|
|
|
|
|
|
|
| Features in |
|
|
| 25 | ||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
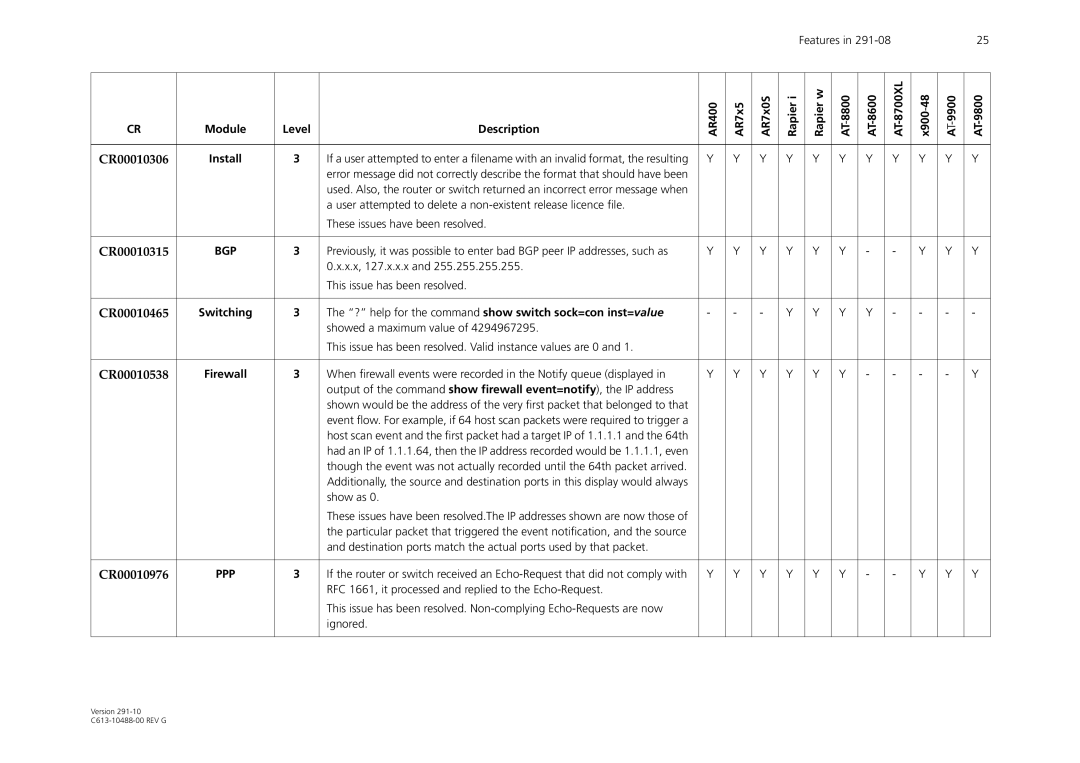
CR | Module | Level | Description | AR400 | AR7x5 | AR7x0S | Rapier i |
| Rapier w | AT8800- |
| x90048- | ||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00010306 | Install | 3 | If a user attempted to enter a filename with an invalid format, the resulting | Y | Y | Y | Y |
| Y | Y | Y |
| Y | Y | Y | Y |
|
|
| error message did not correctly describe the format that should have been |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| used. Also, the router or switch returned an incorrect error message when |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| a user attempted to delete a |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| These issues have been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00010315 | BGP | 3 | Previously, it was possible to enter bad BGP peer IP addresses, such as | Y | Y | Y | Y |
| Y | Y | - |
| - | Y | Y | Y |
|
|
| 0.x.x.x, 127.x.x.x and 255.255.255.255. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00010465 | Switching | 3 | The “?” help for the command show switch sock=con inst=value | - | - | - | Y |
| Y | Y | Y |
| - | - | - | - |
|
|
| showed a maximum value of 4294967295. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. Valid instance values are 0 and 1. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00010538 | Firewall | 3 | When firewall events were recorded in the Notify queue (displayed in | Y | Y | Y | Y |
| Y | Y | - |
| - | - | - | Y |
|
|
| output of the command show firewall event=notify), the IP address |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| shown would be the address of the very first packet that belonged to that |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| event flow. For example, if 64 host scan packets were required to trigger a |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| host scan event and the first packet had a target IP of 1.1.1.1 and the 64th |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| had an IP of 1.1.1.64, then the IP address recorded would be 1.1.1.1, even |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| though the event was not actually recorded until the 64th packet arrived. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Additionally, the source and destination ports in this display would always |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| show as 0. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| These issues have been resolved.The IP addresses shown are now those of |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| the particular packet that triggered the event notification, and the source |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| and destination ports match the actual ports used by that packet. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00010976 | PPP | 3 | If the router or switch received an | Y | Y | Y | Y |
| Y | Y | - |
| - | Y | Y | Y |
|
|
| RFC 1661, it processed and replied to the |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ignored. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Version