Chapter 4 Remote Access VPN Services
Creating Remote Access VPN Policies
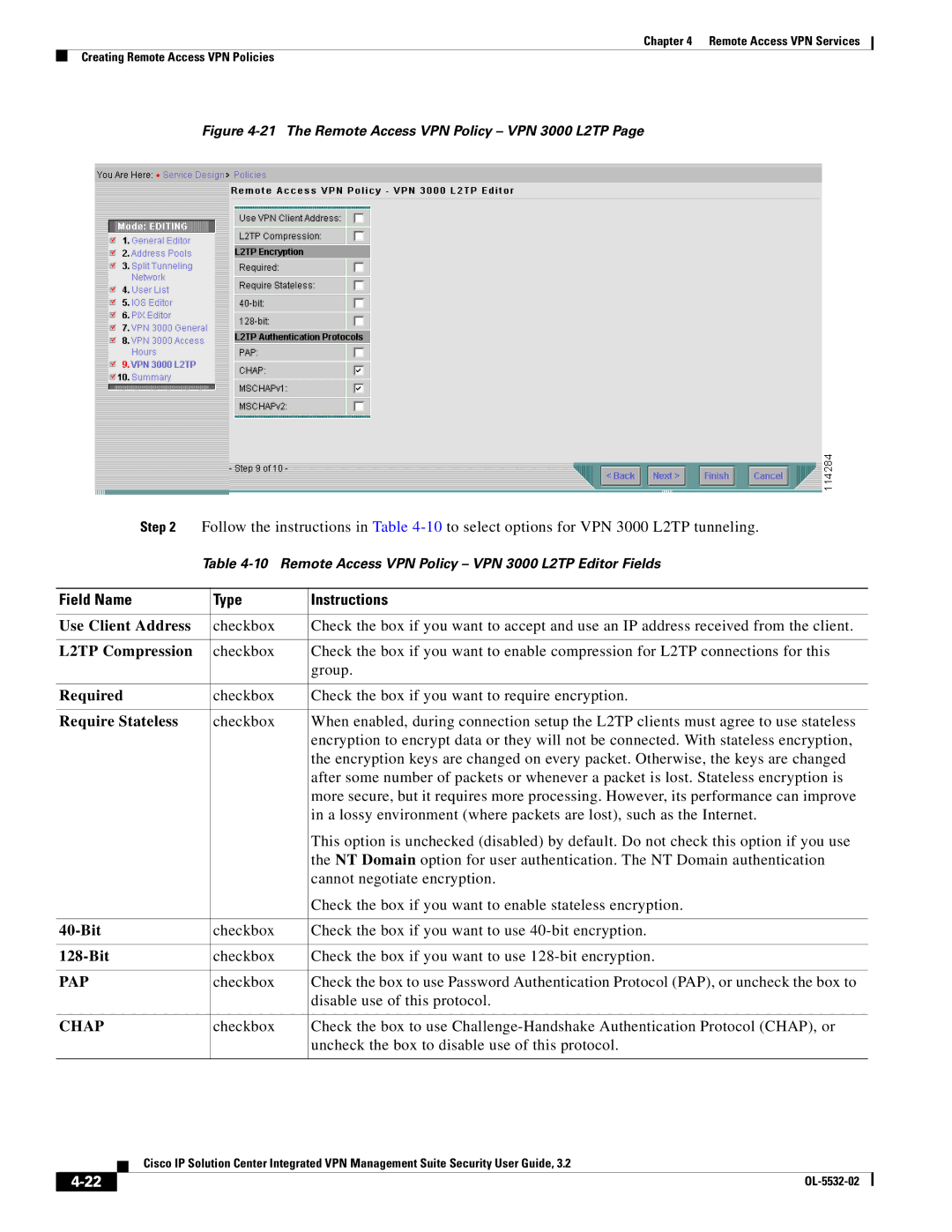
Figure 4-21 The Remote Access VPN Policy – VPN 3000 L2TP Page
Step 2 | Follow the instructions in Table | ||
| Table | ||
|
|
|
|
Field Name |
| Type | Instructions |
|
|
|
|
Use Client Address |
| checkbox | Check the box if you want to accept and use an IP address received from the client. |
|
|
|
|
L2TP Compression |
| checkbox | Check the box if you want to enable compression for L2TP connections for this |
|
|
| group. |
|
|
|
|
Required |
| checkbox | Check the box if you want to require encryption. |
|
|
|
|
Require Stateless |
| checkbox | When enabled, during connection setup the L2TP clients must agree to use stateless |
|
|
| encryption to encrypt data or they will not be connected. With stateless encryption, |
|
|
| the encryption keys are changed on every packet. Otherwise, the keys are changed |
|
|
| after some number of packets or whenever a packet is lost. Stateless encryption is |
|
|
| more secure, but it requires more processing. However, its performance can improve |
|
|
| in a lossy environment (where packets are lost), such as the Internet. |
|
|
| This option is unchecked (disabled) by default. Do not check this option if you use |
|
|
| the NT Domain option for user authentication. The NT Domain authentication |
|
|
| cannot negotiate encryption. |
|
|
| Check the box if you want to enable stateless encryption. |
|
|
|
|
|
| checkbox | Check the box if you want to use |
|
|
|
|
|
| checkbox | Check the box if you want to use |
|
|
|
|
PAP |
| checkbox | Check the box to use Password Authentication Protocol (PAP), or uncheck the box to |
|
|
| disable use of this protocol. |
|
|
|
|
CHAP |
| checkbox | Check the box to use |
|
|
| uncheck the box to disable use of this protocol. |
|
|
|
|
Cisco IP Solution Center Integrated VPN Management Suite Security User Guide, 3.2
| ||
|