ZyXEL | VES-1616/24FA-5x Series Support Notes |
Port-based VLAN across multiple switches
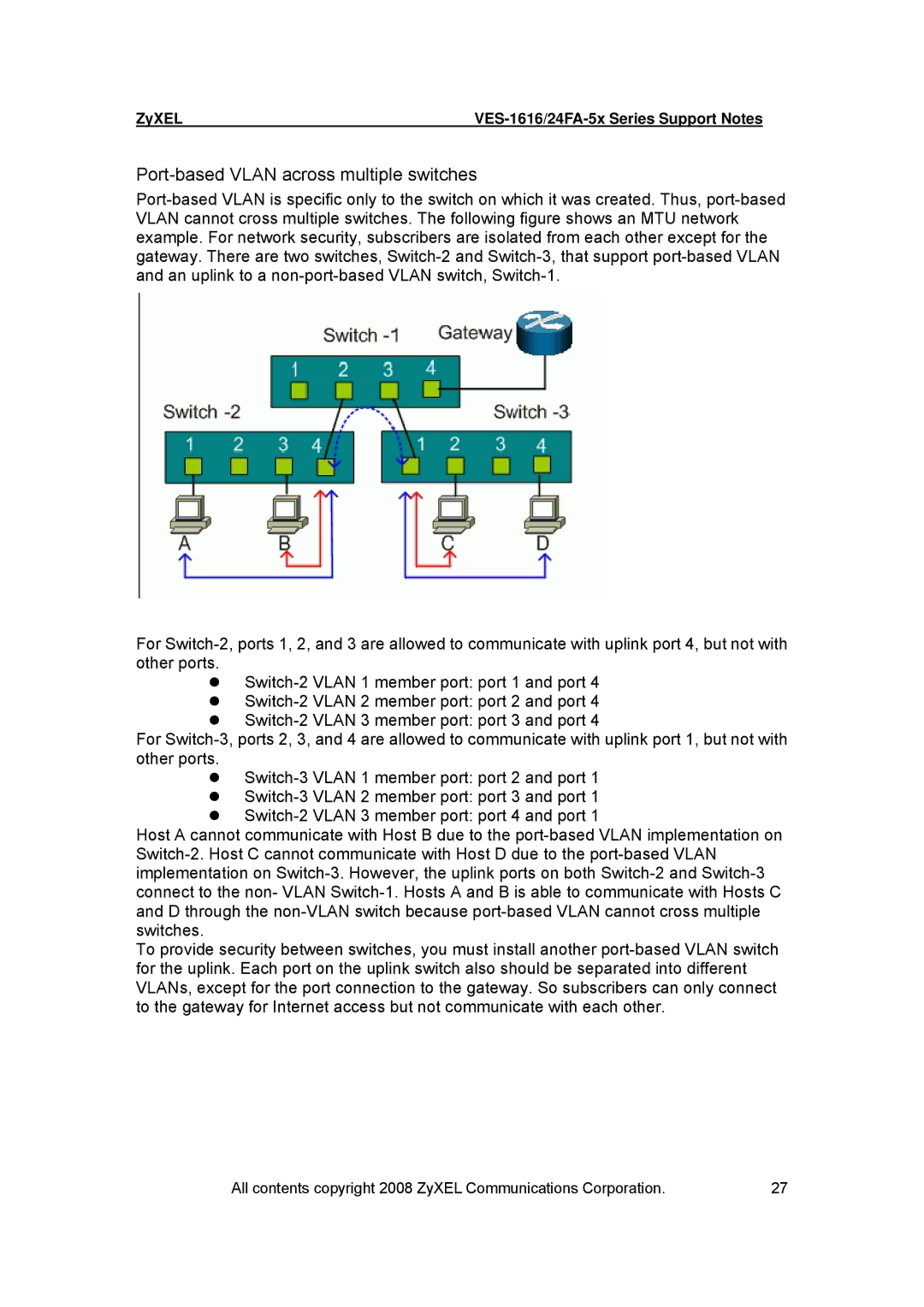
Port-based VLAN is specific only to the switch on which it was created. Thus, port-based VLAN cannot cross multiple switches. The following figure shows an MTU network example. For network security, subscribers are isolated from each other except for the gateway. There are two switches, Switch-2 and Switch-3, that support port-based VLAN and an uplink to a non-port-based VLAN switch, Switch-1.
For Switch-2, ports 1, 2, and 3 are allowed to communicate with uplink port 4, but not with other ports.
zSwitch-2 VLAN 1 member port: port 1 and port 4
zSwitch-2 VLAN 2 member port: port 2 and port 4
zSwitch-2 VLAN 3 member port: port 3 and port 4
For Switch-3, ports 2, 3, and 4 are allowed to communicate with uplink port 1, but not with other ports.
zSwitch-3 VLAN 1 member port: port 2 and port 1
zSwitch-3 VLAN 2 member port: port 3 and port 1
zSwitch-2 VLAN 3 member port: port 4 and port 1
Host A cannot communicate with Host B due to the port-based VLAN implementation on Switch-2. Host C cannot communicate with Host D due to the port-based VLAN implementation on Switch-3. However, the uplink ports on both Switch-2 and Switch-3 connect to the non- VLAN Switch-1. Hosts A and B is able to communicate with Hosts C and D through the non-VLAN switch because port-based VLAN cannot cross multiple switches.
To provide security between switches, you must install another port-based VLAN switch for the uplink. Each port on the uplink switch also should be separated into different VLANs, except for the port connection to the gateway. So subscribers can only connect to the gateway for Internet access but not communicate with each other.