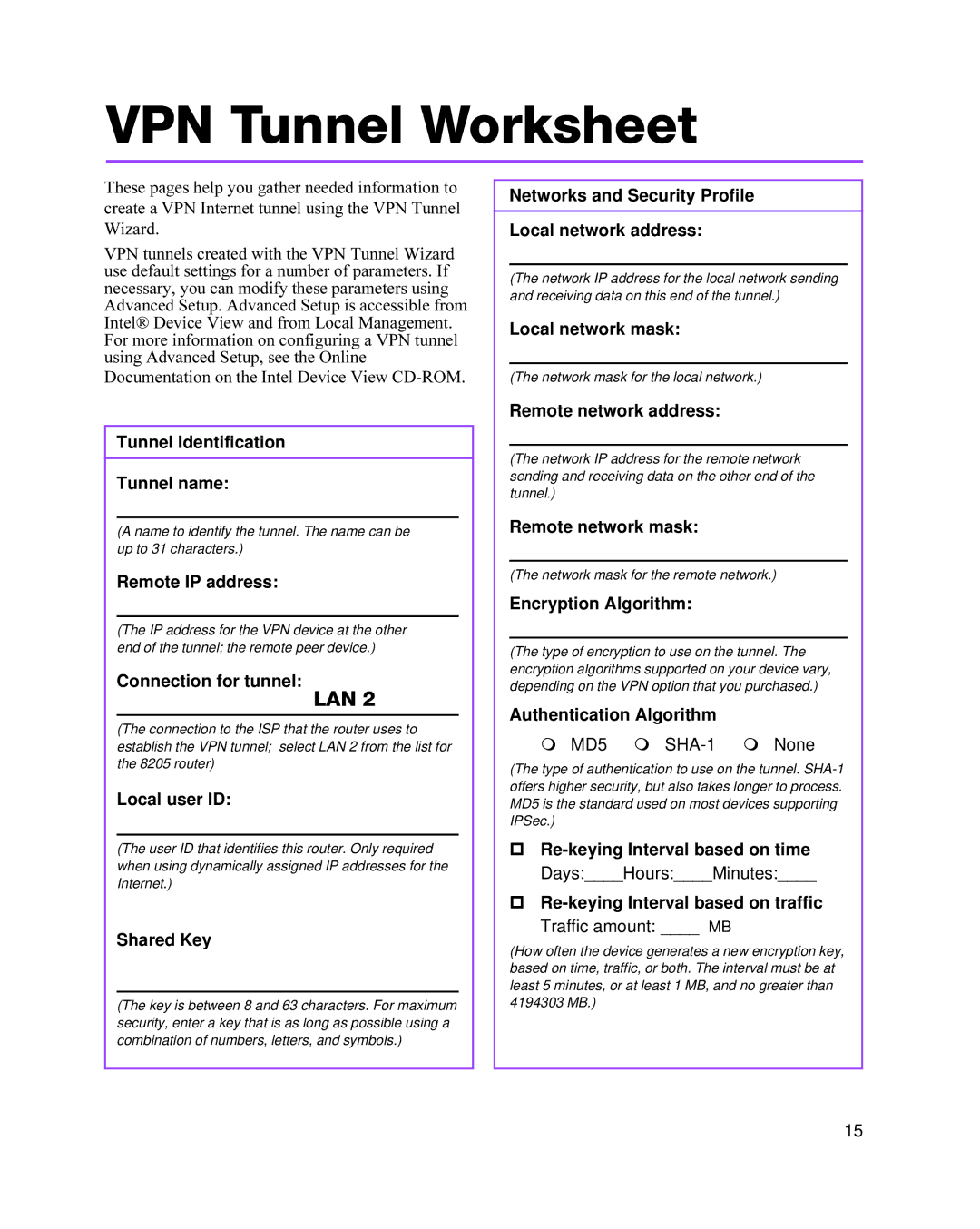
VPN Tunnel Worksheet
These pages help you gather needed information to create a VPN Internet tunnel using the VPN Tunnel Wizard.
VPN tunnels created with the VPN Tunnel Wizard use default settings for a number of parameters. If necessary, you can modify these parameters using Advanced Setup. Advanced Setup is accessible from Intel® Device View and from Local Management. For more information on configuring a VPN tunnel using Advanced Setup, see the Online
Documentation on the Intel Device View
Tunnel Identification
Tunnel name:
(A name to identify the tunnel. The name can be up to 31 characters.)
Remote IP address:
(The IP address for the VPN device at the other end of the tunnel; the remote peer device.)
Connection for tunnel:
LAN 2
(The connection to the ISP that the router uses to establish the VPN tunnel; select LAN 2 from the list for the 8205 router)
Local user ID:
(The user ID that identifies this router. Only required when using dynamically assigned IP addresses for the Internet.)
Shared Key
(The key is between 8 and 63 characters. For maximum security, enter a key that is as long as possible using a combination of numbers, letters, and symbols.)
Networks and Security Profile
Local network address:
(The network IP address for the local network sending and receiving data on this end of the tunnel.)
Local network mask:
(The network mask for the local network.)
Remote network address:
(The network IP address for the remote network sending and receiving data on the other end of the tunnel.)
Remote network mask:
(The network mask for the remote network.)
Encryption Algorithm:
(The type of encryption to use on the tunnel. The encryption algorithms supported on your device vary, depending on the VPN option that you purchased.)
Authentication Algorithm
µMD5 µ SHA-1 µ None
(The type of authentication to use on the tunnel.
π
π
Traffic amount: ____ MB
(How often the device generates a new encryption key, based on time, traffic, or both. The interval must be at least 5 minutes, or at least 1 MB, and no greater than 4194303 MB.)
15