Building a Network Access Control Solution
Page
International Technical Support Organization
Second Edition January
Contents
Part 2. Customer environment
Part 3. Appendixes
Index
Vii
Copyright License
AIX
Trademarks
IBM
Preface
Team that wrote this redbook
Preface
Become a published author
IBM US
Comments welcome
Page
Changed information
January 2007, Second Edition
New information
Page
Part 1 Architecture and design
Page
Business context
Security compliance and remediation concept
Why we need this
Http//banking.senate.gov/conf
Does this concept help our mobile users
Corporate security policy defined
Business driver for corporate security compliance
Achievable benefits for being compliant
Conclusion
Policy Development and Assurance
Business context
Page
Architecting the solution
Solution architectures, design, and methodologies
Architecture overview
Network Admission Control
WAN
Page
Security Compliance Manager
Page
Security policy
Tivoli Configuration Manager
Architectural terminology
Compliance query
Network Admission Control process
Compliance User Interface
Remediation handler
TCM
Cisco NAC and Ieee
ACS
Supplicant
Using Cisco terminology
Authenticator
Posture agent
Network identity provisioning
Remediation process
Phased rollout approach
Definition of a Network Admission Control project
Internet
Design process
Security compliance management business process
Architecting the solution
Security policy life cycle management
Creation
Implementation
Enforcement
Solution objectives
Review and update
Default network
Network design discussion
Performance controls
Quarantine access
Trusted network
Implementation flow
Scalability and high availability
Page
Conclusion
Page
Component structure
Solution logical block diagram
Logical components
Posture validation server
Network Admission Control
Network Admission Control Framework
CSlog
CSMon
Policy enforcement device
Admission control client
Logging service
Posture plug-in
Clean Access Agent CAA
Clean Access Manager CAM
Clean Access Server CAS
Network Admission Control Appliance
Compliance server
Clean Access Policy Updates
Compliance
Administration
Compliance reporting
Compliance client
Posture collector
Compliance client logical component
Policy collector
Remediation server
Default remediation handler
Remediation
Posture cache
Remediation handler component
Physical components
Network client
Security Compliance Manager policy
Cisco Trust Agent
Security Compliance Manager client
Network access device
Network access infrastructure
IBM Integrated Security Solution for Cisco Networks servers
Cisco Secure Access Control Server
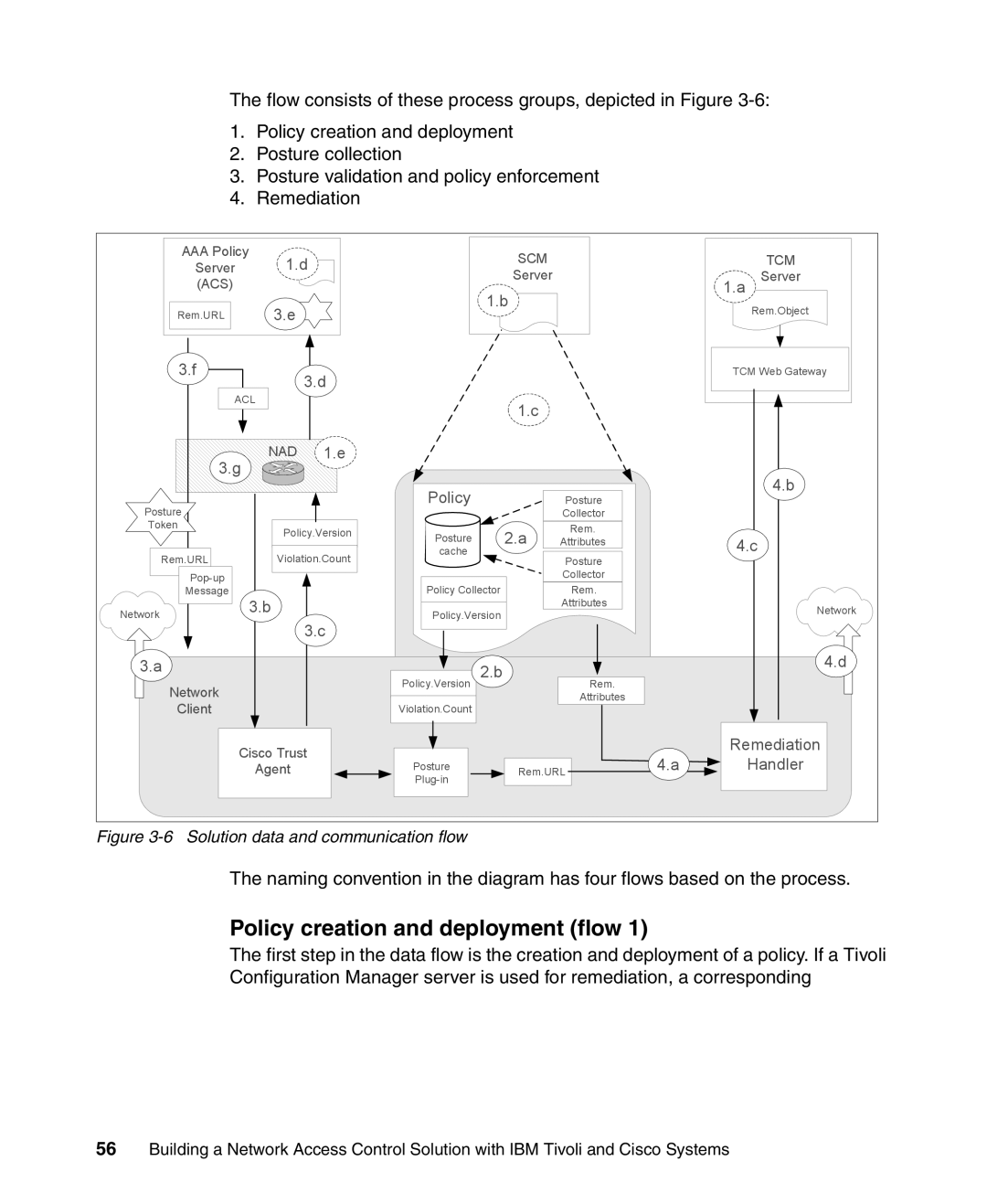
Solution data and communication flow
Tivoli Configuration Manager servers
Policy creation and deployment flow
Policy
Component structure
Posture collection process flow
Posture validation and policy enforcement flow
Page
Remediation flow
Secure communication
Secure communication between components
NAC communication
Component placement
Security zones
Security Compliance Manager communication
Less Secure
Uncontrolled zone Internet, external networks
Network
Restricted zone production network
Controlled zone external network-facing DMZ
Controlled zone intranet
Restricted zone management network
Branch egress enforcement
Policy enforcement points
Branch office compliance
Campus internal enforcement
Branch Office Compliance Campus Ingress Enforcement
Soho Compliance PAT access protection
Small Office Home Office compliance
Extranet compliance
Extranet Compliance
Lab compliance
LAB Compliance
Data Center protection
Data Center Protection
Remote access protection
Remote Access Protection
Part 2 Customer environment
Page
Armando Banking Brothers Corporation
Company profile
Current IT architecture
Network infrastructure
IBM Integrated Security Solution for Cisco Networks lab
Armando Banking Brothers Corporation
NAC Appliance
Armando Banking Brothers Corporation
Page
Application security infrastructure
Middleware and application infrastructure
DMZ
Project layout and implementation phases
Corporate business vision and objectives
Project overview
Action Reference Part I Security compliance server
NAC L2 IP
NAC L3 IP
CCA OOB VG
Part III Remediation server
Conclusion
Page
Solution design
Page
Business requirements
Security compliance requirements
Network access control requirements
Functional requirements
Solution functional requirements
Remediation requirements
Caused by worms and other hostile software
NAC solution conceptual functional requirements
Remediation services
Security compliance criteria
Implementation architecture
Attempt
Component subsystems total solution
Logical components
Configuring the compliance server
Establishing compliance criteria
Establishing the policy collector parameters
Tivoli Security Compliance Manager client components
Solution design
Setting the policy version
Maxdataagesecs conceptual flow
Setting the remediation handler URL attribute
11 Setting the remediation handler JAR classpath
Enforcing compliance criteria
Posture token
ACS
13 Posture validation policies
Page
14 Shared Radius Authorization Components
Assigning the System Posture Token
Performing remediation
Physical components
Remediation handler Html pages
Compliance subsystem
IBM Security Compliance Manager server
IBM Tivoli Security Compliance Manager client
Access Control Server
Network Admission Control subsystem
Solution design
Layer 3 devices
NAC-enabled network device
Layer 2 devices
LRE
Cisco Trust Agent
Software Package Web Server
IBM Tivoli Configuration Manager server
Remediation subsystem
Conclusion
Page
Compliance subsystem implementation
125
Tivoli Security Compliance Manager setup
Installation of DB2 database server
DB2 installation welcome window
127
DB2 version selection is presented similar to the one shown
Setup wizard welcome window
129
License agreement window
Installation type selection window
131
Installation action selection window
Installation folder selection window
133
User information dialog
Administration contact list dialog
135
10 DB2 Instance configuration window
137
11 DB2 Tools selection dialog
12 Administrator contact selection window
13 Installation options summary
139
Installation of Tivoli Security Compliance Manager server
14 Installation completion window
141
15 Language selection dialog
Server
Administration Utilities
Database Configuration
18 Setup type selection window
143
19 E-mail server configuration dialog
20 Server Communication Configuration window
145
Server Security Configuration window is displayed, as shown
147
22 Database Location selection window
23 Database configuration information
149
24 Database creation choice window
25 Administrator User ID Configuration window
26 Installation options summary window
151
Configuration of the compliance policies
27 Installation result window
153
Posture collectors
Posture items and posture elements
Operational
Policy collector
Posture collector parameters
Workflow
Installation of posture collectors
155
28 Tivoli Security Compliance Manager GUI login
30 Tivoli Security Compliance Manager Administration Console
157
32 Import file selection dialog
159
34 Collectors signature validation
35 Policy installation summary
Customization of compliance policies
161
37 Policies view
38 Collectors configuration view
163
Versionwf
Passversion
Warnversions
Faillastscanover
Defswf
165
Warndefsolderthan
Minlenwf
Warnminlenunder
Failminlenunder
Warnmaxageover
167
41 Editing collector parameters
PASSWINDOWS2000
Passwindowsnt
Warnwindowsnt
169
Hotfixwf
Warnhotfixes
Failhotfixes
171
KEY
Novaluerule
Nokeyrule
Value
Pass
173
Rules
Rule operators
Rule format
Checking for ZoneAlarm installation directory
Rule results
175
Checking for Windows XP firewall forced off
Reqservice
177
Servicedisabledwf
Servicerunningwf
Reqdisabled
Reqrunning
179
46 Copying an existing compliance query
47 Destination policy selection dialog
181
48 Renaming compliance query
49 Compliance query description modification
183
50 Violation message modification
51 Disabling collector sharing
185
53 Saving changes made to the policy collectors
Assigning the policy to the clients
54 Save policy collectors warning
187
55 Create group action selection
57 Add policy menu selection
189
Deploying the client software
Tcmcli utility policy
Cisco Trust Agent
Prerequisites
191
61 Certs directory with CTA
Installation of Cisco Trust Agent on Windows
62 Cisco Trust Agent installation wizard
193
63 License agreement for Cisco Trust Agent
Accept the defaults -64and click Next
65 Cisco Trust Agent installation type
195
Click Next Figure
197
67 Confirmation of the certificate import
Click Finish to close the installation, as shown in Figure
IBM Tivoli Security Compliance Manager client
199
Installation of the Security Compliance Manager client
70 Language selection
201
71 The welcome window
72 Client Installation Utility window
203
74 Directory selection window
75 Setup type window
205
Accept the defaults and click Next
Pull
207
77 Client connection window
78 Server communication configuration window
79 Client Dhcp configuration window
209
Next
211
81 Successful completion window
82 Security Compliance Manager posture plug-in files
Network enforcement subsystem implementation
213
Configuring NAC Framework components
Configuring the Cisco Secure ACS for NAC L2
Installing Cisco Secure ACS
215
Configuring the administrative interface to Cisco Secure ACS
Interface configuration advanced options
217
Allowing administrator access via Http optional
Administration control
Cisco Secure ACS certificate setup
219
Using an ACS self-signed certificate
221
Generating self-signed certificate
Restart the Cisco Secure ACS Figure
Importing IBM Security Compliance Manager attributes
223
Example 7-1 Security Compliance Manager attributes
225
Example 7-2 Import Security Compliance Manager attribute
Configuring logging
Click CSV Passed Authentications Figure
Select CSV Failed Authentications Figure
227
11 Failed attempts logging
Configuring a network device group in Cisco Secure ACS
229
13 Interface Configuration screen for the creation of NDGs
231
14 Network Device Group check box
15 Network Configuration
233
16 AAA clients
17 AAA client setup
235
18 AAA Clients
Configuring Radius attributes
19 Global Ietf Radius attributes
Configuring groups
237
21 Group Setup
Configuring users
239
23 User-to-Group mappings
241
Global authentication setup
Click Submit + Restart
EAP-FAST configuration Condition
EAP-TLS
243
EAP-GTC
Configuring posture validation
26 Posture Validation
245
27 Posture Validation Policies
28 CTA Posture Validation Policy
247
29 Posture Validation for CTA
Click Add Condition Set Figure
249
31 Adding a condition set
32 Posture validation rule creation for CTA check
251
33 CTA rule defined
34 Quarantine condition applied as default action
253
35 Completed posture validation for CTA
Click Apply and Restart, as shown in Figure
255
37 Repeating the process for Security Compliance Manager
38 IBM Tscm policy creation
257
39 IBM Tscm policy creation
Click Add Rule to get to the screen shown in Figure
259
41 Tscm policy components
Page
261
Click Done Figure
263
45 Completed posture validation rules
Configuring Radius Authorization Components
Click Radius Authorization Components
265
Ietf
47 IOS RAC attribute
267
48 Ietf drop-down menu
49 Healthy Sales RAC
269
Tunnel-Medium-Type 802
271
Configuring Network Access Profiles
Click Add Profile
51 Newly created NAP
52 Authentication configuration for RAC
273
From the screen shown in -53,click Add Rule
54 Partial configuration of posture validation
275
55 Selecting CTA and Tscm policies
An example of the CTA Healthy pop-up is shown in Figure
277
58 CTA pop-up configuration
279
59 Completed posture validation for Naciisscn
60 Authorization rule creation
281
User group System posture token Shared RAC
62 Completed Authorization RAC configuration
RAC
Unknown user policy
Configuring the Cisco Secure ACS for NAC L2/L3 IP
External User Database
Clientless user
Downloadable Access Control Lists
63 Downloadable ACL creation
285
64 Naming of ACL
Enter the name of the ACL and the ACL definition Figure
Select Radius Authorization Components
287
Vendor Attribute Value
Click Add Rule
289
68 L2IP Healthy Authorization rule
291
Deployment of the network infrastructure
Click Apply and Restart
Configuring Cisco 3750 switch for NAC L2
293
Page
Configuring Cisco 3750 switch for NAC L2 IP
295
Page
Has been applied to the switchport
297
Configuring Cisco IOS Router for NAC L3 IP
No URL Redirect
299
Page
301
Example 7-3 Output of show eou and show eou all command
Verifying Network Admission Control
Configuring NAC Appliance components
303
Installing CCA Agent
71 Installation wizard
72 Default install directory
305
Configuring a CCA OOB VG server
CCA version Required ports
75 CAM login
307
Clean Access Summary window will be displayed Figure
309
77 Device Management
Click Add Clean Access Server
78 Adding a new CAS
311
79 Successful CAS addition
80 CAS Status screen
313
81 Network IP screen
Select Advanced → Vlan Mapping
82 Managed subnets
315
Configure default login
Click Administration → User Pages → Login
Configuring a Switch Group
Select Switch Management → Profiles → Group → New
85 Switch Group creation
317
Verify your new switch group Figure
Configuring a switch profile
319
Configuring Port Profile
88 Switch profile
Select Switch Management → Profiles → Port → New Figure
321
90 Managed profile creation
323
Configuring Snmp receiver
Click Switch Management → Profiles → Snmp Receiver
Adding a managed switch
Select Switch Management → Devices → Switches → New
93 Manually adding a switch to be managed
325
As seen in -94,click the Ports icon
327
Defining user roles
Click User Management → User Roles → New Roles
Click Save Role when completed
329
Creating traffic policies
Click User Management → User Roles → Traffic Control → IP
98 Rules for trusted to untrusted
331
ActionAllow StateEnabled CategoryIP ProtocolTCP
Click Add Policy
Creating local users
Click User Management → Local Users → New Local User
Click Create User
333
Configure Clean Access Agent
102 List of local users
Click Add Check
335
104 CCA version compliance check
337
105 Rules check list check
Operating System
Rule Name
Rule Description
Rule Expression
339
107 CCA Compliance rule definition
Newly defined rules will be displayed Figure
341
Click Requirements → New Requirements Figure
Click Add Requirement
110 CCA Agent update
Click Requirement Rules
343
Click Role-Requirements
112 CCA Compliance Requirement rule
345
113 Role requirements
Discovered clients
114 Viewing online users
Logging on as a client
347
Click Continue
117 Web page pop-up informing user about non-compliance
118 Temporary access notification
349
120 Security Compliance Manager Compliance Report window
351
Configuring Cisco 3750 switch for NAC Appliance
123 Successful login
Example of interface configuration for CAM interface
353
Example of Snmp configuration
Remediation subsystem implementation
355
Page
Automated remediation enablement
357
Remediation server software setup
Prerequisites
359
Tivoli Configuration Manager
Tivoli Configuration Manager Web Gateway setup
Installation of Web infrastructure
Preparing for the installation
Installation of the DB2 database
361
WebSphere Application Server launchpad
WebSphere Installation Wizard window
363
Software License Agreement window
Installation type selection
365
Component selection dialog
Destination folder selection window
367
Node name selection window
Run as a service selection window
Installation options summary
369
10 Online registration dialog
Patching WebSphere Application Server installation
371
12 WebSphere product location
13 Installation option selection
373
Creating the necessary user account
14 Fix packs directory location
Installation of Tivoli Configuration Manager Web Gateway
375
Welcome window is presented -16. Click Next
377
17 License agreement window
18 Component selection
19 Installation directory selection window
379
20 Database configuration window
21 Web infrastructure configuration window
381
22 Endpoint configuration window
23 Secure access configuration
383
24 Summary of installation options
Configuration of the remediation server
385
Installation of Software Package Web Server
26 WebSphere administrative console login
387
27 Install new application
28 Preparing for the application installation
389
29 Installation option summary dialog
30 Installation status window
391
31 Saving the configuration changes
Configuration of the Software Package Web Server
393
Installation of the Software Package Utilities
395
Cd %BINDIR% Cd tcmremed\cfg Sputilinitialsetup.bat
Creating remediation instructions for the users
397
Locating Html
399
33 Directory structure for Html pages
Posture item Html
Defaultlang
Base Html
Html pages example
401
Variables and variable tags
Posture element Html
403
Wfattribute tag
Field Tag
Remattribute tag
Fail
405
\PROGRA~1\IBM\SC
Debug attributes
Logging available attributes
Logging posture items
407
Logging the Html search path
Creating Html pages for Abbc policy
409
Example 8-4shows the Html source code for this
Example 8-5 Content of style definition file
411
Page
Example 8-6 Html source for password length policy details
413
Wfattributecurrentvalues.brbWARNING fieldmsg/bbr
Example 8-7shows the Html source for
415
Page
Building the remediation workflows
417
TCRNavScan workflow
Example 8-8 Content of NavScanMessageen.wsf
419
Example 8-9 Content of Sample.properties file for TCRNavScan
421
38 Remediation handler interface with the warning
TCRNavVirusDefUpdate
423
Page
TCRNavSoftwareInstalled
425
TCRMSPatchesInstallWinXP
427
HotfixId=KB896423 TmfWebUIEndpoint=tcmweb
TCRMSServicePackInstallWinXpSp2
429
Page
431
AddRegistryValueBeforeExecData.arrayLength=2
TCRZLSoftwareInstalled
Noreboot
433
TCRZLSoftwareRunning
TCRMessengerDisabled
435
Modification of the remediation packages
437
Page
Part 3 Appendixes
439
Page
Appendix A. Hints and tips
441
Deployment overview
443
Appendix A. Hints and tips
Top-level sequence of events
Figure A-2 Isscn top-level sequence diagram
Security Compliance Manager and NAC compliance subsystem
Cisco Trust Agent
Figure A-4 Cisco NAC sequence diagram
Cisco NAC sequence of events
Fault isolation
Appendix A. Hints and tips
Security Compliance Manager server and client
Tivoli Security Compliance Manager Server
Communication port usage
Summary of default port usage
Tools and tricks
Cisco NAC
Cisco IOS Software switch
Cisco IOS Software router
Tools and tricks for the client
Cisco Secure ACS server
40500
NAC Appliance details
Cisco NAC Appliance components
In-band versus out-of-band
NAC Appliance integration
Integration design
Integration components
NAC Appliance Agent
TSCMAgent.bat
NACApplianceCompliance.entry
Scheduler
Kickrich.html
Installing and configuring prototype integration components
System path
Scheduler.bat
Considerations for designing a production solution
NAC Appliance Manager
State mapping and scenarios
Page
Appendix A. Hints and tips
Page
43 Sequence of Events for Scenarios #5 and #6
Conclusion
Appendix B. Network Admission Control
471
Executive summary
Benefit of NAC
Dramatically improve network security
473
NAC implementation options
NAC Appliance
475
NAC Framework solution
Investment protection
Planning, designing, and deploying an effective NAC solution
477
NAC Appliance components
Next steps
NAC technology
NAC Framework components
479
Page
Locating the Web material
481
Using the Web material
How to use the Web material
483
IBM Redbooks
Other publications
How to get IBM Redbooks
Online resources
IBM Support and downloads IBM Global Services
Help from IBM
Page
Numerics
487
SCM client communication
Glba
Html
NAC
NAD
Creation Deployment
PPP
Sarbanes-Oxley Act
Vlan
UDP
URL
Page
Page
Page
Building a Network Access Control Solution