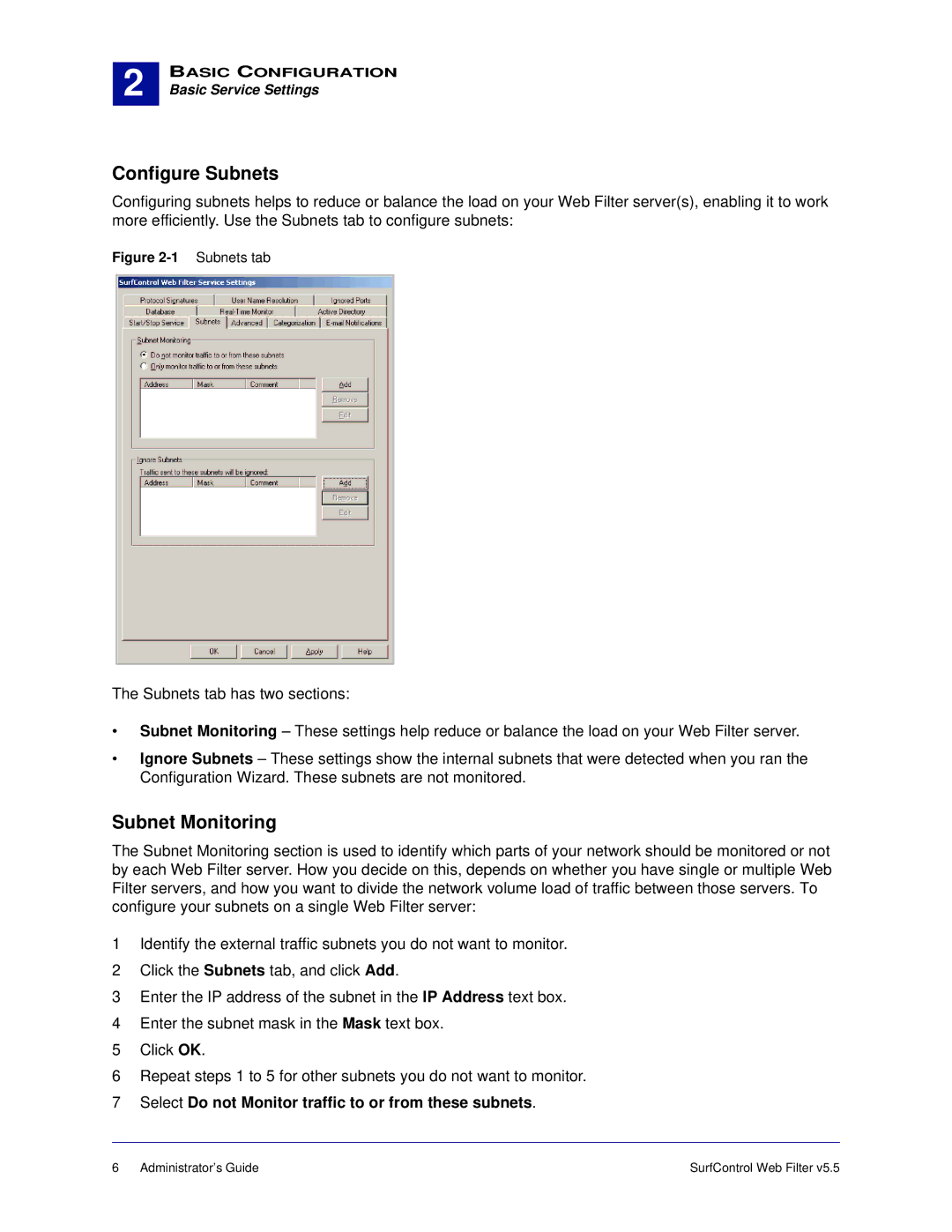
5.5 specifications
Surf Control 5.5 is a robust web filtering and security software designed for organizations seeking comprehensive internet safety and enhanced productivity. With the increasing reliance on the internet for business operations, it becomes imperative to utilize tools that not only ensure secure browsing but also improve workplace efficiency. Surf Control 5.5 offers a range of features that cater to these needs effectively.One of the standout features of Surf Control 5.5 is its powerful web filtering capabilities. The software employs a robust categorization system that classifies websites into various categories such as social media, gambling, adult content, and more. This allows administrators to set policies that restrict access to non-work-related sites, leading to improved employee focus and reduced distractions during work hours.
Another significant characteristic of Surf Control 5.5 is its customizable policy management. Administrators have the flexibility to create specific access rules based on user roles, departments, or individual needs. This granular control ensures that employees can access the resources they need while maintaining an overall secure browsing environment.
Surf Control 5.5 leverages advanced technologies like real-time content analysis and URL filtering to provide instant protection against harmful websites. By analyzing web traffic in real-time, the software can block access to sites that are deemed unsafe or inappropriate, thus minimizing the risk of malware infections and data breaches.
In addition to web filtering, Surf Control 5.5 includes robust reporting and monitoring tools. These features allow administrators to track website usage patterns, identify potential security threats, and generate reports to analyze internet activities across the organization. This data is invaluable for making informed decisions regarding internet usage and policy adjustments.
Moreover, Surf Control 5.5 is designed with user-friendliness in mind. Its intuitive interface facilitates easy setup and management, enabling IT personnel to implement and oversee policies without extensive training. This ease of use, combined with its powerful features, makes Surf Control 5.5 an ideal choice for organizations of various sizes.
In conclusion, Surf Control 5.5 is an essential tool for businesses looking to enhance their internet security and workplace efficiency. With its advanced web filtering, customizable policy management, real-time protection, and comprehensive reporting features, it offers a holistic approach to internet safety in the modern workplace. Organizations leveraging this software can expect to see a significant improvement in productivity and a reduction in exposure to online risks.