Chapter 1 Overview
Rogue Access Points
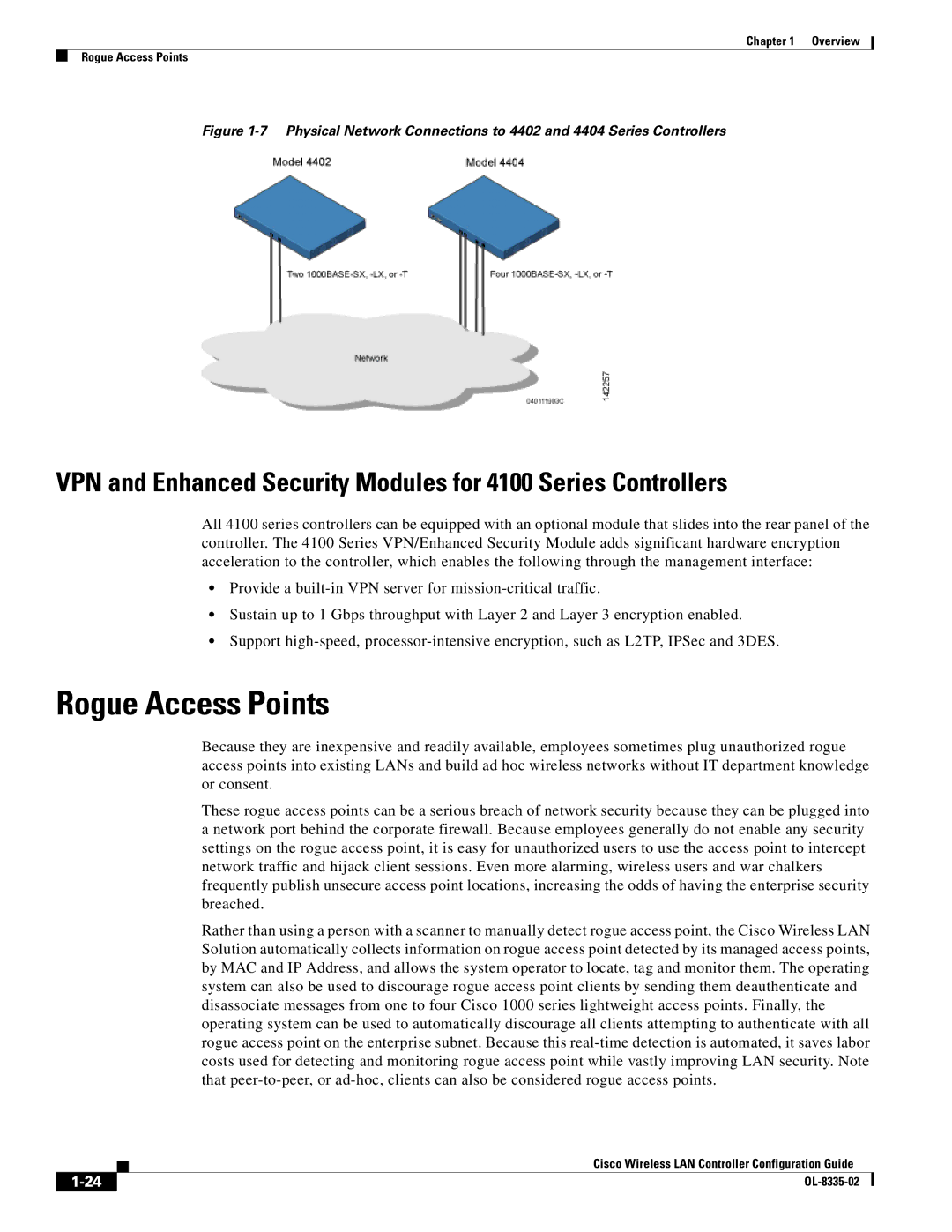
Figure 1-7 Physical Network Connections to 4402 and 4404 Series Controllers
VPN and Enhanced Security Modules for 4100 Series Controllers
All 4100 series controllers can be equipped with an optional module that slides into the rear panel of the controller. The 4100 Series VPN/Enhanced Security Module adds significant hardware encryption acceleration to the controller, which enables the following through the management interface:
•Provide a
•Sustain up to 1 Gbps throughput with Layer 2 and Layer 3 encryption enabled.
•Support
Rogue Access Points
Because they are inexpensive and readily available, employees sometimes plug unauthorized rogue access points into existing LANs and build ad hoc wireless networks without IT department knowledge or consent.
These rogue access points can be a serious breach of network security because they can be plugged into a network port behind the corporate firewall. Because employees generally do not enable any security settings on the rogue access point, it is easy for unauthorized users to use the access point to intercept network traffic and hijack client sessions. Even more alarming, wireless users and war chalkers frequently publish unsecure access point locations, increasing the odds of having the enterprise security breached.
Rather than using a person with a scanner to manually detect rogue access point, the Cisco Wireless LAN Solution automatically collects information on rogue access point detected by its managed access points, by MAC and IP Address, and allows the system operator to locate, tag and monitor them. The operating system can also be used to discourage rogue access point clients by sending them deauthenticate and disassociate messages from one to four Cisco 1000 series lightweight access points. Finally, the operating system can be used to automatically discourage all clients attempting to authenticate with all rogue access point on the enterprise subnet. Because this
Cisco Wireless LAN Controller Configuration Guide
| ||
|