User’s Manual for the NETGEAR Double 108 Mbps Wireless PC Card
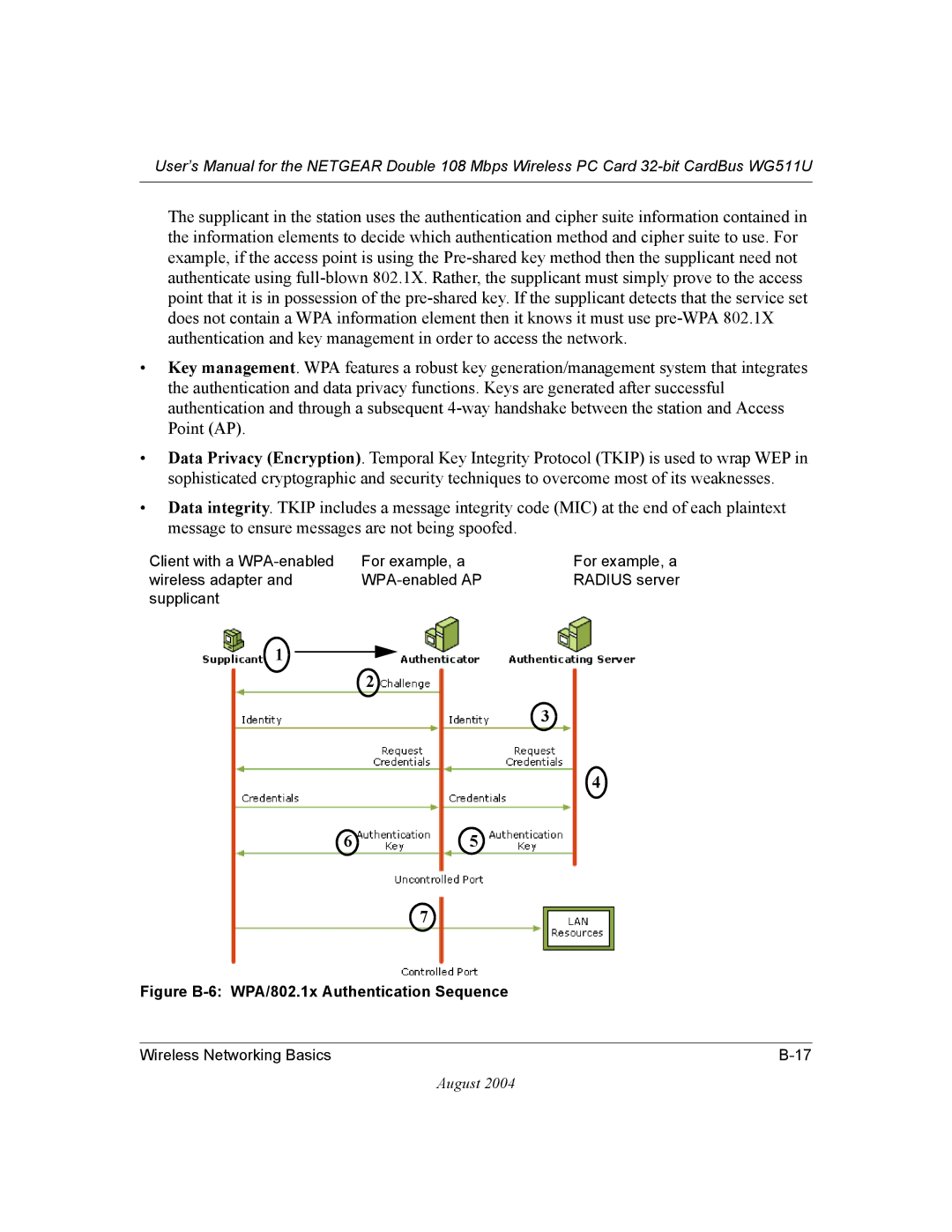
The supplicant in the station uses the authentication and cipher suite information contained in the information elements to decide which authentication method and cipher suite to use. For example, if the access point is using the
•Key management. WPA features a robust key generation/management system that integrates the authentication and data privacy functions. Keys are generated after successful authentication and through a subsequent
•Data Privacy (Encryption). Temporal Key Integrity Protocol (TKIP) is used to wrap WEP in sophisticated cryptographic and security techniques to overcome most of its weaknesses.
•Data integrity. TKIP includes a message integrity code (MIC) at the end of each plaintext message to ensure messages are not being spoofed.
Client with a | For example, a | For example, a |
wireless adapter and | RADIUS server | |
supplicant |
|
|
![]() 1
1 ![]()
![]() 3
3
4
![]() 5
5
![]() 7
7
Figure B-6: WPA/802.1x Authentication Sequence
Wireless Networking Basics |
August 2004