Installing Red Hat* Enterprise Linux 4*
Intel® Server Board S5000PAL
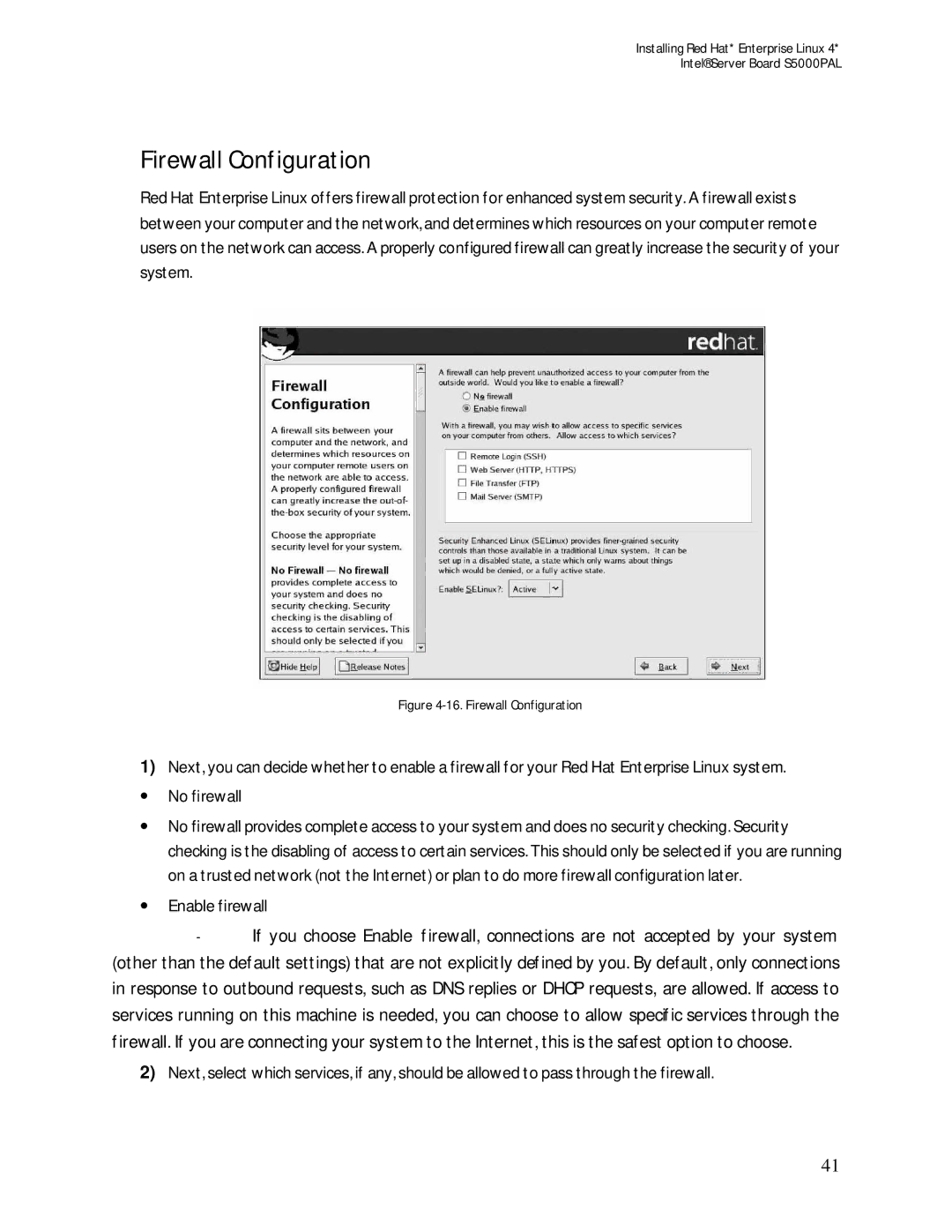
Firewall Configuration
Red Hat Enterprise Linux offers firewall protection for enhanced system security. A firewall exists between your computer and the network, and determines which resources on your computer remote users on the network can access. A properly configured firewall can greatly increase the security of your system.
Figure 4-16. Firewall Configuration
1)Next, you can decide whether to enable a firewall for your Red Hat Enterprise Linux system.
∙No firewall
∙No firewall provides complete access to your system and does no security checking. Security checking is the disabling of access to certain services. This should only be selected if you are running on a trusted network (not the Internet) or plan to do more firewall configuration later.
∙Enable firewall
-If you choose Enable firewall, connections are not accepted by your system (other than the default settings) that are not explicitly defined by you. By default, only connections in response to outbound requests, such as DNS replies or DHCP requests, are allowed. If access to services running on this machine is needed, you can choose to allow specific services through the firewall. If you are connecting your system to the Internet, this is the safest option to choose.
2)Next, select which services, if any, should be allowed to pass through the firewall.
41