|
|
|
|
|
|
|
| Features in |
|
|
| 9 | ||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
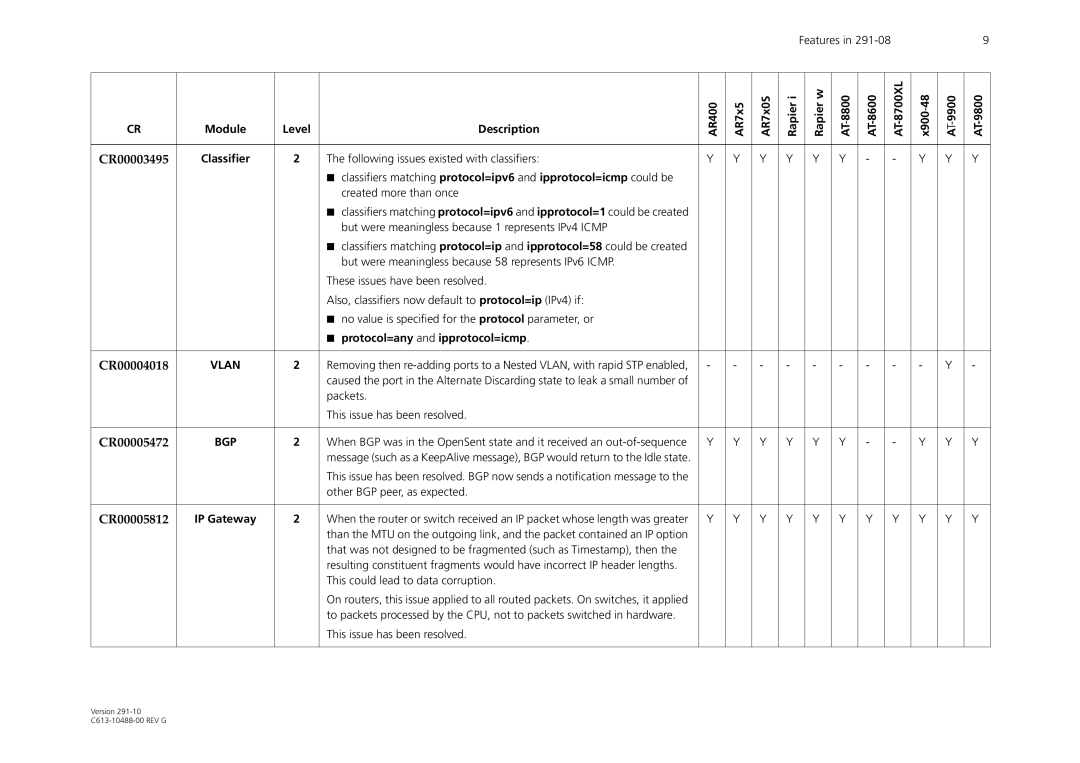
CR | Module | Level | Description | AR400 | AR7x5 | AR7x0S | Rapier i |
| Rapier w | AT8800- |
| x90048- | ||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00003495 | Classifier | 2 | The following issues existed with classifiers: | Y | Y | Y | Y |
| Y | Y | - |
| - | Y | Y | Y |
|
|
| ■ classifiers matching protocol=ipv6 and ipprotocol=icmp could be |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| created more than once |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ■ classifiers matching protocol=ipv6 and ipprotocol=1 could be created |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| but were meaningless because 1 represents IPv4 ICMP |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ■ classifiers matching protocol=ip and ipprotocol=58 could be created |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| but were meaningless because 58 represents IPv6 ICMP. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| These issues have been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Also, classifiers now default to protocol=ip (IPv4) if: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ■ no value is specified for the protocol parameter, or |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ■ protocol=any and ipprotocol=icmp. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00004018 | VLAN | 2 | Removing then | - | - | - | - |
| - | - | - |
| - | - | Y | - |
|
|
| caused the port in the Alternate Discarding state to leak a small number of |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| packets. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00005472 | BGP | 2 | When BGP was in the OpenSent state and it received an | Y | Y | Y | Y |
| Y | Y | - |
| - | Y | Y | Y |
|
|
| message (such as a KeepAlive message), BGP would return to the Idle state. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. BGP now sends a notification message to the |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| other BGP peer, as expected. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00005812 | IP Gateway | 2 | When the router or switch received an IP packet whose length was greater | Y | Y | Y | Y |
| Y | Y | Y |
| Y | Y | Y | Y |
|
|
| than the MTU on the outgoing link, and the packet contained an IP option |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| that was not designed to be fragmented (such as Timestamp), then the |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| resulting constituent fragments would have incorrect IP header lengths. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| This could lead to data corruption. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| On routers, this issue applied to all routed packets. On switches, it applied |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| to packets processed by the CPU, not to packets switched in hardware. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Version