The Security Tabs
Firewall
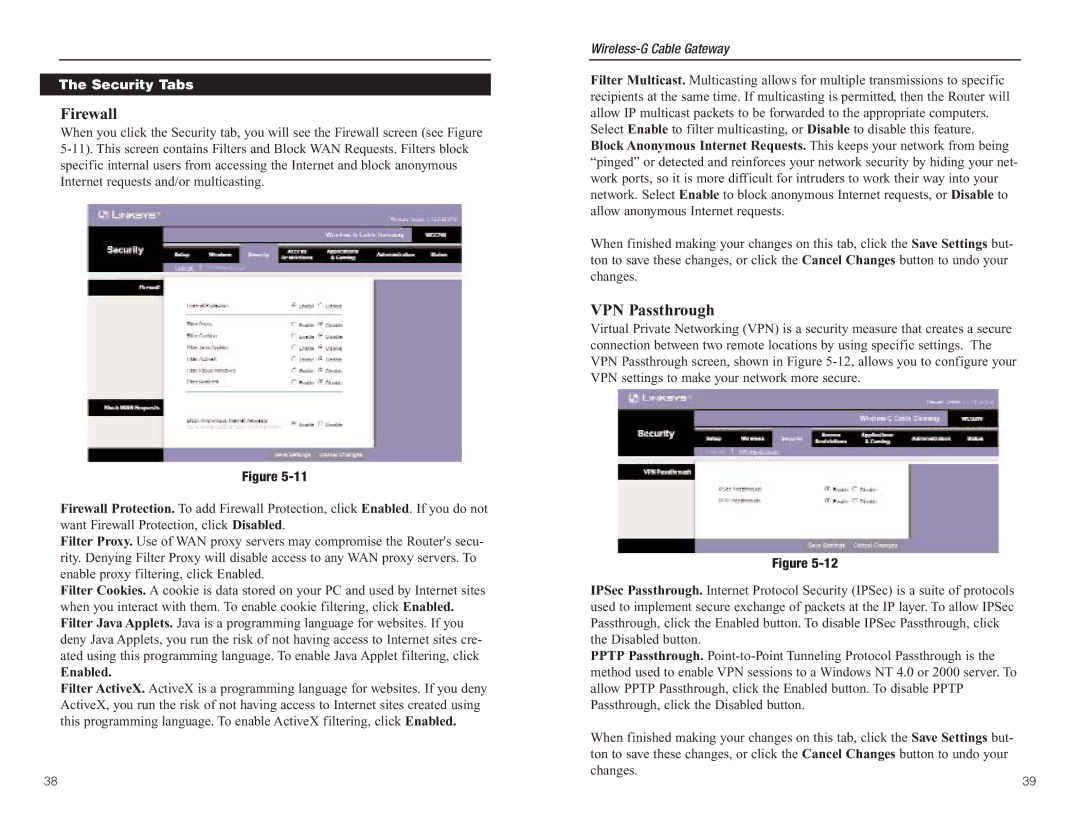
When you click the Security tab, you will see the Firewall screen (see Figure
Figure
Firewall Protection. To add Firewall Protection, click Enabled. If you do not want Firewall Protection, click Disabled.
Filter Proxy. Use of WAN proxy servers may compromise the Router's secu- rity. Denying Filter Proxy will disable access to any WAN proxy servers. To enable proxy filtering, click Enabled.
Filter Cookies. A cookie is data stored on your PC and used by Internet sites when you interact with them. To enable cookie filtering, click Enabled. Filter Java Applets. Java is a programming language for websites. If you deny Java Applets, you run the risk of not having access to Internet sites cre- ated using this programming language. To enable Java Applet filtering, click
Enabled.
Filter ActiveX. ActiveX is a programming language for websites. If you deny ActiveX, you run the risk of not having access to Internet sites created using this programming language. To enable ActiveX filtering, click Enabled.
Filter Multicast. Multicasting allows for multiple transmissions to specific recipients at the same time. If multicasting is permitted, then the Router will allow IP multicast packets to be forwarded to the appropriate computers.
Select Enable to filter multicasting, or Disable to disable this feature. Block Anonymous Internet Requests. This keeps your network from being “pinged” or detected and reinforces your network security by hiding your net- work ports, so it is more difficult for intruders to work their way into your network. Select Enable to block anonymous Internet requests, or Disable to allow anonymous Internet requests.
When finished making your changes on this tab, click the Save Settings but- ton to save these changes, or click the Cancel Changes button to undo your changes.
VPN Passthrough
Virtual Private Networking (VPN) is a security measure that creates a secure connection between two remote locations by using specific settings. The VPN Passthrough screen, shown in Figure
Figure
IPSec Passthrough. Internet Protocol Security (IPSec) is a suite of protocols used to implement secure exchange of packets at the IP layer. To allow IPSec Passthrough, click the Enabled button. To disable IPSec Passthrough, click the Disabled button.
PPTP Passthrough.
When finished making your changes on this tab, click the Save Settings but- ton to save these changes, or click the Cancel Changes button to undo your changes.
38 | 39 |