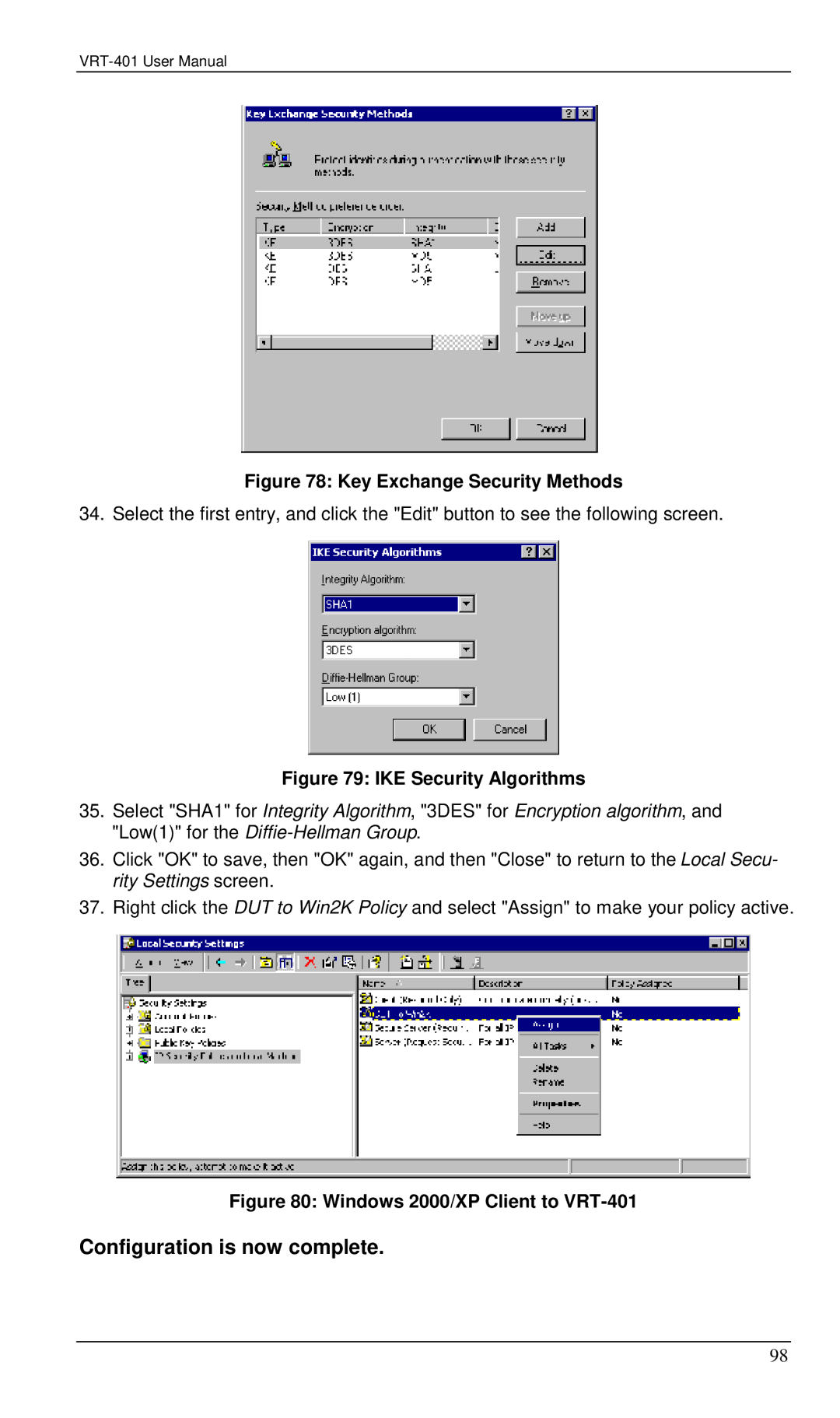
Figure 78: Key Exchange Security Methods
34. Select the first entry, and click the "Edit" button to see the following screen.
Figure 79: IKE Security Algorithms
35.Select "SHA1" for Integrity Algorithm, "3DES" for Encryption algorithm, and "Low(1)" for the
36.Click "OK" to save, then "OK" again, and then "Close" to return to the Local Secu- rity Settings screen.
37.Right click the DUT to Win2K Policy and select "Assign" to make your policy active.
Figure 80: Windows 2000/XP Client to VRT-401
Configuration is now complete.
98