9032578-05
SmartSwitch Router User Reference Manual
Trademarks
Copyright
Changes
Disclaimer
Regulatory Compliance Statements
Regulatory Compliance Information
Vcci Compliance Statement
Industry Canada Compliance Statement
Laser Radiation and Connectors
Safety Information Class 1 Laser Transceivers
Cabletron Systems, Inc Program License Agreement
SmartSwitch Router User Reference Manual Vii
Viii SmartSwitch Router User Reference Manual
SmartSwitch Router User Reference Manual
Cabletron Systems Limited Program License Agreement
Cabletron Systems Limited Program License Agreement
Declaration of Conformity Addendum
Contents
SmartTRUNK Configuration Guide
Dhcp Configuration Guide
Vrrp Configuration Guide
111
160
Routing Policy Configuration Guide 161
197
Firewall Load Balancing 214 Monitoring IP Policies 215
Network Address Translation Configuration Guide
249
QoS & Layer-2/Layer-3/Layer-4 Flow Overview 291
Security Configuration Guide 275
309
Lfap Configuration Guide 329
357
Contents Xxvi SmartSwitch Router User Reference Manual
For Information About See
About This Manual
Related Documentation
Document Conventions
Choice. Select one keyword or argument
Keywords and arguments within a set of square brackets are
Optional
Keywords or arguments separated by vertical bars indicate a
Chapter Introduction
Configuration Files
Enable Mode
Using the Command Line Interface
Command Modes
User Mode
Boot Prom Mode
Getting Help with CLI Commands
Configure Mode
CLI completes the command as follows
CLI Line Editing Commands
Line Editing Commands
Show all commands currently stored in the history buffer
Next command from history buffer
Previous command from history buffer
Word-backward command
Commands to Display and Change Configuration Information
Displaying and Changing Configuration Information
Save active
Task Command
Erase scratchpad
Erase startup
Line Card Port Number Arrangement Left to Right
Port Names
Each port in the SSR is referred to in the following manner
Port Numbers for Line Cards
Hssi WAN
Base LLX Quad Serial WAN
Hot Swapping Overview
Chapter Hot Swapping Line Cards Control Modules
Deactivating the Line Card
Hot Swapping Line Cards
Hot Swapping One Type of Line Card With Another
Installing a New Line Card
Removing the Line Card
Deactivating the Control Module
Hot Swapping a Secondary Control Module
Removing the Control Module
Installing a Control Module
Hot Swapping a Switching Fabric Module SSR 8600 only
Installing a Switching Fabric Module
Removing the Switching Fabric Module
Page
Spanning Tree Ieee 802.1d
Chapter Bridging Configuration Guide
Bridging Overview
Bridging Modes Flow-Based and Address-Based
Vlan Overview
Subnet-based VLANs
Port-based VLANs
MAC-address-based VLANs
Protocol-based VLANs
VLANs and the SSR
SSR Vlan Support
Multicast-based VLANs
Policy-based VLANs
Ports, VLANs, and L3 Interfaces
Access Ports and Trunk Ports 802.1Q support
Explicit and Implicit VLANs
Configuring SSR Bridging Functions
Configuring Address-based or Flow-based Bridging
Address-Based Bridge Table Flow-Based Bridge Table
SSR
More ports for a particular Vlan
Configuring Spanning Tree
Adjusting Spanning-Tree Parameters
Assigning Port Costs
Setting the Bridge Priority
Setting a Port Priority
Defining the Maximum Age
Adjusting Bridge Protocol Data Unit Bpdu Intervals
Adjusting the Interval between Hello Times
Defining the Forward Delay Interval
Adding Ports to a Vlan
Configuring a Port- or Protocol-Based Vlan
Configuring Vlan Trunk Ports
Creating a Port or Protocol Based Vlan
Configuring Layer-2 Filters
Configuring VLANs for Bridging
Creating an IP or IPX Vlan
Configuration Examples
Monitoring Bridging
Next, assign ports to the ‘RED’ Vlan
Creating a non-IP/non-IPX Vlan
Overview
Chapter SmartTRUNK Configuration Guide
Add Physical Ports to the SmartTRUNK
Configuring SmartTRUNKs
Creating a SmartTRUNK
Specify Traffic Distribution Policy Optional
Monitoring SmartTRUNKs
St.2 St.4 Router Switch Server
Example Configurations
SmartTRUNK Configuration Guide
Page
Virtual Channels
Chapter ATM Configuration Guide
ATM Overview
Atm create vcl port port list
Service Class Definition
Creating a Virtual Channel
Creating a Service Class Definition
Applying a Service Class Definition
Atm set port port list pdh-cell-scramble on off
Cell Scrambling
Enabling Cell Scrambling
Atm set port port list cell-mapping direct plcp
Cell Mapping
Selecting the Cell Mapping Format
Pdh-cell-scramble onoff
Atm set port port list vpi-bits num
Setting the Bit Allocation for VPI
Creating a Non-Zero VPI
Atm show vpl port port list all-ports
Displaying ATM Port Information
Atm show serviceall
B3ZS
Atm show port-settings port list all-ports
G751 is used for E3 framing
Esf indicates extended super frame and is used
For T1 framing
G832 is used for E3 framing
Consider the following network configuration
ATM Sample Configuration
Defining an ATM Service Class
Configuring an Interface on an Ethernet Port
Configuring an IP Route
Applying an ATM Service Class
Configuring an Interface on an ATM Port
Ssr1config# ip add route 11.1.2.0/24 gateway
ATM Sample Configuration
Chapter Packet-over-SONET Configuration Guide
Configuring IP Interfaces for PoS Links
Configuring Packet-over-SONET Links
Configuring Automatic Protection Switching
Configuring Working and Protecting Ports
Specifying Bit Error Rate Thresholds
Threshold
Specify signal degrade BER
Threshold Specify signal failure BER
Monitoring PoS Ports
APS PoS Links Between SSRs
This section shows example configurations for PoS links
Following is the configuration for router a
Following is the configuration for router B
Router So.6.1 So-1 40.1.1.1/16
PoS Link Between the SSR and a Cisco Router
Router So.6.1
Bridging and Routing Traffic Over a PoS Link
Page
Dhcp Overview
Configuration Guide
Chapter
Client Parameters
Configuring Dhcp
Configuring an IP Address Pool
Configuring Client Parameters
Grouping Scopes with a Common Interface
Configuring a Static IP Address
Monitoring the Dhcp Server
Configuring Dhcp Server Parameters
Updating the Lease Database
Define a static IP address for
Dhcp Configuration Examples
Define Dhcp network parameters for the scope ‘scope1’
Define an IP address pool for addresses 10.1.1.10 through
Configuring Secondary Subnets
Include ‘scope2’ in the superscope ‘super1’
Secondary Subnets and Directly-Connected Clients
Interacting with Relay Agents
Define the address pool for ‘scope1’
Page
Unicast Routing Protocols
Chapter IP Routing Configuration Guide
IP Routing Protocols
Multicast Routing Protocols
Configuring IP Interfaces and Parameters
Specifying Ethernet Encapsulation Method
Configuring IP Interfaces to Ports
Configuring IP Interfaces for a Vlan
Configuring Jumbo Frames
Unresolved MAC Addresses for ARP Entries
Configuring Address Resolution Protocol ARP
Configuring ARP Cache Entries
To clear the entire ARP table
Configuring Proxy ARP
Configuring Reverse Address Resolution Protocol Rarp
Defining MAC-to-IP Address Mappings
Specifying IP Interfaces for Rarp
Monitoring Rarp
Configuring DNS Parameters
Configuring IP Services Icmp
Configuring IP Helper
Configuring Direct Broadcast
Monitoring IP Parameters
Configuring Denial of Service DOS
System show dns
Configuring Router Discovery
Arp show all
Interface show ip
Ssrconfig# rdisc add address
Ssr# rdisc show all
To display router discovery information
Assigning IP/IPX Interfaces
Vrrp Overview
Configuring Vrrp
Following is the configuration file for Router R1 in Figure
Basic Vrrp Configuration
Backup
Configuration of Router R1
Following is the configuration file for Router R2 in Figure
Symmetrical Configuration
Configuration for Router R2
Symmetrical Vrrp Configuration
Master for VRID=1 Master for VRID=2 Backup for VRID=2
Configuration of Router R2
Multi-Backup Configuration
Multi-Backup Vrrp Configuration
Configuration of Router R1
Virtual Router Default Priority Configured Priority
Following is the configuration file for Router R3 in Figure
Additional Configuration
Configuration of Router R3
Setting Pre-empt Mode
Setting the Backup Priority
Setting the Advertisement Interval
Ip-redundancy trace
Setting an Authentication Key
Monitoring Vrrp
Ssr# ip-redundancy show vrrp interface int1
Ip-redundancy show
Ssr# ip-redundancy show vrrp 1 interface int1 verbose
Vrrp Configuration Notes
104
RIP Overview
Chapter RIP Configuration Guide
Configuring RIP
Enabling and Disabling RIP
Configuring RIP Interfaces
Configuring RIP Parameters
Specify that RIP V2 packets
Set the authentication method
Characters Set the authentication method
To RIP
Monitoring RIP
Configuring RIP Route Preference
Configuring RIP Route Default-Metric
Configuration Example
110
Ospf Overview
Ospf
Ospf Multipath
Configuring Ospf
Ospf Interface Parameters
Configuring Ospf Interface Parameters
Enabling Ospf
Port Media Type Speed Ospf Default Cost
Default Cost of an Ospf Interface
Ospf Default Cost Per Port Type
Add an interface to an Ospf area
Configuring an Ospf Area
Create an Ospf area
Add a network to an Ospf area for
Configuring Ospf Area Parameters
Creating Virtual Links
Add a stub host to an Ospf area
Set virtual link
Configuring Ospf for Different Types of Interfaces
Create a virtual
Link
Monitoring Ospf
Show information about all interfaces
Monitor Ospf error conditions
Configured for Ospf
Show Ospf errors
Shows information about Ospf Border
Ospf Configuration Examples
Routes Show Ospf timers
Shows information about all valid next
Exporting All RIP, Interface & Static Routes to Ospf
Exporting All Interface & Static Routes to Ospf
Create a Static export source
Create a Ospf export destination for type-1 routes
Create a Ospf export destination for type-2 routes
Create a RIP export source
Create OSPF-ASE export source
Create a RIP export destination
Create Ospf export source
R10
BGP Overview
Chapter BGP Configuration Guide
SSR BGP Implementation
Basic BGP Tasks
Ip-router global set autonomous-system num1 loops num2
Setting the Autonomous System Number
Setting the Router ID
Configuring a BGP Peer Group
Autonomous-system number
Where
Starting BGP
Using AS-Path Regular Expressions
Adding and Removing a BGP Peer
130
To import MCI routes with a preference
Using the AS Path Prepend Feature
AS-Path Regular Expression Examples
Following is an example
BGP Configuration Examples
BGP Peering Session Example
Physical Link Peering Relationship
CLI configuration for router SSR1 is as follows
AS-1 AS-2
Gated.conf file for router SSR2 is as follows
Ibgp Configuration Example
CLI configuration for router SSR2 is as follows
Gated.conf file for router SSR1 is as follows
Ibgp Routing Group Example
AS-64801
Sample Ibgp Configuration Routing Group Type
Following lines in the Cisco router configure Ospf
Ibgp Internal Group Example
Sample Ibgp Configuration Internal Group Type
Illustrates a sample Ibgp Internal group configuration
SmartSwitch Router User Reference Manual 141
Configuration for router C2 a Cisco router is as follows
Ebgp Multihop Configuration Example
Configuration for router C1 a Cisco router is as follows
Physical Link
AS-64800
CLI configuration for router SSR3 is as follows
Gated.conf file for router SSR4 is as follows
CLI configuration for router SSR4 is as follows
Community Attribute Example
Gated.conf file for router SSR3 is as follows
Sample BGP Configuration Specific Community
Sample BGP Configuration Well-Known Community
, router SSR11 has the following configuration
, router SSR13 has the following configuration
, router SSR14 has the following configuration
, router SSR10 has the following configuration
SmartSwitch Router User Reference Manual 151
Local Preference Examples
Sample BGP Configuration Local Preference
For router SSR13, local-prefis set to
Using the local-pref Option
Using the set-pref Option
Multi-Exit Discriminator Attribute Example
Sample BGP Configuration MED Attribute
AS-64901
Router SSR6 has the following CLI configuration
Ebgp Aggregation Example
AS-64900
Route Reflection Example
Router SSR8 has the following CLI configuration
Router SSR9 has the following CLI configuration
AS-64902
Shows a sample configuration that uses route reflection
SmartSwitch Router User Reference Manual 159
160
Route Import and Export Policy Overview
Chapter Routing Policy Configuration Guide
Preference
Default Preference Values
Preference Defined by CLI Command Default
Import-Source
Import Policies
Export-Source
Export Policies
Route-Filter
Export-Destination
Specifying a Route Filter
Aggregates and Generates
Aggregate-Source
Aggregate-Destination
Authentication Methods
Authentication
Authentication Keys and Key Management
Configuring Simple Routing Policies
Redistributing Directly Attached Networks
Redistributing Static Routes
Redistributing Aggregate Routes
Redistributing RIP into RIP
Redistributing RIP into Ospf
Redistributing Ospf to RIP
Example 1 Redistribution into RIP
Simple Route Redistribution Examples
To redistribute aggregate
Routes into Ospf
Example 2 Redistribution into Ospf
Exporting a Given Static Route to All RIP Interfaces
Exporting All Static Routes to All RIP Interfaces
174
Configuring Advanced Routing Policies
176
Creating an Export Source
Creating an Export Destination
Destination Create an Ospf import
Creating an Import Source
Creating a Route Filter
Create a RIP import
Creating an Aggregate Route
Example 1 Importing from RIP
Creating an Aggregate Destination
Creating an Aggregate Source
Examples of Import Policies
R41
182
Rip add source-gateways 140.1.1.41 rip add trusted-gateways
Example 2 Importing from Ospf
185 Routing Policy Configuration
Importing a Selected Subset of OSPF-ASE Routes
Example 1 Exporting to RIP
Examples of Export Policies
188
Exporting a Given Static Route to a Specific RIP Interface
190
Exporting Aggregate-Routes into RIP
Example 2 Exporting to Ospf
SmartSwitch Router User Reference Manual 193
194
SmartSwitch Router User Reference Manual 195
196
Igmp Overview
Chapter Multicast Routing Configuration Guide
IP Multicast Overview
Dvmrp Overview
Configuring Igmp Response Wait Time
Configuring Igmp
Configuring Igmp on an IP Interface
Configuring Igmp Query Interval
Ship to a specific group
Configuring Dvmrp
Configuring Per-Interface Control of Igmp Membership
Configuring Static Igmp Groups
Starting and Stopping Dvmrp
Configuring Dvmrp on an Interface
Configuring Dvmrp Parameters
Configuring Dvmrp TTL & Scope
Configuring the Dvmrp Routing Metric
Membership details running Igmp
Configuring a Dvmrp Tunnel
Monitoring Igmp & Dvmrp
Shows all the interfaces
Registered by Igmp Show Igmp status on a Vlan
Memberships on a port basis Show all Igmp timers
Shows all Igmp group
Show information about multicasts
SmartSwitch Router User Reference Manual 205
206
Chapter IP Policy-Based Forwarding Configuration Guide
Associating the Profile with an IP Policy
Configuring IP Policies
Defining an ACL Profile
Creating Multi-Statement IP Policies
Setting the IP Policy Action
Applying an IP Policy to Locally Generated Packets
Setting Load Distribution for Next-Hop Gateways
Applying an IP Policy to an Interface
Routing Traffic to Different ISPs
IP Policy Configuration Examples
Using an IP Policy to Prioritize Service to Customers
Prioritizing Service to Customers
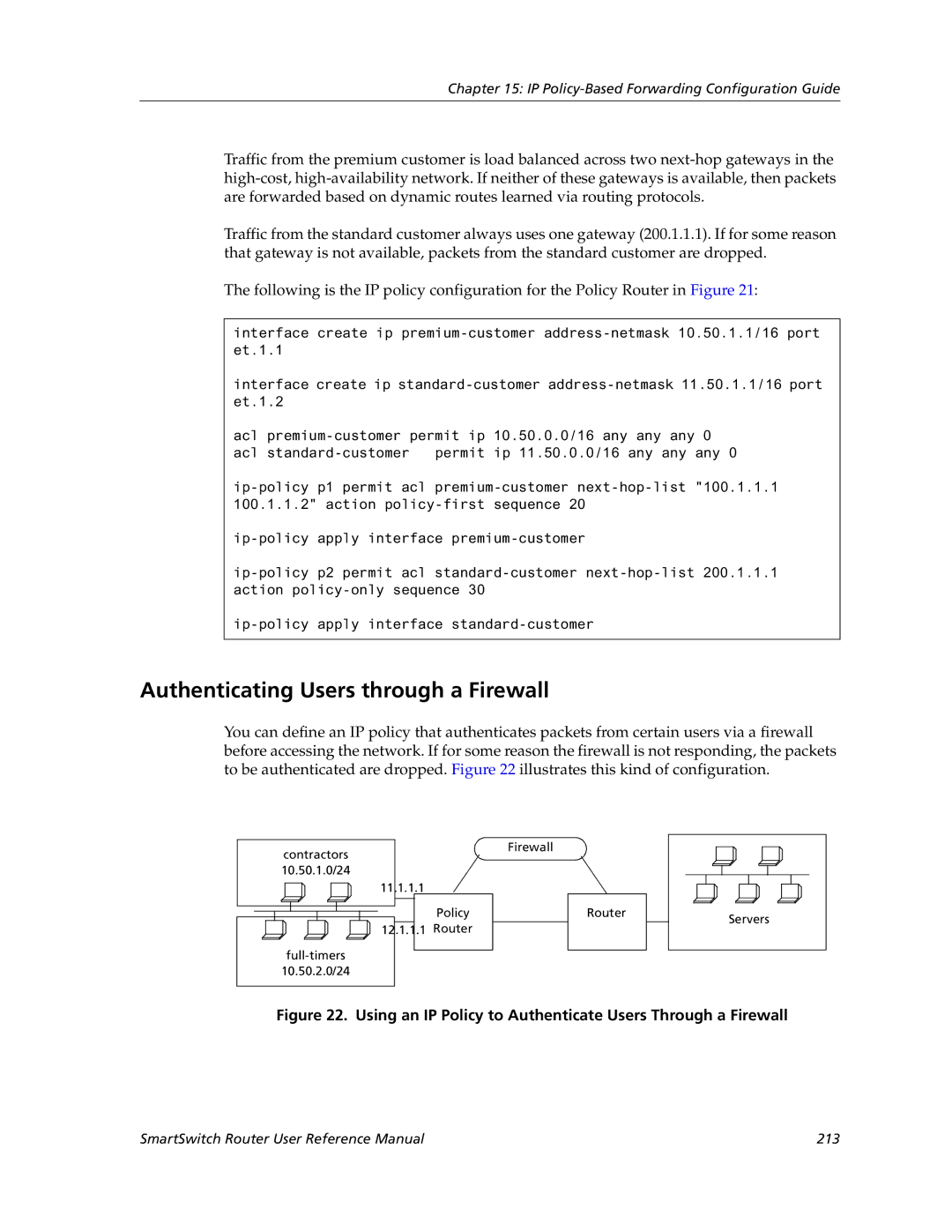
Using an IP Policy to Authenticate Users Through a Firewall
Authenticating Users through a Firewall
Selecting Next Hop Gateway from IP Packet Information
Firewall Load Balancing
Monitoring IP Policies
Following is the configuration for Policy Router 1 in Figure
Ssr# ip-policy show policy-name p1
SmartSwitch Router User Reference Manual 217
218
Chapter Network Address Translation Configuration Guide
Setting Inside and Outside Interfaces
Configuring NAT
Dynamic
Setting NAT Rules
Forcing Flows through NAT
Static
NAT and DNS
Managing Dynamic Bindings
Specify the FTP control port
Specify the FTP session timeout
NAT and Icmp Packets
NAT and FTP
Next, define the interfaces to be NAT inside or outside
Static Configuration
This section shows examples of NAT configurations
Monitoring NAT
Using Static NAT
Dynamic Configuration
Using Dynamic NAT
Using Dynamic NAT with IP Overload
Dynamic NAT with IP Overload PAT Configuration
DNS
Dynamic NAT with DNS
Dynamic NAT with Outside Interface Redundancy
Using Dynamic NAT with DNS
Using Dynamic NAT with Matching Interface Redundancy
Chapter Web Hosting Configuration Guide
Adding Servers to the Load Balancing Group
Configuring Load Balancing
Load Balancing
Creating the Server Group
Session Persistence
Sticky Minutes
Persistence Default Binding Level Timeout
Specifying a Connection Threshold
Optional Group or Server Operating Parameters
Specifying Load Balancing Policy
Verifying Servers and Applications
Specify application verification
Setting Server Status
Verifying Extended Content
Load Balancing and FTP
Allowing Access to Load Balancing Servers
Setting Timeouts for Load Balancing Mappings
Displaying Load Balancing Information
Configuration Examples
10.1.1.4 Internet Web requests
Web requests forwarded to One of the servers Router
Domain Name Virtual IP TCP Port Real Server
207.135.89.16 207.135.89.17 207.135.89.18 207.135.89.50
Virtual IP Address Ranges
Session and Netmask Persistence
Creating the Cache Group
Configuring Web Caching
Web Caching
Redirecting Http Traffic on an Interface
Specifying the Clients for the Cache Group Optional
Redirected to cache servers
Not redirected to cache servers
Bypassing Cache Servers
Configuration Example
Other Configurations
Proxy Server Redundancy
Distributing Frequently-Accessed Sites Across Cache Servers
Monitoring Web-Caching
Show cache server information
Show caching policy information
RIP Routing Information Protocol
Chapter IPX Routing Configuration Guide
IPX Routing Overview
SAP Service Advertising Protocol
IPX Addresses
Configuring IPX RIP & SAP
Creating IPX Interfaces
Configuring IPX Interfaces for a Vlan
Configuring IPX Interfaces and Parameters
Configuring IPX Addresses to Ports
Configuring Secondary Addresses on an IPX Interface
Enabling SAP
Configuring IPX Routing
Specifying IPX Encapsulation Method
Enabling IPX RIP
Creating an IPX Access Control List
Configuring Static Routes
Configuring Static SAP Table Entries
Controlling Access to IPX Networks
Creating an IPX SAP Access Control List
Creating an IPX Type 20 Access Control List
Creating an IPX RIP Access Control List
Creating an IPX GNS Access Control List
Monitoring an IPX Network
258
Chapter Access Control List Configuration Guide
Defining Selection Criteria in ACL Rules
ACL Basics
SmartSwitch Router User Reference Manual 261
Implicit Deny Rule
How ACL Rules are Evaluated
Allowing External Responses to Established TCP Connections
Editing ACLs Offline
Following ACL illustrates this feature
Creating and Modifying ACLs
Maintaining ACLs Using the ACL Editor
These uses of ACLs are described in the following sections
Using ACLs
Applying ACLs to Interfaces
Applying ACLs to Layer-4 Bridging Ports
Applying ACLs to Services
SSR Feature ACL Profile Usage
Using ACLs as Profiles
Using Profile ACLs with the Traffic Rate Limiting Facility
Using Profile ACLs with the IP Policy Facility
Using Profile ACLs with Dynamic NAT
Using Profile ACLs with the Web Caching Facility
Using Profile ACLs with the Port Mirroring Facility
Preventing Web Objects From Being Cached
Redirecting Http Traffic to Cache Servers
Enabling ACL Logging
Monitoring ACLs
Security Overview
Chapter Security Configuration Guide
Configuring Radius
Configuring SSR Access Security
Monitoring Tacacs
Configuring Tacacs
Monitoring Radius
Configuring Tacacs Plus
Monitoring Tacacs Plus
Configuring Passwords
Layer-2 Security Filters
Configuring Layer-2 Address Filters
Configure a destination static
Configuring Layer-2 Port-to-Address Lock Filters
Configuring Layer-2 Static Entry Filters
Configure a source static
Port filter
Configuring Layer-2 Secure Port Filters
Configure a source secure port
Configure a destination secure
Layer-2 Filter Examples
Monitoring Layer-2 Security Filters
Port-to-Address Lock Examples
Static Entries Example
Example 2 Secure Ports
Layer-3 Access Control Lists ACLs
Sample Vlan for Layer-4 bridging
Layer-4 Bridging and Filtering
Enabling Layer-4 Bridging on the Vlan
For example, to enable Layer-4 Bridging on the blue Vlan
Creating a Port-Based Vlan for Layer-4 Bridging
Placing the Ports on the Same Vlan
Applying a Layer-4 Bridging ACL to a Port
SmartSwitch Router User Reference Manual 289
290
QoS & Layer-2/Layer-3/Layer-4 Flow Overview
Chapter QoS Configuration Guide
Layer-2 and Layer-3 & Layer-4 Flow Specification
SSR Queuing Policies
Traffic Prioritization for Layer-2 Flows
Precedence for Layer-3 Flows
Control
Configuring Layer-2 QoS
802.1p Priority Mapping
Removing or Disabling Per-Port Priority Map
Creating and Applying a New Priority Map
Displaying Priority Map Information
Configuring IP QoS Policies
Traffic Prioritization for Layer-3 & Layer-4 Flows
Specifying Precedence for an IP QoS Policy
Configuring IPX QoS Policies
Setting an IP QoS Policy
Setting an IPX QoS Policy
Specifying Precedence for an IPX QoS Policy
Configuring SSR Queueing Policy
Allocating Bandwidth for a Weighted-Fair Queuing Policy
ToS Rewrite
Weighted Random Early Detection Wred
Tos-rewrite
Configuring ToS Rewrite for IP Packets
Tos-precedence-rewrite = 5 tos-rewrite =
Monitoring QoS
Rate Limiting Modes
Limiting Traffic Rate
Apply a per-flow rate limit
Per-Flow Rate Limiting
Port Rate Limiting
Policy
Limit outgoing traffic on a port
Aggregate Rate Limiting
Define a port rate limit policy to
Limit incoming traffic on a port
Per-Flow Rate Limiting
Example Configurations
Aggregate Rate Limiting
Displaying Rate Limit Information
Performance Monitoring Overview
Chapter Performance Monitoring Guide
Particular MAC address Show info about multicasts
Show port error statistics
Show information about the master
MAC table Show information about a
Only IP ACLs can be specified for port mirroring
Configuring the SSR for Port Mirroring
Monitoring Broadcast Traffic
312
Rmon Overview
Rmon
Example of Rmon Configuration Commands
Configuring and Enabling Rmon
Lite Rmon Groups
Rmon Groups
Professional Rmon Groups
Standard Rmon Groups
Control Tables
Using Rmon
Configuring Rmon Groups
Size owner string status enabledisable
Enabledisable
Num status enabledisable
String status enabledisable
Rmon user-history-control index index-number
Port port owner string status enabledisable
Oid type absolutedelta status enabledisable
Rmon protocol-distribution index index-number
Displaying Rmon Information
Rmon CLI Filters
01000CCCCCCC
Following shows Host table output without a CLI filter
Creating Rmon CLI Filters
Troubleshooting Rmon
Using Rmon CLI Filters
326
Ssr# rmon show status
Allocating Memory to Rmon
Rmon set memory number
Lfap
Configuring the Lfap Agent on the SSR
Cabletron’s Traffic Accounting Services
Allow external ACL policy control
Start the Lfap protocol on the SSR
Monitoring the Lfap Agent on the SSR
Command Displays
WAN Overview
WAN
Static Addresses
Configuring WAN Interfaces
Primary and Secondary Addresses
Static, Mapped, and Dynamic Peer IP/IPX Addresses
Dynamic Addresses
Following command line displays an example for a Vlan
Following command line displays two examples for PPP
Mapped Addresses
Packet Compression
Following command line displays an example for PPP
Forcing Bridged Encapsulation
Link Integrity
Example Configurations
Average Packet Size
Nature of the Data
Packet Encryption
WAN Quality of Service
Random Early Discard RED
Weighted-Fair Queueing
Source Filtering and ACLs
Congestion Management
Adaptive Shaping
Frame Relay Overview
Virtual Circuits
Permanent Virtual Circuits PVCs
Configuring Frame Relay Interfaces for the SSR
Applying a Service Profile to an Active Frame Relay WAN Port
Setting up a Frame Relay Service Profile
Monitoring Frame Relay WAN Ports
Frame Relay Port Configuration
344
Use of LCP Magic Numbers
Configuring PPP Interfaces
Point-to-Point Protocol PPP Overview
Defining the Type and Location of a PPP Interface
Setting up a PPP Service Profile
Compression on MLP Bundles or Links
Applying a Service Profile to an Active PPP Port
Configuring Multilink PPP Bundles
Monitoring PPP WAN Ports
PPP Port Configuration
Ssrconfig# ppp apply service profile2 ports hs.5.1
Simple Configuration File
WAN Configuration Examples
Multi-router WAN configuration
Multi-Router WAN Configuration
Following configuration file applies to Router R2
Router R1 Configuration File
Following configuration file applies to Router R1
Router R2 Configuration File
Following configuration file applies to Router R4
Router R3 Configuration File
Following configuration file applies to Router R3
Router R4 Configuration File
Following configuration file applies to Router R6
Router R5 Configuration File
Following configuration file applies to Router R5
Router R6 Configuration File
SmartSwitch Router User Reference Manual 355
356
Line Cards Available Prior to the 3.0 Firmware Release
Appendix a New Features Supported on Line Cards
Introduction
SSR 8000/8600 Line Cards
WFQ
Pre-3.0 SSR Firmware Line Card Part Number Features
Pre-3.0
Line Card Part Firmware Number Features
Listed 3.0 Features
Line Cards Introduced at the 3.1 Firmware Release T-Series
POS OC-12cSMF SSR-ATM29-02 ATM OC-3c SSR-ATM31-02 ATM OC-12c
Routing Table on Pre-3.0 Line card
AAs Line Cards
SSR 2000 Line Cards
SSR-2-LX70
AAs -- Chassis
SSR-2-LX70-AA
New Features that Require Specific Line Cards
Network Address Translation
Page
Load Balancing Lsnat
Layer 4 Bridging
Per-Protocol Vlan
Port Rate Limiting
QoS Rate Limiting
Multiple IPX Encapsulation
ToS Rewrite
Established Bit ACL
Jumbo Frames
Weighted Random Early Detection Wred
Port Interface Ingress Port Egress Port Features Base
Summary
Example
Identifying a Line Card
Multiple IPX Encapsulation Interface AA/T-series
Non -AA Line Card
372