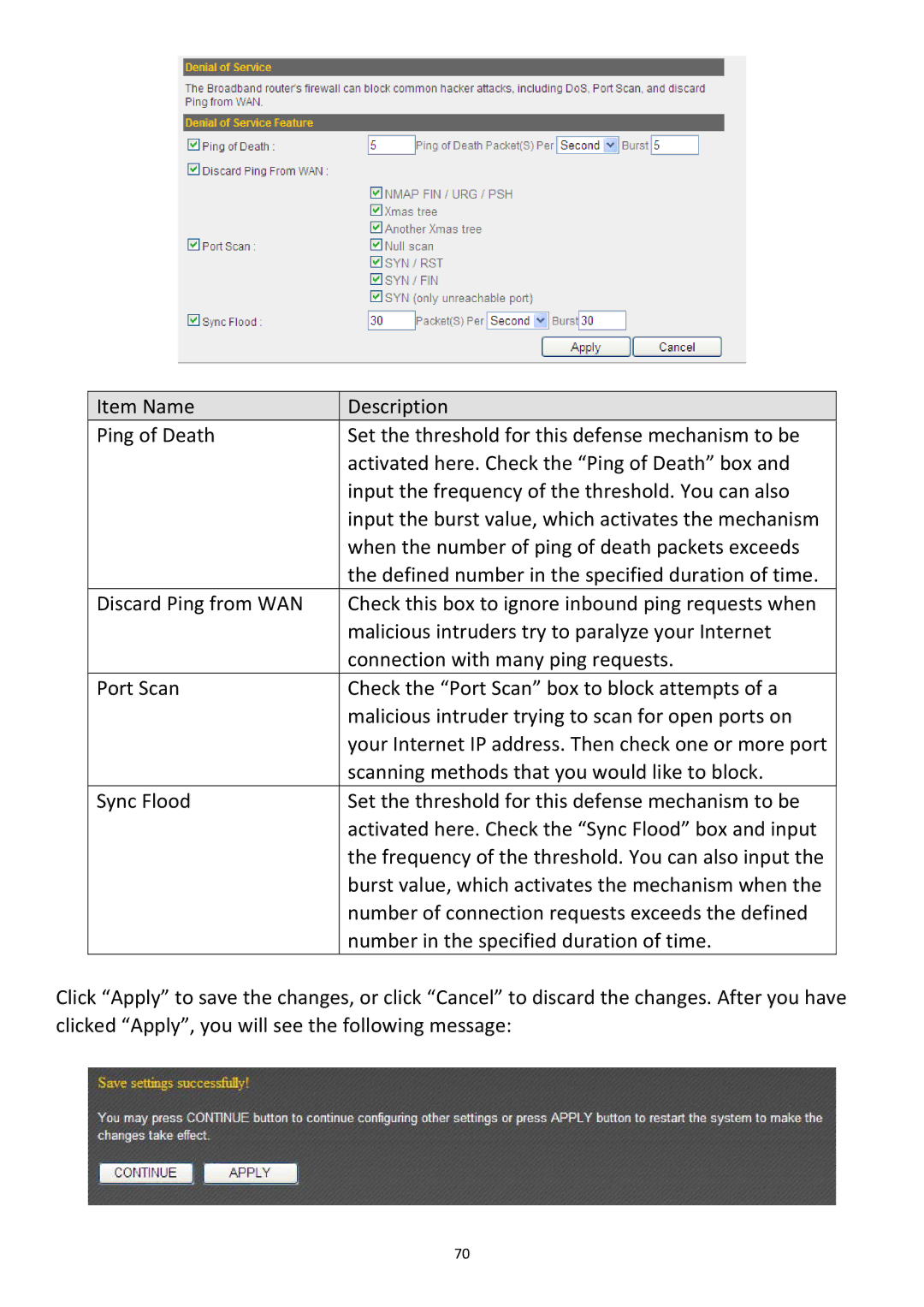
Item Name | Description |
Ping of Death | Set the threshold for this defense mechanism to be |
| activated here. Check the “Ping of Death” box and |
| input the frequency of the threshold. You can also |
| input the burst value, which activates the mechanism |
| when the number of ping of death packets exceeds |
| the defined number in the specified duration of time. |
Discard Ping from WAN | Check this box to ignore inbound ping requests when |
| malicious intruders try to paralyze your Internet |
| connection with many ping requests. |
Port Scan | Check the “Port Scan” box to block attempts of a |
| malicious intruder trying to scan for open ports on |
| your Internet IP address. Then check one or more port |
| scanning methods that you would like to block. |
Sync Flood | Set the threshold for this defense mechanism to be |
| activated here. Check the “Sync Flood” box and input |
| the frequency of the threshold. You can also input the |
| burst value, which activates the mechanism when the |
| number of connection requests exceeds the defined |
| number in the specified duration of time. |
Click “Apply” to save the changes, or click “Cancel” to discard the changes. After you have clicked “Apply”, you will see the following message:
70