the Attributes of a Principal
Modifying a Principal
Number of Authentication Failures fcnt
Key Version Number Attribute
Attributes
Policy Name
Allow Postdated Attribute
Allow Renewable Attribute
Allow Forwardable Attribute
Allow Proxy Attribute
Allow Duplicate Session Key Attribute
Require Preauthentication Attribute
Require Password Change Attribute
Lock Principal Attribute
Allow As Service Attribute
Require Initial Authentication Attribute
Principal InformationEditEdit Administrative Permissions
Authentication Set As Password Change Service Attribute
Authentication Select Require Initial
No text shows
Password Expiration Attribute
Principal Expiration Attribute
Maximum Ticket Lifetime Attribute
Key Type Attribute
Maximum Renew Time Attribute
Salt Type Attribute
Principal Database Utilities
Principal Database Utilities
Utility Task
Kerberos Database Utilities
226
Database Encryption
Database Master Password
Destroying the Kerberos Database
230
Dumping the Kerberos Database
Loading the Kerberos Database
Stashing the Master Key
234
Starting and Stopping Daemons and Services Situation
Starting and Stopping Daemons
Maintenance Tasks
Master Password
Protecting Security Server Secrets
Host/fqdn@REALM
Backing Up primary security server Data
Backing Up the Principal Database
238
Removing Unused Space from the Database
240
Propagating the Kerberos
242
Propagation Hierarchy
Propagation Relationships
Extracting a Key to the Service Key Table File
Service Key Table
Maintaining Secret Keys in the Key Table File
Creating a New Service Key Table File
Deleting Older Keys from the Service Key Table File
Propagation Tools
Propagation Tools If You Want To Use This Tool
One or more servers once Propagation is configured Started
Kpropd Daemon
Mkpropcf Tool
250
Kpropd.ini File
Defaultvalues Section
Sections
Chapter 253
Secsrvname Section
Examples
Configuration file
256
Prpadmin Administrative Application
Setting Up Propagation
Primary security server Services and Daemons
Daemon Name Function Generic Usage
260
Chapter 261
262
Monitoring Propagation
Critical Error Messages
Monitoring the Log File
Monitoring Propagation Queue Files
Monitoring Old File Date and Large File Size
Updating the principal.ok Time Stamp
Authentication problems
Comparing the Database to Its Copies
Log files indicate problems
Administration appears normal
Mismatch between the number of principals
Kdbdump Utility
Restarting Propagation Using a Simple Process
Restarting Propagation Using the Full Dump Method
Propagation Failure
Converting a secondary security server to a primary
Security server
Restarting Services
Cleaning the Temp Directory
Number of Realms per Database
Configuring Multirealm Enterprises
Primary security servers Supporting Multiple Realms
Multiple primary security servers Supporting a Single Realm
Adding More Realms to a Multirealm Database
Database Propagation for Multirealm Databases
Managing Multiple Realms
276
One-Way Trust
Considering a Trust Relationship
Two-Way Trust
Hierarchical Trust
Other Types of Trust
Configuring Direct Trust Relationships
280
Hierarchical Interrealm Trust
Hierarchical Chain of Trust
Hierarchical Interrealm Configuration
Chapter 283
Configuring the Local Realm
Configuring the Intermediate Realm
Configuring the Target Realm
Hierarchical Interrealm Trust Chapter 287
288
Troubleshooting
290
Characterizing a Problem
292
Diagnostic Tools
Diagnostic Tools Summary
Tool Description Name
Error Messages
Troubleshooting Kerberos
Logging Capabilities
Unix Syslog File
Troubleshooting Techniques
Services Checklist
Troubleshooting Scenarios Cause Tips
Troubleshooting Scenarios
298
Troubleshooting Scenarios for your LDAP-based Kerberos
Server Scenario Cause Troubleshooting Tips
300
Chapter 301
302
General Errors
Forgotten Passwords
Locking and Unlocking Accounts
Clock Synchronization
User Error Messages
Decrypt Integrity Check Failed
Password Has Expired While Getting Initial Ticket
Administrative Error Messages
Service Key Not Available While Getting Initial Ticket
Chapter 307
Reporting Problems to Your HP Support Contact
Chapter 309
310
Configuration Worksheet
Appendix a
Appendix a 313
314
Sample krb.conf File
Appendix B
Services File
318
Sample krb.realms File
Appendix C
Glossary
Key Distribution Center See KDC
Glossary
V5srvtab
Ticket-granting ticket See TGT
Ticket-granting ticket
Symbols
Index
326
327