Chapter 4 Remote Access VPN Services
Creating Encryption Policies
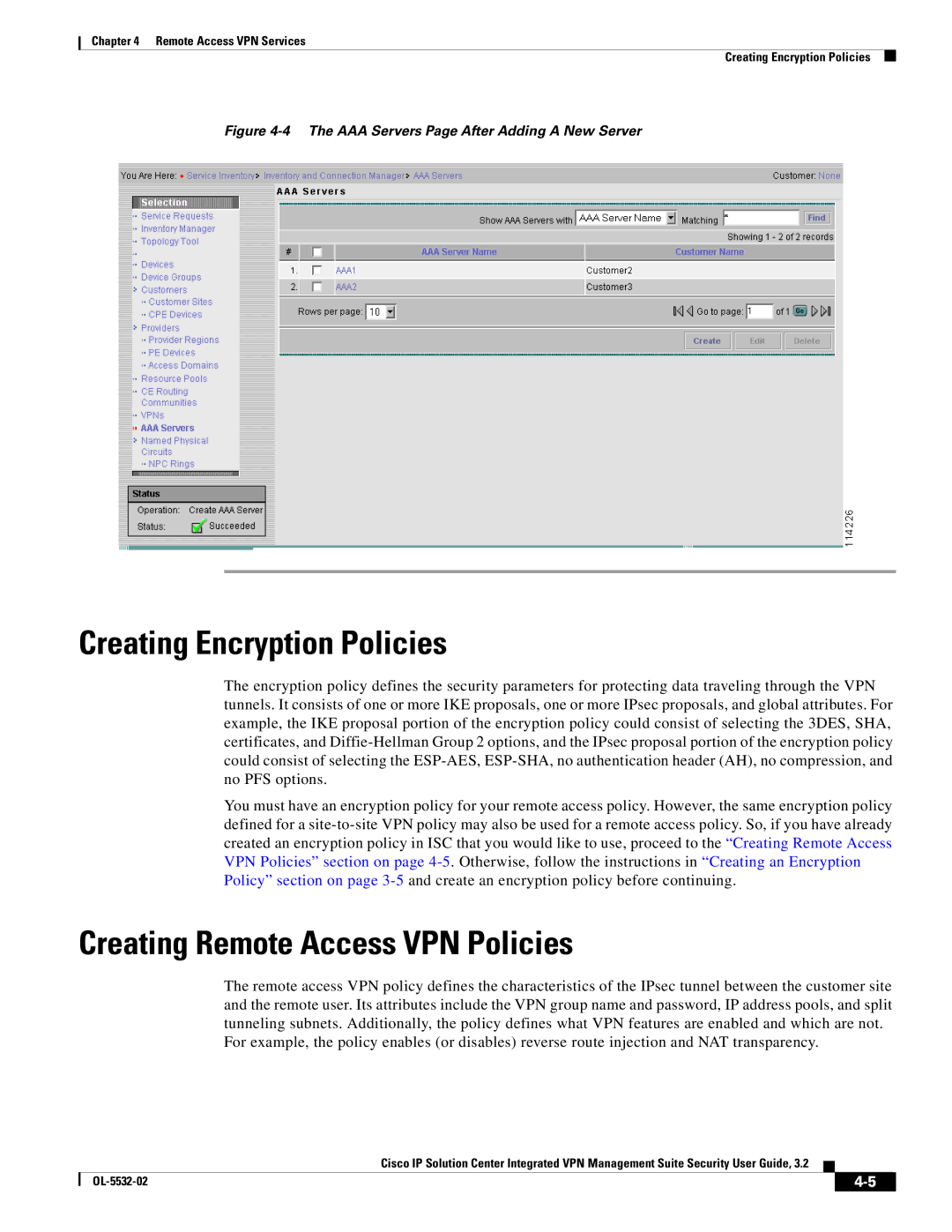
Figure 4-4 The AAA Servers Page After Adding A New Server
Creating Encryption Policies
The encryption policy defines the security parameters for protecting data traveling through the VPN tunnels. It consists of one or more IKE proposals, one or more IPsec proposals, and global attributes. For example, the IKE proposal portion of the encryption policy could consist of selecting the 3DES, SHA, certificates, and
You must have an encryption policy for your remote access policy. However, the same encryption policy defined for a
Creating Remote Access VPN Policies
The remote access VPN policy defines the characteristics of the IPsec tunnel between the customer site and the remote user. Its attributes include the VPN group name and password, IP address pools, and split tunneling subnets. Additionally, the policy defines what VPN features are enabled and which are not.
For example, the policy enables (or disables) reverse route injection and NAT transparency.
Cisco IP Solution Center Integrated VPN Management Suite Security User Guide, 3.2
|
| ||
|
|