CHAPTER2 Ethernet Unit
■Example 5
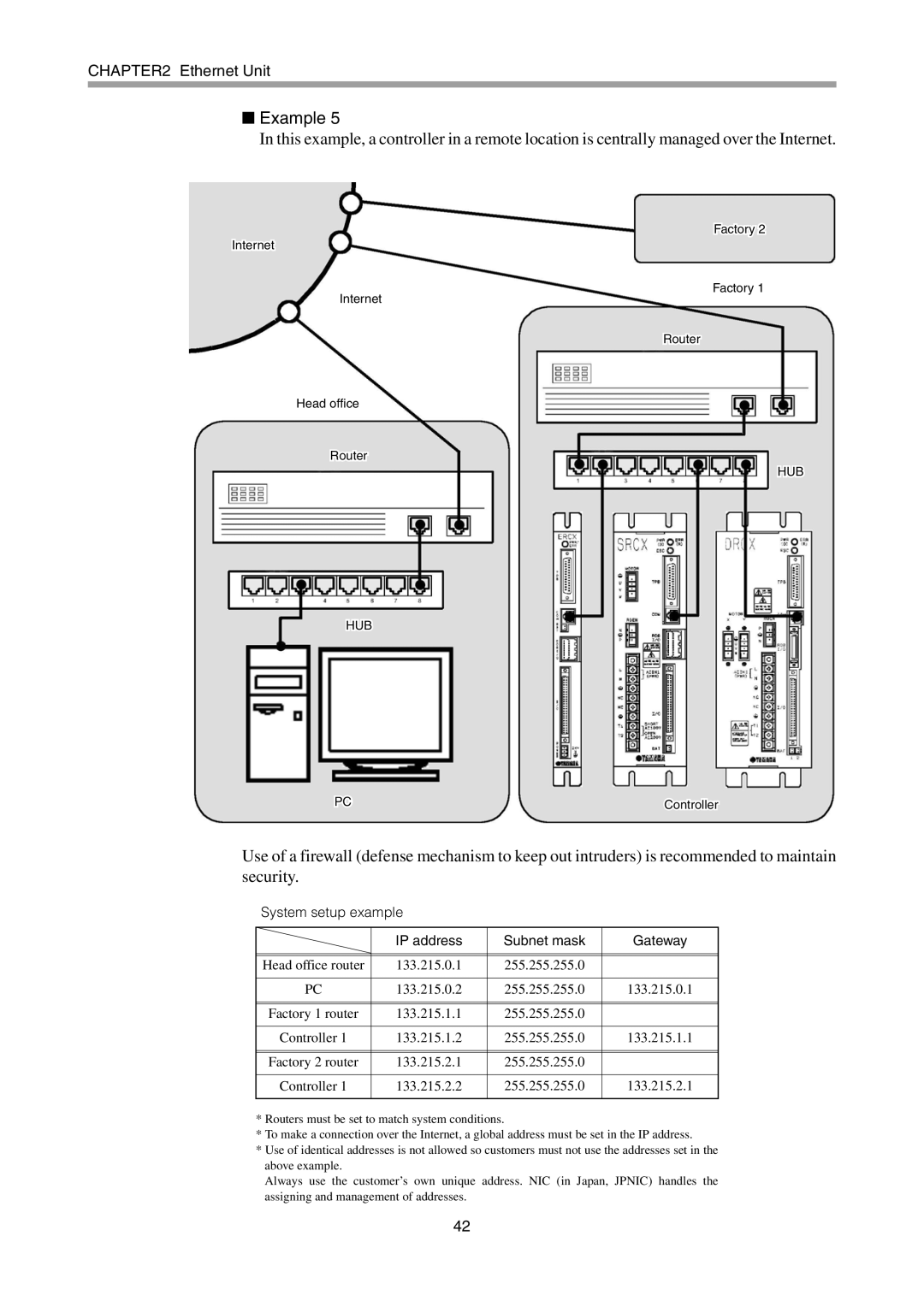
In this example, a controller in a remote location is centrally managed over the Internet.
Internet
Internet
Head office
Router
HUB
PC
Factory 2
Factory 1
Router
HUB
Controller
Use of a firewall (defense mechanism to keep out intruders) is recommended to maintain security.
System setup example
| IP address | Subnet mask | Gateway |
Head office router | 133.215.0.1 | 255.255.255.0 |
|
PC | 133.215.0.2 | 255.255.255.0 | 133.215.0.1 |
Factory 1 router | 133.215.1.1 | 255.255.255.0 |
|
Controller 1 | 133.215.1.2 | 255.255.255.0 | 133.215.1.1 |
Factory 2 router | 133.215.2.1 | 255.255.255.0 |
|
Controller 1 | 133.215.2.2 | 255.255.255.0 | 133.215.2.1 |
|
|
|
|
*Routers must be set to match system conditions.
*To make a connection over the Internet, a global address must be set in the IP address.
*Use of identical addresses is not allowed so customers must not use the addresses set in the above example.
Always use the customer’s own unique address. NIC (in Japan, JPNIC) handles the assigning and management of addresses.
42