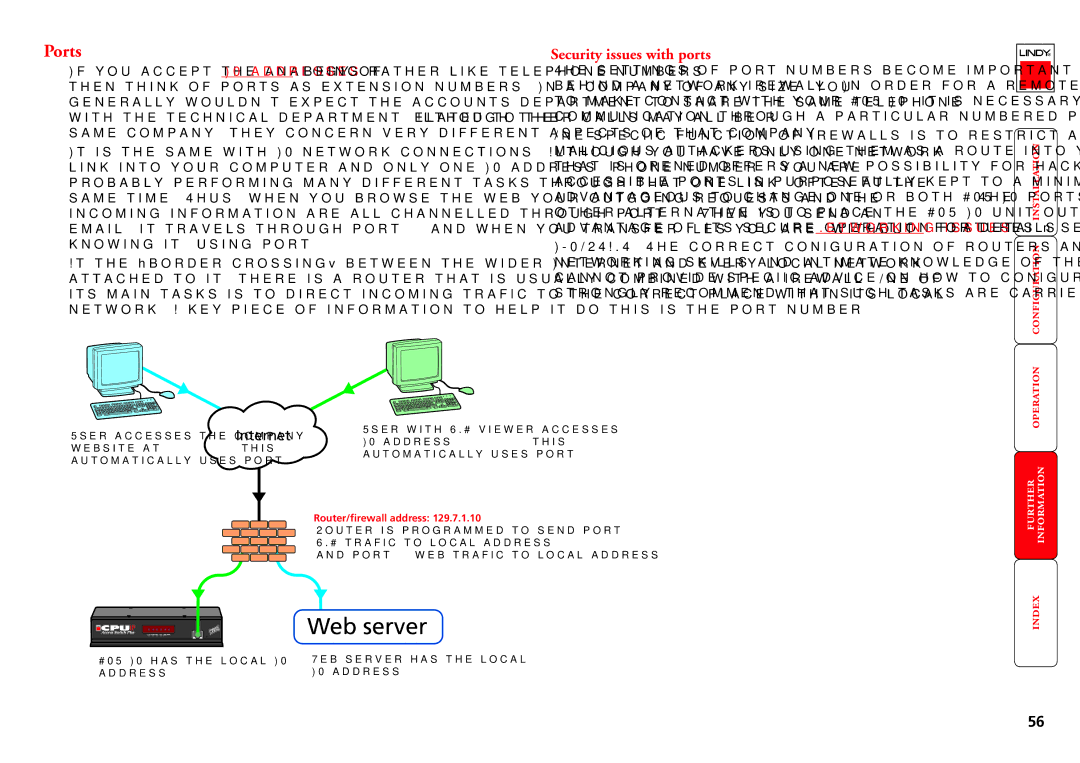
Ports
If you accept the analogy of IP addresses being rather like telephone numbers, then think of ports as extension numbers. In a company of any size, you generally wouldn’t expect the accounts department to share the same telephone with the technical department. Although their calls may all be related to the same company, they concern very different aspects of that company.
It is the same with IP network connections. Although you have only one network link into your computer and only one IP address (phone number), you are probably performing many different tasks through that one link, often at the same time. Thus, when you browse the web your outgoing requests and the incoming information are all channelled through port 80. When you send an email, it travels through port 25 and when you transfer files you are, without knowing it, using port 20.
At the “border crossing” between the wider Internet and every local network attached to it, there is a router that is usually combined with a firewall. One of its main tasks is to direct incoming traffic to the correct place within its local network. A key piece of information to help it do this is the port number:
User accesses the company | Internet | User with VNC viewer accesses | |
IP address: 129.7.1.10 (this | |||
website at: 129.7.1.10 (this |
| ||
| automatically uses port 5900). | ||
automatically uses port 80). |
| ||
|
|
Router/firewall address: 129.7.1.10 Router is programmed to send port 5900 VNC traffic to local address 192.168.0.3 and port 80 web traffic to local address 192.168.0.42
LOC REM VNC 100 LNK PWR | Web server |
IP |
|
Access Switch Plus |
|
CPU IP has the local IP | Web server has the local |
address: 192.168.0.3 | IP address: 192.168.0.42 |
Security issues with ports
The settings of port numbers become important when the CPU IP is situated behind a network firewall. In order for a remote VNC viewer or web browser to make contact with your CPU IP, it is necessary for the firewall to allow communication through a particular numbered port to occur.
One specific function of firewalls is to restrict access to ports in order to prevent malicious attackers using them as a route into your network. Every new port that is opened offers a new possibility for hackers and so the number of accessible ports is purposefully kept to a minimum. In such cases, it may be advantageous to change one or both CPU IP ports to use the same number. The other alternative is to place the CPU IP unit outside the firewall and take full advantage of its secure operation features – see Networking issues for details.
IMPORTANT: The correct configuration of routers and firewalls requires advanced networking skills and intimate knowledge of the particular network. LINDY cannot provide specific advice on how to configure your network devices and strongly recommend that such tasks are carried out by a qualified professional.
56