Section 4 | IP Access Configuration & Operation | |
|
|
|
Certificate
The
This certificate and the underlying secret key is the same for all
However, it is possible to generate and install a new certificate that is unique for a particular
The following steps are necessary to create and install an SSL certificate for the
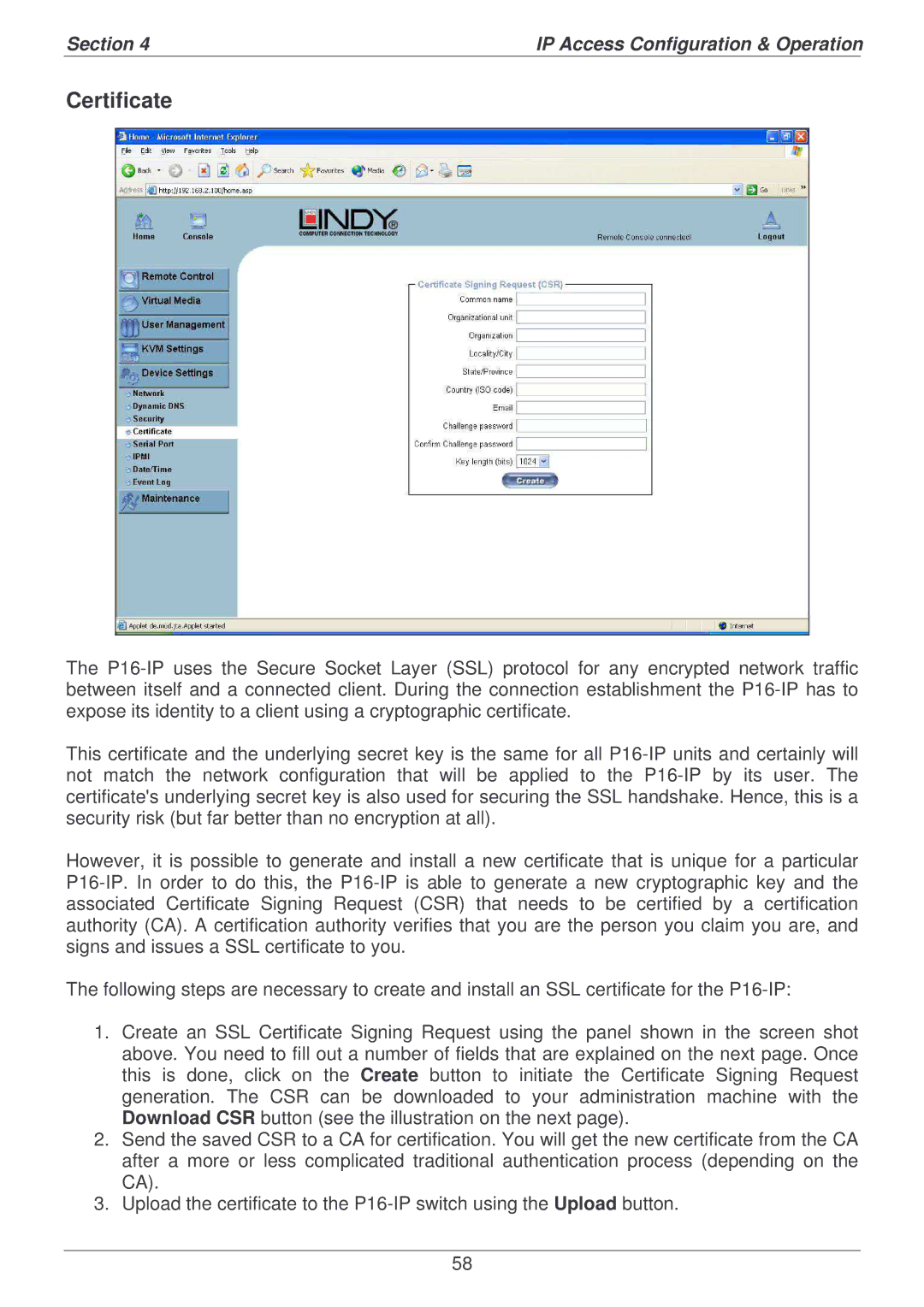
1.Create an SSL Certificate Signing Request using the panel shown in the screen shot above. You need to fill out a number of fields that are explained on the next page. Once this is done, click on the Create button to initiate the Certificate Signing Request generation. The CSR can be downloaded to your administration machine with the Download CSR button (see the illustration on the next page).
2.Send the saved CSR to a CA for certification. You will get the new certificate from the CA after a more or less complicated traditional authentication process (depending on the CA).
3.Upload the certificate to the
58