8.3.2.2Code description
The protection code (see Table 68) is a cyclic binary BCH code.
Table 68: | Protection code |
|
| |
|
|
|
|
|
|
|
| Number of |
|
| Maximum data |
| redundant | Minimum distance |
Code | bits allowed |
| bits | of the code |
|
|
|
|
|
|
|
|
|
|
(21,15,4) | 15 |
| 6 | 4 |
|
|
|
|
|
The BCH protection code is a cyclic code with a generator polynomial of x 6 + x 5 + x 2 + 1.
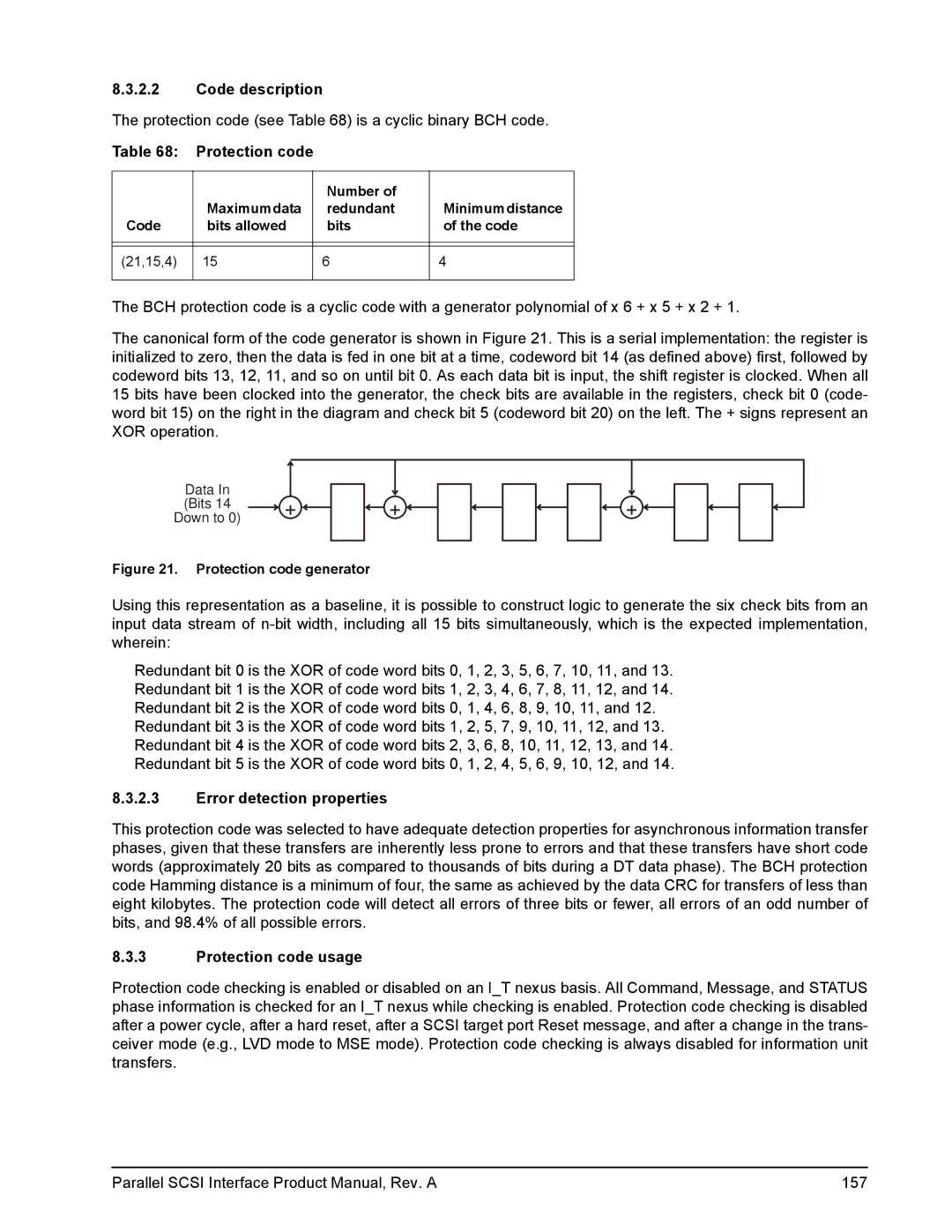
The canonical form of the code generator is shown in Figure 21. This is a serial implementation: the register is initialized to zero, then the data is fed in one bit at a time, codeword bit 14 (as defined above) first, followed by codeword bits 13, 12, 11, and so on until bit 0. As each data bit is input, the shift register is clocked. When all 15 bits have been clocked into the generator, the check bits are available in the registers, check bit 0 (code- word bit 15) on the right in the diagram and check bit 5 (codeword bit 20) on the left. The + signs represent an XOR operation.
Data In (Bits 14 Down to 0)
Figure 21. Protection code generator
Using this representation as a baseline, it is possible to construct logic to generate the six check bits from an input data stream of
Redundant bit 0 is the XOR of code word bits 0, 1, 2, 3, 5, 6, 7, 10, 11, and 13. Redundant bit 1 is the XOR of code word bits 1, 2, 3, 4, 6, 7, 8, 11, 12, and 14. Redundant bit 2 is the XOR of code word bits 0, 1, 4, 6, 8, 9, 10, 11, and 12.
Redundant bit 3 is the XOR of code word bits 1, 2, 5, 7, 9, 10, 11, 12, and 13. Redundant bit 4 is the XOR of code word bits 2, 3, 6, 8, 10, 11, 12, 13, and 14. Redundant bit 5 is the XOR of code word bits 0, 1, 2, 4, 5, 6, 9, 10, 12, and 14.
8.3.2.3Error detection properties
This protection code was selected to have adequate detection properties for asynchronous information transfer phases, given that these transfers are inherently less prone to errors and that these transfers have short code words (approximately 20 bits as compared to thousands of bits during a DT data phase). The BCH protection code Hamming distance is a minimum of four, the same as achieved by the data CRC for transfers of less than eight kilobytes. The protection code will detect all errors of three bits or fewer, all errors of an odd number of bits, and 98.4% of all possible errors.
8.3.3Protection code usage
Protection code checking is enabled or disabled on an I_T nexus basis. All Command, Message, and STATUS phase information is checked for an I_T nexus while checking is enabled. Protection code checking is disabled after a power cycle, after a hard reset, after a SCSI target port Reset message, and after a change in the trans- ceiver mode (e.g., LVD mode to MSE mode). Protection code checking is always disabled for information unit transfers.
Parallel SCSI Interface Product Manual, Rev. A | 157 |