Chapter 4: Web Configuration
Firewall
The firewall is a kind of software that interrupts the data between the Internet and your computer. It is the TCP/IP equivalent of a security gate at the entrance to your company. All data must pass through it, and the firewall (functions as a security guard) will allow only authorized data to be passed into the LAN.
What the firewall can do? It can:
deny or permit any packet from passing through explicitly
distinguish between various interfaces and match on the following fields:
source and destination IP address
port
To keep track of the performance of IP Filter, a logging device is used. The device supports logging of the TCP/UDP and IP packet headers and the first 129 bytes of the packet (including headers) whenever a packet is successfully passed through or blocked, and whenever a packet matches a rule being setup for suspicious packets.
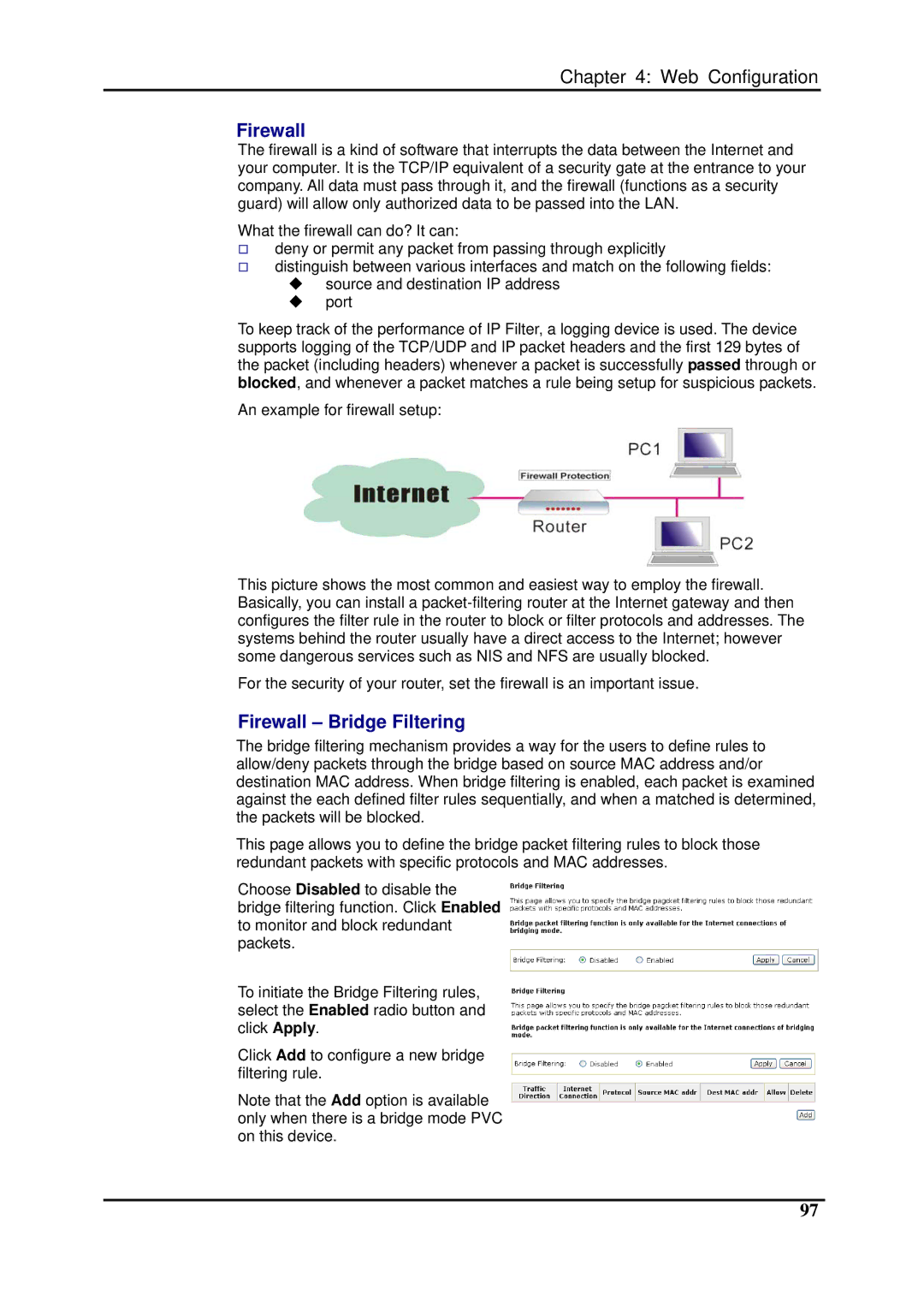
An example for firewall setup:
This picture shows the most common and easiest way to employ the firewall. Basically, you can install a
For the security of your router, set the firewall is an important issue.
Firewall – Bridge Filtering
The bridge filtering mechanism provides a way for the users to define rules to allow/deny packets through the bridge based on source MAC address and/or destination MAC address. When bridge filtering is enabled, each packet is examined against the each defined filter rules sequentially, and when a matched is determined, the packets will be blocked.
This page allows you to define the bridge packet filtering rules to block those redundant packets with specific protocols and MAC addresses.
Choose Disabled to disable the bridge filtering function. Click Enabled to monitor and block redundant packets.
To initiate the Bridge Filtering rules, select the Enabled radio button and click Apply.
Click Add to configure a new bridge filtering rule.
Note that the Add option is available only when there is a bridge mode PVC on this device.
97