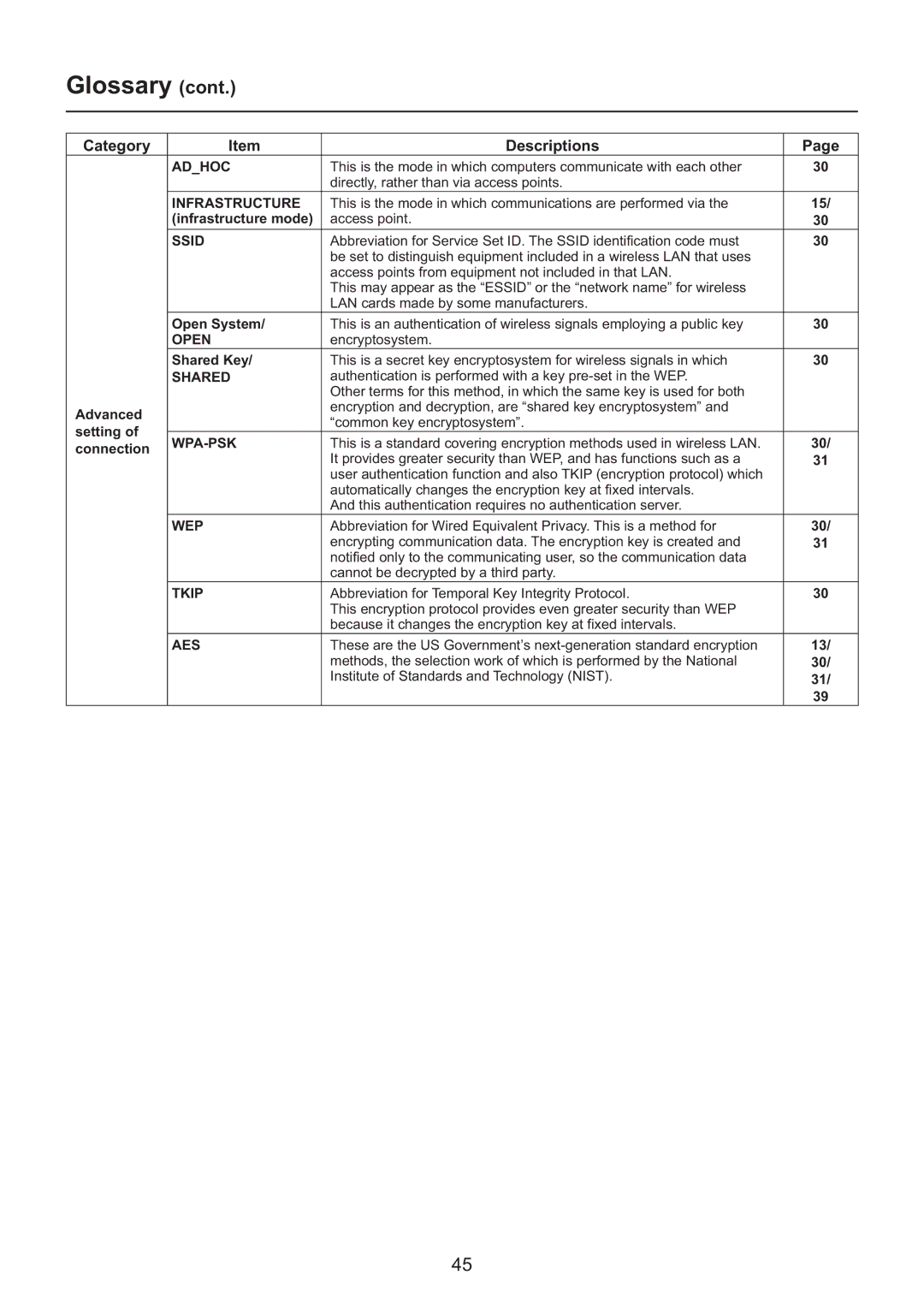
Glossary (cont.)
Category | Item | Descriptions | Page | |
| AD_HOC | This is the mode in which computers communicate with each other | 30 | |
|
| directly, rather than via access points. |
| |
| INFRASTRUCTURE | This is the mode in which communications are performed via the | 15/ | |
| (infrastructure mode) | access point. | 30 | |
| SSID | Abbreviation for Service Set ID. The SSID identification code must | 30 | |
|
| be set to distinguish equipment included in a wireless LAN that uses |
| |
|
| access points from equipment not included in that LAN. |
| |
|
| This may appear as the “ESSID” or the “network name” for wireless |
| |
|
| LAN cards made by some manufacturers. |
| |
| Open System/ | This is an authentication of wireless signals employing a public key | 30 | |
| OPEN | encryptosystem. |
| |
| Shared Key/ | This is a secret key encryptosystem for wireless signals in which | 30 | |
| SHARED | authentication is performed with a key |
| |
|
| Other terms for this method, in which the same key is used for both |
| |
Advanced |
| encryption and decryption, are “shared key encryptosystem” and |
| |
| “common key encryptosystem”. |
| ||
setting of |
|
| ||
| This is a standard covering encryption methods used in wireless LAN. | 30/ | ||
connection | ||||
| It provides greater security than WEP, and has functions such as a | 31 | ||
|
| |||
|
| user authentication function and also TKIP (encryption protocol) which |
| |
|
| automatically changes the encryption key at fixed intervals. |
| |
|
| And this authentication requires no authentication server. |
| |
| WEP | Abbreviation for Wired Equivalent Privacy. This is a method for | 30/ | |
|
| encrypting communication data. The encryption key is created and | 31 | |
|
| notified only to the communicating user, so the communication data |
| |
|
| cannot be decrypted by a third party. |
| |
| TKIP | Abbreviation for Temporal Key Integrity Protocol. | 30 | |
|
| This encryption protocol provides even greater security than WEP |
| |
|
| because it changes the encryption key at fixed intervals. |
| |
| AES | These are the US Government’s | 13/ | |
|
| methods, the selection work of which is performed by the National | 30/ | |
|
| Institute of Standards and Technology (NIST). | 31/ | |
|
|
| 39 |
45