OMB-483-0901 Rev
Portable Data Recorder
For immediate technical or application assistance
Servicing North America
Servicing Europe
Appendices
How To Use This Manual
Table of Contents
EZ-PostView and ViewXL Calibration
ChartScan User’s Manual
Overview
ChartScan Unit Startup and ChartView Tutorial
Inspect Your System
Unit Startup
Selection Micro Setting Switch #
Verify Voltage Setting
Verify DIP Switch Setting
Install Signal Conditioning Cards
Connect Expansion Chassis option
Install Ieee 488 Interface Communications Card option
Error Condition LED Indicators
Apply Power to ChartScan
DB50 Pin Descriptions
Start ChartView, Configure System, and Collect Data
� = Mouse, Ú= Arrow Keypads , � = PageUp/PageDown Keypads
ChartView Main Window Control Options
Device Interface
Configuration Files
ChartView, Basic Concepts
Acquiring Data with no charting or meter use
ChartView Tutorial
Select Interface Device
Advanced
Moderate
Configure Channels & Alarms
Configure Acquisition
Count
High Speed Setup
Parameter Options
Stop
Review Configuration
Page
ChartScan User’s Manual
General Description
General Information
Data Handling and Triggering
Operational Aspects
Software and Hardware
ChartScan Specifications
Channels
General
Data Storage & Format
Triggers
Digital I/O Interface & Alarms
Calibration
− Notes
Front Panel
Hardware
Rear Panel
Changing the Voltage Setting
Power Aspects
Replacing the AC Power Supply Fuse
Memory Configuration
Expanded Memory Options
Memory Option JP201 JP202
Calibration Memory Write Enable/Disable
RS-232/422 Interface Configurations
Configuring RS-232/422 Parameters
Standard Units, Only
Selection Micro Setting Switch
Early Production Units, Only
Pin # RS-232 Signal Pin Description
Serial Port Pin Connectors
ChartScan to PC Connection RS-232 DB9 Male Pin & Signal
Cable Wiring DB9 Female Pin & Signal
Ethernet Interface Configuration
Specifications
Ieee 488 Interface Configuration Option
Ieee 488 Pinout
Ieee 488 Configuration
Ieee 488 Configuration Settings
Logic Levels
Digital I/O Lines
Digital I/O Port Pinout
Signal Conditioning Cards
External TTL BNC Connectors
Fault Detection
Input Connector
Temperature Range, Accuracy, and Resolution1 Type J
Temperature Units
Digital Filtering
Voltage Range2, Accuracy3 and Resolution
CSN14/LV/ T, B, & S Low Voltage Cards
Voltage Range, Accuracy1 and Resolution
Voltage Range, Accuracy and Resolution
Input Connectors
Number of Inputs
Slot
Device
Connecting the Expansion Chassis
CSN/Relay Card Specifications
Expansion Chassis, CSN/Exp Option
Cross Section of Mounting Block
Device Channel Assignments Slot
Automatic Channel Assignment
Number of Slots Four
Channel-to-System Isolation 500 V peak Dimensions
− Notes
ChartView Software Reference
Three Ways of Using ChartView
Groups, Charts, & Channels
Waiting for Trigger
What ChartView and ChartView Plus Provide
Main Window
ChartView Main Window and Control Options
Channel Information Region
Instrument
Status Indicator Region
Scroll Faster Scroll Slower
Start, Pause, Stop Charts
Main Window Toolbar
Group Select
Normal Edit
Display Configuration
ChartView Software Reference ChartScan User’s Manual
Adjusting Channel Setup for Channel
Manually Creating a Display
Adding a Chart to Group
Adjusting Channel Setup for Channel
Disarm
Channel Configuration
PostView post-acq data viewer
Arm Acquisition
See File Menu Note, immediately following this text
Print Charts
Main Window Pull-Down Menus
File
File Menu Note
Chart
View
Display config
System
Charts
Acquisition
Data
Acquire
Displays the condition of a data acquisition
Ctrl + J manual control
Command Characters Data Destination Timeout Region
Ctrl + U manual
Window
Setup
Device …
Log configuration
ChartScan User’s Manual ChartView Software Reference
Device Expanded Menu obtained with use of the F12 Key
Log Enable
Ctrl+A
Bar Graph, Analog, and Digital Meters
Setup
Overview
Bar Graph Meters
Configuration Note
…. for Analog Meters
Analog Meters
…. For Digital Meters
Digital Meters
Name Function
Reset. This feature does not apply to the Digital Meters
Meter Toolbars
Meter Pull-Down Menus
Configuring a Meter
Meters Configuration Menu
Channel & Alarm Setup Dialog Box
Setup Window
Configure Meter Settings, Function Descriptions
Channel and Alarm Setup, Button Descriptions
Example
Channel Configuration Columns
Alarm Configuration Columns
Acquisition Setup Dialog Box
Acquisition Setup Dialog Box, Normal Mode
Normal Mode, CH1 and CH2 Assigned to a Chart
Burst Mode, Operational Issues
Introduction
Measuring AC Voltage, or AC RMS Voltage
Measuring AC RMS
Data Destination
Data Destination Dialog Box
Why use Auto Re-arm?
Introduction
Chart Setup Wizard
Chart Setup Wizard, Simple Mode
Automatic Chart Setup with Wizard
Bypassing Automatic Chart Setup
EZ-PostView
Introduction
ViewXL
EZ-PostView includes the following features
Reference Note
Range 100 mV
Calibration Setup
Range
Hardware Protected RAM
Non-Volatile Storage of Calibration Constants
Instruction Tool Icon
Using ScanCal
ScanCal Software Application
ScanCal’s Main Window
System Inventory
Interface Parameters
Calibration Without ScanCal
Password
Mode Indicator
Command Active Indicators
Offset Calibration of Main Unit
Calibration of Main Unit
Required Equipment
U132
U128
U129
U130
Gain Calibration of Main Unit
U128
Offset Calibration of Cards
Calibration of Signal Conditioning Cards
Cal Err offset, gain, or temperature sensor out of range
Gain Calibration of Low Volts Cards
ChartScan User’s Manual Calibration
Volts DC Slot #
…to clear the buffer
#1X QC?
C1,1X
Gain Calibration of High Volts Cards
…to clear the buffer
Option c T/C Calibrator/Simulator Method
Cold Junction Calibration
Option a Cold Cell Method
Option b Hot Cell Method
Calibration ChartScan User’s Manual
Enter J3,3,0000.0X J6,3,0000.0X J11,3,0000.0X J14,3,0000.0X
Calibration ChartScan User’s Manual
Appendices
ChartScan User’s Manual
Appendix a
Contents
Command Syntax
Fixed Formats
Command Interpretation
Conflict Errors
Immediate & Deferred Commands
Command Type
Order Function
Deferred Commands, Order of Execution
Command Summary
E002
#make
E000
E001
Mmask
Lchan
Level
Hyst Chan max
Tstart
Rtype
#chans
Stime
− Notes
Type
Command Reference
Command Description Format
Commands
Sleep
Trigger On Command
PRINT#1, OUTPUT07T1,1,0,0X
PRINT#1, OUTPUT07 @X
PRINT#1,OUTPUT07 *BX
Flush Acquisition Buffer
PRINT#1,SPOLL07
INPUT#2, S%
Channel
Clear Channel Configuration
‘ Clear all channels configuration
PRINT#1,OUTPUT07
Input A$
Restore Factory Settings
PRINT#1,OUTPUT07Q?T?Y?X
PRINT#1,ENTER07
PRINT#1, ENTER07 INPUT#2, C%
If C% and 16 then PRINT,ERROR-INVALID Keyword Sleep
Change Calibration Keyword
PRINT#1, OUTPUT07U2X
PRINT#1,OUTPUT07*P01X
Adjust Calibration Card Pots
PRINT#1,OUTPUT07K12345X
PRINT#1,OUTPUT07*P02X
Print #1, SPOLL07
Power-On Reset
PRINT#1,OUTPUT07*RX
While S% and 4 =
PRINT#1, OUTPUT07*RX
Power-Up Settings
‘ Screen shows Q1,7,7,7,0 T1,3,0,0 Y000100
PRINT#1,OUTPUT07*S1X
PRINT#1,OUTPUT07*T0X
Time Stamping
PRINT#1,OUTPUT07*T1X
PRINT#1,OUTPUT07*T2X
Assign Alarm Output
Byte 1 A07 A00 Byte 2 A15 A08 Byte 3 A23 A16 Byte 4 A31 A24
# Alarm Stamping
PRINT#1,OUTPUT07A#1X
PRINT#1,OUTPUT07A#0X
Configure Channels
Volts Card Types
Same as Without temperature Temp
Thermocouple Card Types
These special types are valid only in degrees Celsius
PRINT#1,OUTPUT07X
PRINT#1, OUTPUT07*C
PRINT#1,OUTPUT07 U13X
# Select Card
PRINT#1, OUTPUT07D#12X
Set Relay Make Time
PRINT#1, OUTPUT07M#0X
PRINT#1, OUTPUT07W#32X
PRINT#1, OUTPUT07J1,2,90.0X
End Calibration Mode
PRINT#1, OUTPUT07H17X
PRINT#1, OUTPUT07G17,1X
PRINT#1,ENTER07 INPUT#2,A$ Print A$
? Error Status Query
PRINT#1,CLEAR07
PRINT#1,OUTPUT07E?X
Data Input Formats see Note
Set Data Format
Dddddddd =
Data Output Formats
MM/DD/YY
Dddddddd
PRINT#1, ENTERO7
PRINT#1, OUTPUT07F0,0X
PRINT#1,OUTPUT07C1, 1
PRINT#1, OUTPUT07 U4X
OUTPUT07F#100.5X
# Set Burst Mode Frequency
PRINT#1
OUTPUT07F#15000.0X
PRINT#1, OUTPUT07G17,1
Calibrate Channel Gain
Calibrate Channel Offset
PRINT#1, OUTPUT07I010000.0
Set Scan Interval
Inorm
Acq
PRINT#1, OUTPUT07I#1X
Digital Input Stamping
PRINT#1, OUTPUT07I#0X
PRINT#1, OUTPUT07R1X
Temp
Calibrate Cold Junction Offset
PRINT#1, OUTPUT07J1,2,101.7X
If C% and 16 then
Enter Calibration Mode
PRINT,ERROR-INVALID Keyword Halt
Print #1, ENTER07 INPUT#2, C%
PRINT#1, OUTPUT07T4,5,0,0X
Set Trigger Level
Hyst
PRINT#1, OUTPUT07F0,0X PRINT#1, OUTPUT07L1,100.0,10.0X
Set SRQ Mask
PRINT#1, OUTPUT07M#1X
Set Measuring Mode
Set Event Mask
PRINT#1, OUTPUT07O?X
Set Digital Outputs
PRINT#1 OUTPUT07O?X
Line Input #2, N$ Print N$
Program Trigger Times
PRINT#1, OUTPUT07 V4 V?
? Query
OUTPUT07 V1 X V?
PRINT#1, OUTPUT07 V0 X V?
None
Set Query Terminator
CR LF/EOI LF CR/EOI USER/EOI User
Terminator Type Terminator Description IEEE-488
PRINT#1,OUTPUT07Q?X
R1X R2X R3X
U4X U5X
PRINT#1,OUTPUT07F0,0X
INPUT#1 PRINT#1
QC? Query Card Data
PRINT#1, OUTPUT07 C#5X
PRINT#1, OUTPUT07 QC?X
API Commands Appendix a
PRINT#1,ENTER07 Line INPUT#2, A$
Read Buffered Data
While S% and 8 =
PRINT#1 SPOLL07 INPUT#2, S% Wend PRINT#1,OUTPUT07R1X
Line Input #2, R$ Print R
# Read Last Readings
PRINT#1,OUTPUT07F1,0X
PRINT#1,OUTPUT07R#16X
PRINT#1, OUTPUT07 S140000.0,4/30/93X
Set Real Time Clock
Set Trigger Configuration
PRINT#1, OUTPUT07T1,7,0,1X
PRINT#1, OUTPUT07
000100.0X
PRINT#1, OUTPUT07Y100,10000,0X
User Status
?I?L?P?Q?S?T?Y?
#123101.20,04/24/93
00256
01024
001,1,002,0,003,0 …
Change Calibration Keyword
PRINT#1, OUTPUT07V58X
Set User Terminator
PRINT#1, OUTPUT07V44X
PRINT#1,OUTPUT07@X
PRINT#1, OUTPUT07C1
# Set Average Weight
PRINT#1, OUTPUT07W#64X
OUTPUT07Y0,10,0X
C18-32,3
Execute
PRINT#1,OUTPUT07*C
PRINT#1,OUTPUT07C1-16,1 C17,2
PRINT#1,SPOLL07 INPUT#2,S% Wend PRINT#1,OUTPUT07U6X
Set Counts, or Select Blocks
PRINT#1,OUTPUT07N0 N2
PRINT#1,SPOLL07 INPUT#2,S% Wend PRINT#1,OUTPUT07N0 N1
Appendix B
Memory Allocation
U16
Measuring Modes
U17
Scan time = #channels x #samples/channel + 12 x 520.83 µs
Normal Mode
‘Select Normal mode #16 Samples over which to average
‘Select Normal mode Sample over which to average
‘Select high-speed, single-channel mode
High-Speed, Single-Channel Mode Burst Mode
Condition
PRINT#1,OUTPUT07 U4X
Configuration Requirements
Signal-Conditioning Modules Type Inputs Connector
Channel Configuration
Type Volts AC
CSN14/TC/P Configuring Thermocouple Channels
CSN14/LV/ T, B, or S Configuring Low Volts Channels
Type Volts DC
Configuring the Scan Interval
Scan Configuration
CSN14/HV/S Configuring High Volts Channels
Configuring a Scan
I000010.0,000000.0
Acquisition Configuration
Component Description Required
I000010.0,000000.1
Continuous, Gap-Free Acquisition with Two Timebases
Pre-Trigger State
Configuration Aspects for Programmers Appendix B
Post-Trigger State
Trigger and Stop Events
Post-Stop State
‘@’ character
Selected Temperature Channel High or Low Level
Alarm on or off
External TTL High or Low Level
Time Stamping *T
Alarm Stamping A#
Digital Input Stamping I#
With Alarm Stamping
PRINT#1, OUTPUT07A#1X
With Digital Input Stamping
‘ Enable digital input stamping
Get the response
Acquisition Buffer, a Description
Trigger Block Organization
PRINT#1,ENTER
PRINT#1,OUTPUT 07 U6X
PRINT#1,OUTPUT 07R1X
Multiple Trigger Blocks
Acquisition Buffer Interrogation
Field Response Implication
Field Response Implication
Print
Reading the Acquisition Buffer
PRINT#1,OUTPUT07 U6X
Input
PRINT#1,OUTPUT07R3X
PRINT#1,OUTPUT07R2X
Print #1
Configuring Alarms
Alarm Set Points
Digital Alarm Outputs
Set Point Hysteresis
PRINT#1,OUTPUT07A3,0X ‘Disable channel 3 from digital output
Digital I/O Operation
Appendix C
HLL Register Contents
Using High/Low/Last HLL Registers
Accessing HLL Registers
Example
Example shows how to read only the Last readings
Data Format F
Data Format F
Data Input Formats
Code
Thermocouples
Data Output Formats
Engineering Units Data Format
Examples
Time/Date Stamp
Volts
Hhmnss.t,mm,dd,yy
HHhmstMDYLLhmstMDYll
Binary Data Format
Counts Data Format
010203.5
Configuring Power-Up State
Queries
Query ? Commands
Status Commands
Vuser where 0 user
Status, Event Reporting, and Mask Registers
Theory of Operation
Register Chart Status and Event Reporting Registers
Register Access
Register Chart Mask Registers
Appendix C Registers, Data Formats, & Queries
Event Status Register
Calibration Status Register U2 Command
Error Source Register E? Command
Event Status Enable Register
Bit Location Value Description
Status Byte Register
Ieee 488 Serial Poll Response
Service Request Enable Register
DIO8 MSBit
DI02
Using Status Reporting Registers
Avg
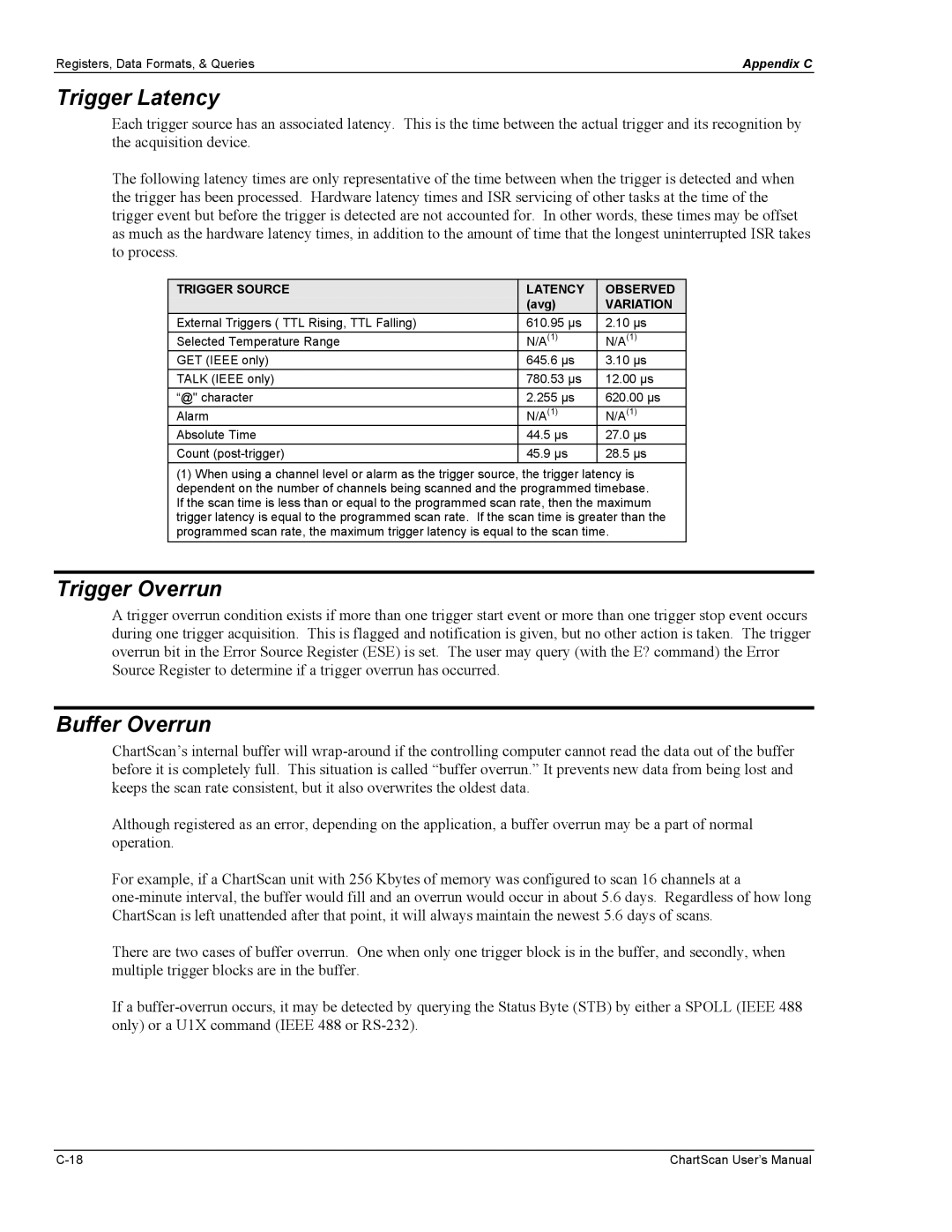
Trigger Latency
Trigger Overrun
Buffer Overrun
Buffer Overrun With Multiple Trigger Blocks
Open Thermocouple/Range Error Checking
Real Time Clock
Buffer Overrun With One Trigger Block
− Notes
Appendix D
ChartScan Program Examples
Reading HLL Data from T/C & Volts Cards using HLL32.BAS
Reading HLL Status using HLL16.BAS
Print #1, Output 07I000001.0,00000.3X
CLS Print The ChartScan is resetting
Print #1, Output 07C1-16,1X Print #1, Output 07C17-32,2X
Print #1, Output 07Y30,1,200X
PRINT#1, Enter INPUT#2, READING$
While INKEY$ = ‘’
Print #1, ENTER07 Output #2, U%
Print #1, Output 07L1,20.0,0X T4,5,0,0X
Print #1, Output 07C1-16,3X Print #1, Output 07C17-32,2X
Print #1, Output 07Y50,100,200X
Print #1, Output 07I000000.1,000000.1X
Operating Alarms using ALARM2.BAS
END if Wend
Print #1, Enter 07 Line Input #2, A$ Print A$
Else
END if
Print #1, Output 07M1X
Using the Ieee 488 SRQ with Alarms using ALAR2SRQ.BAS
On PEN Gosub AlarmHandler
PEN on Print #1, ARM SRQ
Line Input #2, A$
Collecting Data in Binary Format using BINACQ.BAS
Locate
Input #2 Print #1 Output 07O?X
Print #1, Output 07R2X
Print #1, Enter 07 Line Input #2, U$ Print U$
Binary DATA%/10 = C
Print #1, Output 07C1-16,1X Print #1, Output 07C17-32,14X
Collecting Binary-Formatted HLL Data using BINHLL.BAS
Print #1, Clear Print #1, Output 07*S1X
Print #1, Output 07M#0X Print #1, Output 07W#32X
Print STR$VALLAST$ Else
Decode received data and print on screen in Ascii
Print #1, Output 07Q,0,0,8,8,0X
Print #1, Output 07Y1000,20,10X
Print #1, Output 07I000000.3,000000.0X
Print #1, Output 07T1,8,1,0X
Print UA$
Print #1, Output 07U6X
Loop Until UA$=
Print UAT$
Wend Close END
While INKEY$ =
Print #1, Disarm SRQ
Sleep Print #1, ARM SRQ Return
Input #2, EVENT%
Print UA
Print #1, Output 07R3X
Print #1, Output 07C1,14x
Print #1, Output 07M#1X Print #1, Output 07F#20000.0X
Print #1, Output 07Y0,8,0X
Print SCAN$
Print #1, Output 07V32X Q7,0,7,7,1X
For i = 1 to UA% Print #1, Enter
Locate 14, 1 Print Scan i is
Appendix E
− Notes
Box Items
Universal Command Group UCG
Appendix F
Decimal Values 00 to 63 ACG, UCG & LAG
$41
Decimal Values 64 to 127 TAG & SCG
Ascii Code Details
Decimal Values 00 to 31 ACG & UCG Characteristics
Decimal Values 00 to 31 ACG & UCG Descriptions
Dec Name Description Addressed Command Group ACG
Ascii Control Codes 00 to
Space
Decimal Values 32 to 63 LAG
Decimal Values 64 to 95 TAG
Ascii Code SummaryAppendix F
Delete Command
Decimal Values 96 to 127 SCG
DEL
− Notes
Appendix G
LED Indications of Error Conditions LED Indicators
ChartScan Error Messages
Appendix H
Abbreviations Appendix H
Index
ChartScan User’s Manual
WARRANTY/DISCLAIMER
Temperature