Printer without Imaging Printer with Imaging
Programming Guide
Page
Contents
B780 Configuration Commands
Contents A776 Configurable Slip Commands
User data storage
Bar codes Mode Macros Micr check reader commands
Contents Print and paper feed
Convert 6-dots/mm bitmap to 8-dots/mm bitmap
106
100
113
114
126
121
129
132
142
140
143
144
153
152
154
156
Contents
Where to find the basics
How to use this Guide
Where to find advanced technical information
Support
About this Guide
Runtime diagnostics
Startup Diagnostics
Remote diagnostics
Printer Status, Ethernet and Indicators
Ethernet Terminology
Ethernet terms and default setup
�������������� � � �����������������
Ethernet Default Setup
Indicator Sequence Condition
Indicators
Green slip-in light in front of the paper feed button
For more information about See this section
Migrating from existing CognitiveTPG printers
A758 wide slip station 66 columns
A760 wide slip station 66 columns
24 n1 n2
Command Description Difference between the A756 A776
NL nH
Moving from the A756 to the A776 Emulation commands
A776 Configuration Commands
A776 Emulation Commands
Select A776 Delete Slip Trailing Spaces Option
Select A776 Narrow Slip 51-column Compressed Print Option
Select Cover Open Option
Select A776 21 and 25-line Rotated Slip Print Options
Set Page Mode Option to Trim Full Dots
Set Page Mode Margin Mechanical Adjustment
Select A776 Slip Eject Option
Select 45/60 Column Slip Option
A776 Slip Minimum Units
A776 Slip Character Spacing
A776 Slip Left Margin and Print Width
A776 Slip Print Justification
Ascii
Moving from A756/A758 to A776 Two-color Commands
Discription
LogoEZ colorization commands
B780 Emulation Commands
B780 Configuration Commands
Migrating from the A721 7221 printer to the B780
Select DH Pitch and Rotated Text Columns
Select Two Sensor Option for B780
Select Slip Right Margin in Page Mode
Select Number of Lines of Validation for B780
Select B780 Map User Character Option for B780
Select Cover Open Option for B780
Select B780 Map Logo Option for B780
Select Concurrent Print to Receipt for B780
Select B780 with A776 Slip Functions
Set Page Mode Option to Trim Full Dots
Migrating to a new printer
Programming the Printer 23
Overview of Printing Characteristics
Character appearance
Receipt character specification
Rotated Scaled Shading
Standard
Print zones
Print zones for receipt station 80 mm paper
Programming the Printer 25
Print zones for slip station
1B 64 n command, with n =
Print Zones for Slip, Validation
Lines Inches
Programming the Printer 27
Rotated printing commands
Commands listed by function
Commands in bold are ColorPOS commands
Printer actions
Text characteristics
Print and paper feed
Vertical and horizontal positioning
31
Graphics
Unsolicited status mode Code hexadecimal Command
Batch mode
Status
Real-time
Bar codes
Micr check reader commands
Mode
Macros
User data storage
Ethernet setup commands
Flash download
1D 97 m n User storage status
Programming commands 35
Image Commands
Command conventions
Command descriptions
Clear printer
Open form
Close form
Perform partial knife cut
Generate tone
Selects the device to which the host computer sends data
Select peripheral device for multi-drop
Initialize printer
Set slip paper eject length
This command is ignored if n is out of range
Select receipt or slip for setting line spacing
Select paper sensors to output paper end signals
Programming commands 39
Default Bit of n Function
Enable or disable panel button
Select sensors to stop printing
Set slip paper waiting time
Sends a pulse to open the cash drawer
Generate pulse to open cash drawer
Release Paper
Set current color
Select cut mode and cut paper
After a power loss or reset the default value m=0 is reset
If m is out of the specified range, the command is ignored
Select slip station
Select receipt station
Programming commands 43
Set Interpretation of Set current color
Hexadecimal 1E Decimal
Print and feed paper one line
Print test form
Print and eject slip
Print and carriage return
Range of n Default
Programming commands 45
Feed n dot rows
Add n extra dot rows
Print and feed paper
Print
Print and reverse feed paper
Print and feed n lines
Reverse feed n lines
Print and reverse feed n lines
Reverse feed n dots
Horizontal tab
Set column
Set absolute starting position
Set vertical line spacing to 1/6 inch
Set vertical line spacing
Programming commands 49
Set horizontal tab positions
Value of k
Compatibility information A776 receipt vs. A756 receipt
Set relative print position
Select justification
Programming commands 51
Set left margin
GS L nL nH
Set horizontal and vertical minimum motion units
Default of y
Set printing area width
GS P x y
Select double-wide characters
Text characteristics commands
Select single-wide characters
Select 90 degree counter-clockwise rotated print
Select pitch column width
Standard mode the horizontal motion unit is used
Selects the character pitch for a print line
Set right-side character spacing
Select print mode
Select or cancel user-defined character set
Character sets cannot be used together on the same line
Define user-defined character set
Values and ranges Receipt
Slip s =
This command is ignored if n is out of the specified range
Select or cancel underline mode
Programming commands 57
Copy character set from ROM to RAM
Cancel user-defined character
Select or cancel emphasized mode
Select double-strike
Cancel double-strike
Printer output is the same as in emphasized mode
Select or cancel italic print
Select international character set
Select or cancel upside-down print mode
Select or cancel 90 degree clockwise rotated print
Character sets cannot be mixed on the same line
Select character code table
Select or cancel white/black reverse print mode
Character height selection
Hex Decimal Height
This command is only valid for the receipt station
Reverse color text mode ColorPOS
Set smoothing
Select font ID number
Text strike-through mode ColorPOS
CB hex Kanji CE hex Korean
Select font style number
Download font
Save font ID number as default font at power up
Download font list
Print downloaded font information
Define extended user-defined character set
Programming commands 65
Select active user-defined character set
Values and ranges
Select bit image mode
Value of m Mode No. of dots vertical No. of dots horizontal
Download BMP logo
Dot single-density N1 + 256 × n2
Advanced raster graphics is not available in page mode
Print advanced raster graphics
Value of r
Print Flash Logo
Select double-density graphics
Define Flash Logos
XHxL 1024 max printable xHxL = 72 = 576 dots wide YHyL
Print downloaded bit image
Define downloaded bit image
Print raster color graphics ColorPOS
Print raster monochrome graphics ColorPOS
Download logo image ColorPOS
Max n1 =
Monochrome shade mode ColorPOS
Color shade mode ColorPOS
Programming commands 71
Logo print with color plane swap ColorPOS
Merge watermark mode ColorPOS
Apply shading to logo ColorPOS
Hexadecimal 1D 89 n m Decimal
Form and merge real-time surround graphic ColorPOS
Programming commands 73
This command is ignored in page mode
Background logo print mode ColorPOS
Save graphics buffer as logo ColorPOS
Shade and store logo ColorPOS
Apply margin message mode ColorPOS
Logo print with knife cut
See Print downloaded bit image command
Set temporary max target speed
Decimal Values
Set LogoEZ colorization ColorPOS
Programming commands 77
Example
Value of f
= 3 link margin message printing
Programming commands 79
Modify the settings within the utility
LogoEZ utility default settings
Set LogoEZ attribute mapping ColorPOS
Attributes substituted table Bit on
Programming commands Original attribute mapped table
Enable constant speed logos
Programming commands 81 Related information
Convert 6-dots/mm bitmap to 8-dots/mm bitmap
Transmit peripheral device status
Status command introduction
Hexadecimal 1B 75 Decimal
Value of returned byte Bit
Transmit paper sensor status
Programming commands 83
Transmit printer ID
ESC
Printer ID Specification ID Hexadecimal
Transmits the printer ID specified by n as follows
= 4 Logo Definition Bit Off/On Hex Decimal Function
Preforms the remote diagnostic function specified by n
Transmit printer ID, remote diagnostics extension
Programming commands 85
GS I @ n
Hex Dec Remote diagnostic item Function
Programming commands Value of n
Transmit status
Programming commands 87
A776 B780 Programming Guide
Send printer software version
Real-time commands
Preferred implementation
Rules for using real-time commands
Alternate implementation
Moving data through the buffer
Busy line and fault conditions
Programming commands 91
Real-time status transmission
= Transmit error status Bit Status Hex Decimal Function
A776 B780 Programming Guide
Real-time request to printer
Real-time commands disable
Programming commands 95
Real-time printer status transmission
Select or cancel unsolicited status mode USM
Unsolicited status mode
Bit Off/On Hex Decimal Status for USM
Second byte error information
Fourth byte paper sensor information -- A776
Third byte paper sensor information
Unsolicited status mode USM
Batch mode response
Recognizing data from the printer
Real time response
Select pitch of HRI characters
Select printing position of HRI characters
Select bar code height
Print bar code
Programming commands 101 Exceptions
Bar code
Length
Undercut, default 0, can be set 0 to a-1
Illegal data cancels this command
Programming commands Bar code
Set GS1 DataBar formerly RSS parameters
Print GS1 DataBar formerly RSS, data length specified
Programming commands 103
Print GS1 DataBar formerly RSS, null terminated
Type
GS k
Print multiple barcodes
Programming commands 105
Sample symbol description
Defaults
GS p a b c d e f
Related Information Value Dimension Row height
Select bar code width
Sets the bar code width to n dots
Size
Reset to power-on parameters
Character Size
Exceptions
Slip Page Mode Improved
Mode configurations
Slip Page Mode Enabled
Slip Page Mode Disabled Print and return to standard mode
Programming commands 109
Select page mode
Select standard mode
This command is effective only in page mode
Select print direction in page mode
Programming commands 111
Set print area in page mode
Set absolute vertical print position in page mode
Command is effective only in page mode
Set relative vertical print position in page mode
NL + nH × 256 × vertical or horizontal motion unit inches
Select or cancel macro definition
Contents of the macro can be defined up to 2048 bytes
Execute macro
Programming commands Formulas
Micr commands
Read Micr data and transmit
Status Status byte value
Transmit last Micr read
Micr parsing
Define parsing format, save in Nvram
Define parsing format, do not save permanently
Status Two digits returned
Error number One digit returned
Field separator
Country code One digit returned
Sample parsing formats
Programming commands ESC w p T ‘/ a ‘/ C ‘/ S CR
Check serial number
Programming commands 119
Which writes the two byte word n1n2 to word k in Nvram
Loading the exception table
Exception table entry format
Bits within byte
Programming commands 121
Maintaining the exception table
Write to user data storage
Read from non-volatile memory
Read from user data storage
Write to non-volatile memory Nvram
Select memory type SRAM/flash
Expanded flash memory allocation
Flash memory user sectors allocation
Memory allocation sequence
22 80 31 nL nH Sectors to logo/font area 22 80 32 nL nH
Programming commands Values and ranges
Erase user flash sector
Value of n = 49 Ascii n = 1 HEX
User storage status ColorPOS
Programming commands 125 = 50 Ascii n = 2 HEX
Hexadecimal 1B 5B 7D Decimal 27 91
Download mode
Return segment number status of flash memory
Return boot sector firmware part number
Memory sector to download
Get firmware CRC
Return main program flash CRC
Erase all flash contents except boot sector
Erase selected flash sector
Download to active flash sector
Restore default settings
Reset firmware
Set IP address
Set Net Mask
Set Gateway
Default enabled
Set raw Tcpip port
Telnet Daemon
Inactivity timeout
Dhcp auto-configuration
Programming commands 131
Keep-alive pings
Calibrate Scanner
Imaging Commands
Hexadecimal ID B0 Parameters None
Value Definition
Configure/Change Image Transmission Port
Set Top Entry Startup Delay
Set Image Format Properties
Method
Configure Binarization Methods and Attributes
Programming commands 135
Define/Update Application Tag Values
Decimal Value Definition
T6.G4 binary, else 1=Black is Zero
Return Imager Status
Attach Scan Application Tags
Hexadecimal 1D B6 Parameters None
Hexadecimal 1D B7
Value Definition Decimal Meaning
Real-Time Imager Status
Hexadecimal 10 04 Parameters None
Bit Meaning
Real-Time Cancel Image Transmission
Real-Time Error Status
Wait for Scan & Optionally Transmit
Hexadecimal 10 05 Parameters None Return None
Bit 0 =1 rear image sensor covered
Sensors currently covered none = 0 value
Bit 1 =1 front image sensor covered
Bit 2 =1 image cover open
LZW lossless, also used in GIF compressed grayscale Tiff
Transmit Image
Ccitt T.6 compression binary Tiff
Reserved for Jpeg lossy
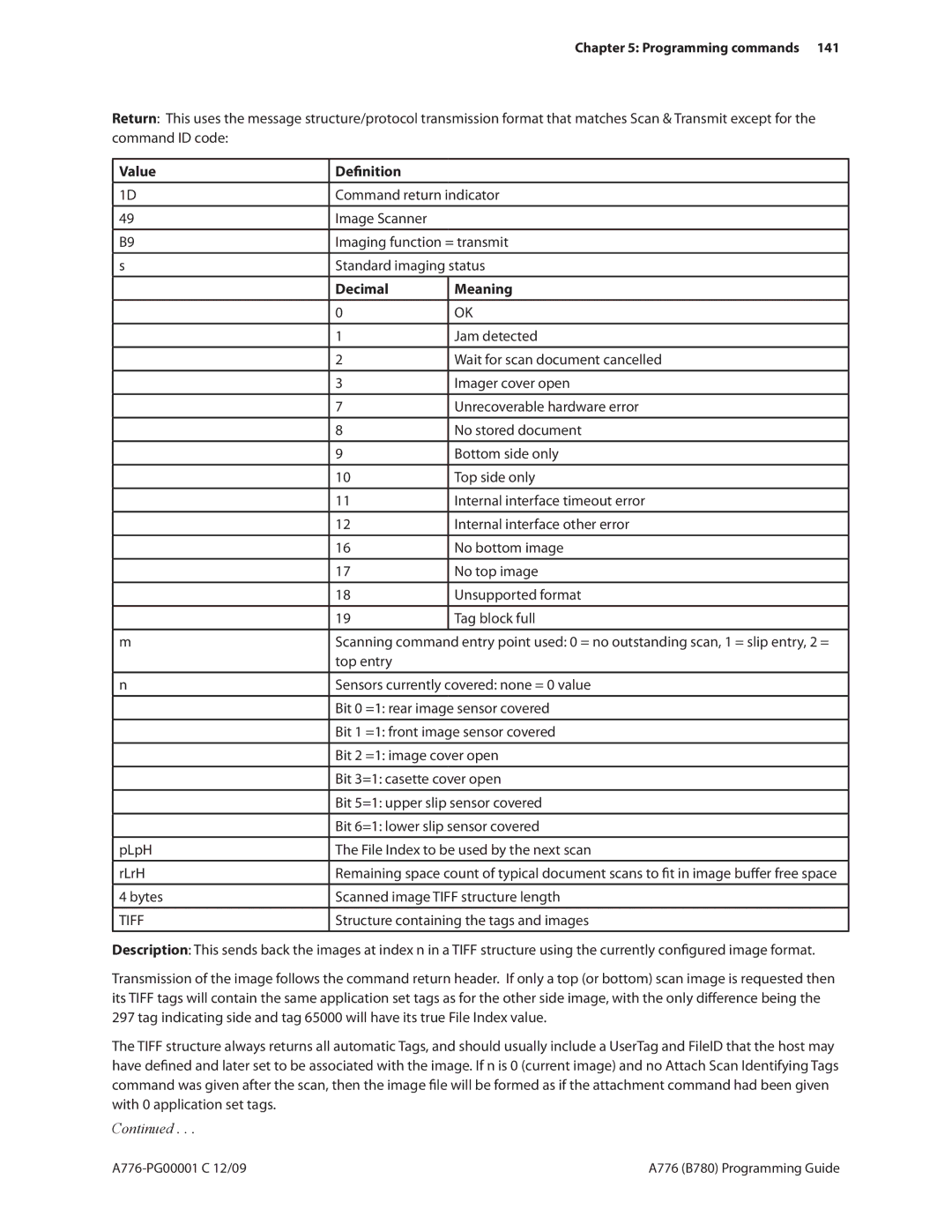
Programming commands 141
Bytes Scanned image Tiff structure length
Structure containing the tags and images
As in the Image Status Command return
Eject from Scanner
Hexadecimal 1D BA p
Free Imager Buffering
Free Image
Get Buffered Image List
Get Buffered Image Attributes
Configure Max Scan Width & Height
Configure Scan Options
Transmit Printer Type Extended Existing Command
Hexadecimal 1D C6 m n Parameters Description
List of DH 4700 Emulation Commands
Hexadecimal Code Command Name
DH Emulation 145
Hexadecimal Code Command Name
List of DH emulation Commands
Printer Function Commands
List of DH 4700 Command Descriptions
Cash Drawer
Reset Printer
Document Clamp Open
Self Test
Document Clamp Close
Clamp Delay
Form Eject
Download
Print Speed
Print Characteristics Commands
Buffered Validate
Buffer Clear
DH Emulation 151
Character Set
Underline Off
Underline Print
Double-High Off
Double-High Font
Graphics
Graphics Commands
Graphics 5 Dot
DH Emulation 153
Status 3 Bit
Printer Status Commands
Transmitted status is shown in the table
Status 6 Bit
DH Emulation 155
Appendix a Commands by hexadecimal code
Commands listed by hexadecimal code
34 m a0 a1 a2
157
Appendix a Commands by hexadecimal code Code hexadecimal
Or …n160 Print raster color graphics
159
X y o p q
M n o Apply margin message mode
161
Code Page 437 US
Appendix B Resident Character Sets
163
Code page 737 Greek
Code page 850 Multilingual
165
Code Page 852 Slavic
Code Page 857 Turkish
167
Code page 858 with Eurosymbol
Code page 860 Portugese
169
Code page 862 Hebrew
Code page 863 French Canadian
171
Code page 865 Nordic
Code page 866 Cyrillic
173
Code page 1252 Windows Latin
Page
1F 03 18 01 n Auto Journal Mode via Configuration Command
Electronic Journal Storage
There are two methods for activating Electronic Journal
Exception Conditions in Auto Journal Mode
Journal RAM buffer
Journal Flash buffer
Operator Activation of Journal Print and Erase
Printing and Erasing the Journal Flash Buffer
1F 0A C3 Clear Journal
1F 0A C4 Print Journal
Returns one byte of status
1F 0A C5 Return Journal Status
1F 0A C6 Return Journal Flash Size
Journal flash Buffer used
Page
A776-PG00001 Rev. C 12/09