Wireless-G Home Router
Caution: The Router is not designed to have a
If you have enabled the Wireless RF Scheduling function and leave the Router unused
When you finish making changes to this screen, click the Save Settings button to save the changes, or click the Cancel Changes button to undo your changes. Help information is shown on the
The Wireless Tab - Wireless Security
The Wireless Security settings configure the security of your wireless network. There are six wireless security mode options supported by the Router: WPA Personal, WPA Enterprise, WPA2 Personal, WPA2 Enterprise, RADIUS, and WEP. (WEP stands for Wired Equivalent Privacy, WPA stands for
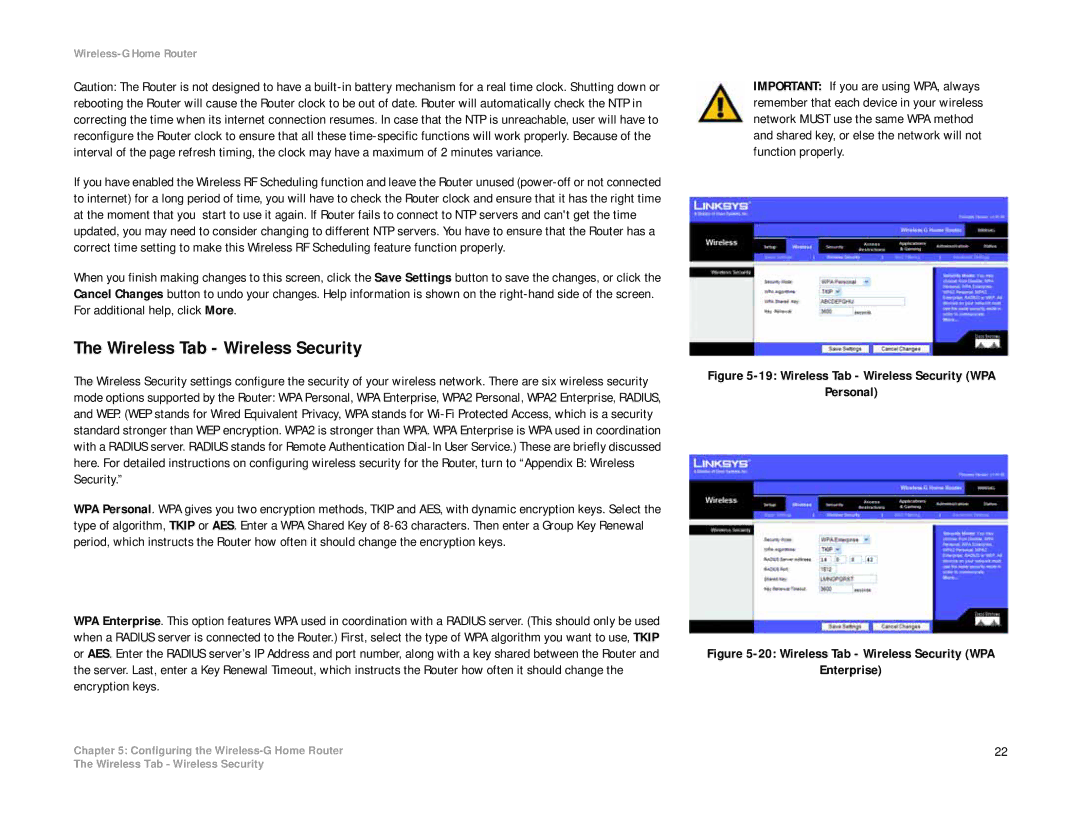
WPA Personal. WPA gives you two encryption methods, TKIP and AES, with dynamic encryption keys. Select the type of algorithm, TKIP or AES. Enter a WPA Shared Key of
WPA Enterprise. This option features WPA used in coordination with a RADIUS server. (This should only be used when a RADIUS server is connected to the Router.) First, select the type of WPA algorithm you want to use, TKIP or AES. Enter the RADIUS server’s IP Address and port number, along with a key shared between the Router and the server. Last, enter a Key Renewal Timeout, which instructs the Router how often it should change the encryption keys.
Chapter 5: Configuring the
IMPORTANT: If you are using WPA, always remember that each device in your wireless network MUST use the same WPA method and shared key, or else the network will not function properly.
Figure 5-19: Wireless Tab - Wireless Security (WPA
Personal)
Figure 5-20: Wireless Tab - Wireless Security (WPA
Enterprise)
22
The Wireless Tab - Wireless Security