3 | Retrieve the email with your | Your System Admin has setup your IronKey ahead of | ||
| Activation Code. Copy and paste | time to abide by your organization’s security standards. | ||
| it into the IronKey window. | You will receive an email with an Activation Code that | ||
|
|
|
| is needed to use your IronKey. |
|
|
|
| Enter your email address and your Activation Code |
|
|
|
| into the fields provided on the IronKey window. Click |
|
|
|
| ‘Continue’ when you are ready. |
|
|
|
| If your IronKey cannot connect to the Internet, click |
|
|
|
| “Edit Proxy Settings...” to adjust its network settings. |
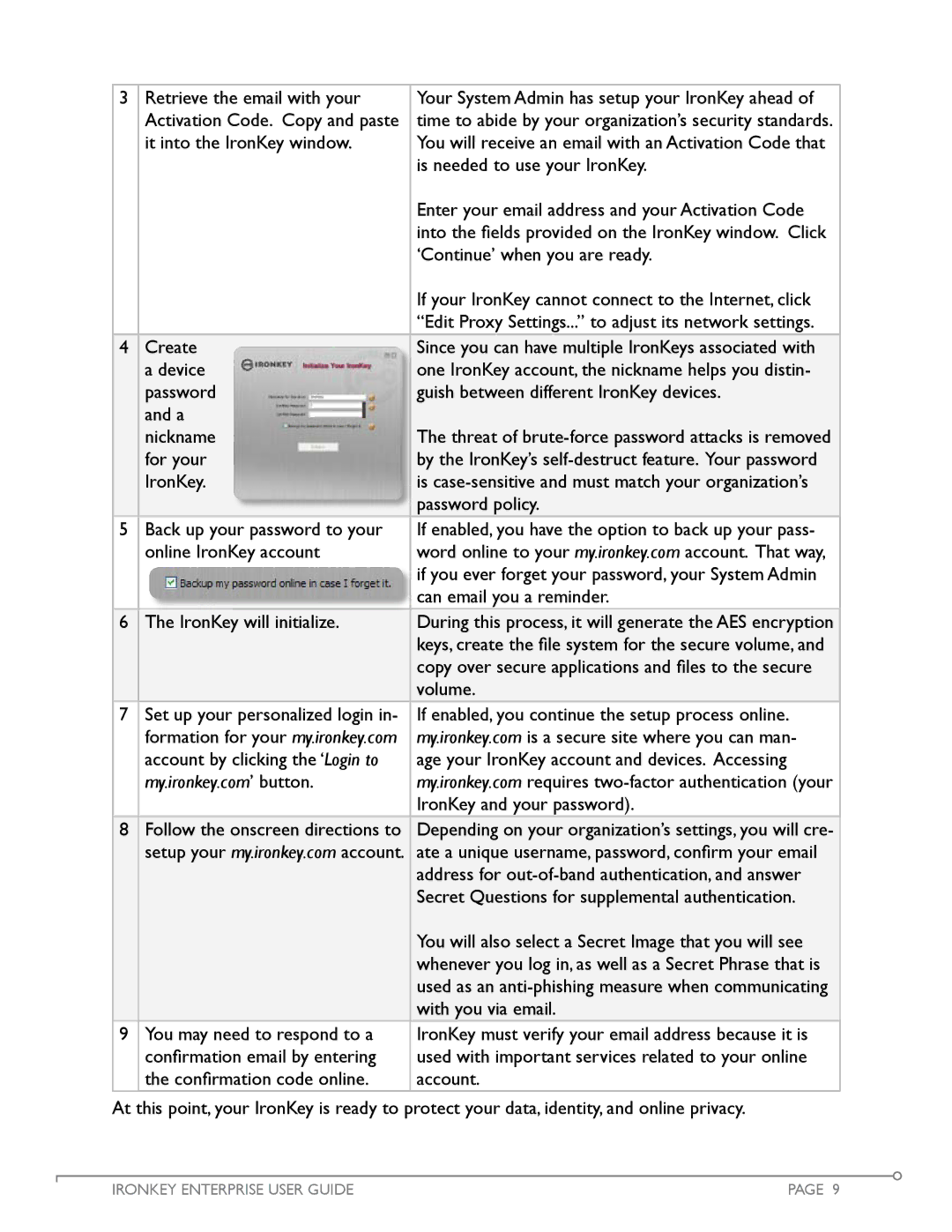
4 | Create |
| Since you can have multiple IronKeys associated with | |
| ||||
| a device |
| one IronKey account, the nickname helps you distin- | |
| password |
| guish between different IronKey devices. | |
| and a |
|
| |
| nickname |
| The threat of | |
| for your |
| by the IronKey’s | |
| IronKey. |
| is | |
|
|
|
| password policy. |
|
|
|
|
|
5 | Back up your password to your | If enabled, you have the option to back up your pass- | ||
| online IronKey account | word online to your my.ironkey.com account. That way, | ||
|
|
|
| if you ever forget your password, your System Admin |
|
|
|
| can email you a reminder. |
6 | The IronKey will initialize. | During this process, it will generate the AES encryption | ||
|
|
|
| keys, create the file system for the secure volume, and |
|
|
|
| copy over secure applications and files to the secure |
|
|
|
| volume. |
7 | Set up your personalized login in- | If enabled, you continue the setup process online. | ||
| formation for your my.ironkey.com | my.ironkey.com is a secure site where you can man- | ||
| account by clicking the ‘Login to | age your IronKey account and devices. Accessing | ||
| my.ironkey.com’ button. | my.ironkey.com requires | ||
|
|
|
| IronKey and your password). |
8 | Follow the onscreen directions to | Depending on your organization’s settings, you will cre- | ||
| setup your my.ironkey.com account. | ate a unique username, password, confirm your email | ||
|
|
|
| address for |
|
|
|
| Secret Questions for supplemental authentication. |
|
|
|
| You will also select a Secret Image that you will see |
|
|
|
| whenever you log in, as well as a Secret Phrase that is |
|
|
|
| used as an |
|
|
|
| with you via email. |
9 | You may need to respond to a | IronKey must verify your email address because it is | ||
| confirmation email by entering | used with important services related to your online | ||
| the confirmation code online. | account. | ||
At this point, your IronKey is ready to protect your data, identity, and online privacy.
IRONKEY ENTERPRISE USER GUIDE | PAGE |