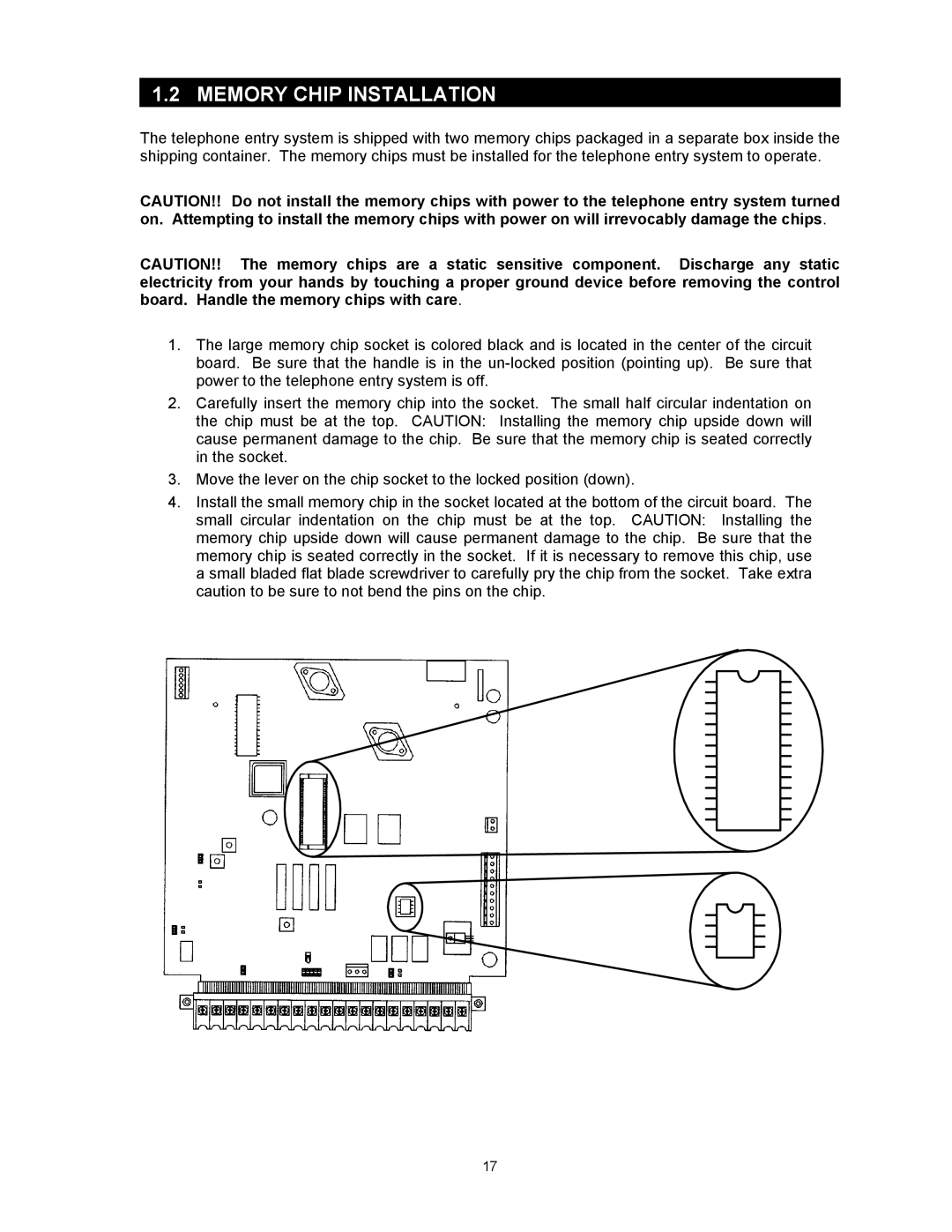
1815, 1803PC, 1817 specifications
DKS Enterprises has established itself as a leading provider of cutting-edge access control solutions, and among its notable offerings are the 1803PC, 1817, and 1815 models. These products stand out in the commercial security landscape, providing businesses with reliable and efficient entry management.The DKS 1803PC is an advanced digital keyless entry system designed for commercial applications. Its primary feature is the easy-to-use keypad interface, which allows users to input their access codes directly. This model is equipped with a robust memory capable of storing up to 100 unique codes, making it suitable for locations with multiple users. Additionally, the 1803PC supports timed access, enabling businesses to set specific entry windows, which enhances security and access control.
The DKS 1817 model takes entry management a step further with its smart technology integration. It features Bluetooth capabilities that allow users to unlock doors via their smartphones, offering convenience and flexibility. The 1817 can be connected to various security devices, such as alarms and surveillance cameras, providing a comprehensive security ecosystem. It also includes a user-friendly mobile app that enables remote management of access permissions, ensuring that business owners can monitor and control entry points effectively from anywhere.
In contrast, the DKS 1815 model caters to businesses looking for a cost-effective yet reliable access solution. This model features a straightforward keypad interface similar to the 1803PC, but it is designed with essential functionalities to meet basic security needs. The 1815 supports up to 50 access codes and is ideal for smaller businesses or limited access areas. Its durable construction ensures longevity and requires minimal maintenance over time.
All three models employ DKS's proprietary technology that emphasizes durability and security. They are built to withstand harsh environmental conditions, making them suitable for both indoor and outdoor use. Each model adheres to stringent safety standards to protect against unauthorized access, ensuring the safety of personnel and assets.
In conclusion, DKS Enterprises' 1803PC, 1817, and 1815 models represent a diverse range of access control solutions tailored for various business needs. Their features focus on ease of use, advanced technology, and reliability, making them an excellent choice for organizations looking to enhance their security measures while streamlining access management.