Chapter 5 | Configuring the |
PPTP PassThrough
L2TP PassThrough Layer 2 Tunneling Protocol is the method used to enable
When you have finished making changes to the screen, click Save Settings to save the changes, or click Cancel Changes to undo your changes. For help information, click More.
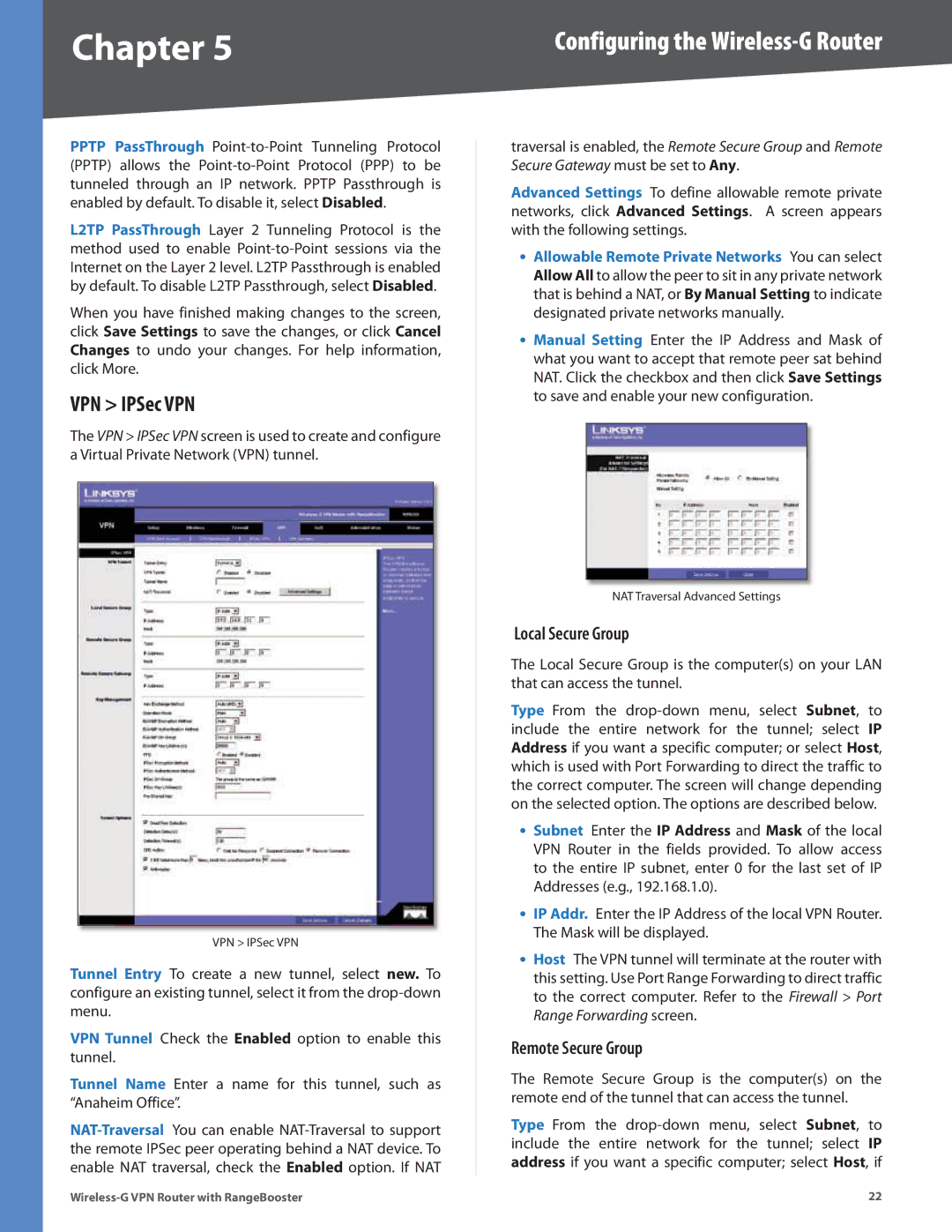
VPN > IPSec VPN
The VPN > IPSec VPN screen is used to create and configure a Virtual Private Network (VPN) tunnel.
VPN > IPSec VPN
Tunnel Entry To create a new tunnel, select new. To configure an existing tunnel, select it from the
VPN Tunnel Check the Enabled option to enable this tunnel.
Tunnel Name Enter a name for this tunnel, such as “Anaheim Office”.
traversal is enabled, the Remote Secure Group and Remote Secure Gateway must be set to Any.
Advanced Settings To define allowable remote private networks, click Advanced Settings. A screen appears with the following settings.
•Allowable Remote Private Networks You can select Allow All to allow the peer to sit in any private network that is behind a NAT, or By Manual Setting to indicate designated private networks manually.
•Manual Setting Enter the IP Address and Mask of what you want to accept that remote peer sat behind NAT. Click the checkbox and then click Save Settings to save and enable your new configuration.
NAT Traversal Advanced Settings
Local Secure Group
The Local Secure Group is the computer(s) on your LAN that can access the tunnel.
Type From the
•Subnet Enter the IP Address and Mask of the local VPN Router in the fields provided. To allow access to the entire IP subnet, enter 0 for the last set of IP Addresses (e.g., 192.168.1.0).
•IP Addr. Enter the IP Address of the local VPN Router. The Mask will be displayed.
•Host The VPN tunnel will terminate at the router with this setting. Use Port Range Forwarding to direct traffic to the correct computer. Refer to the Firewall > Port Range Forwarding screen.
Remote Secure Group
The Remote Secure Group is the computer(s) on the remote end of the tunnel that can access the tunnel.
Type From the
22 |