3Com Corporation
Restricted Rights Notification for U.S. Government Users
Restricted Rights Legend
Proprietary Material
Page
Solutions
Overview
Functionality
Multiple LANs
Translational
Bridging
No Local Bridging
Transparent
This Manual Topic
This Notice Topic
Bridging Features and Capabilities
Switches
Introduction
Bridging Primer
Ethernet LAN
Example
Ethernet Bridge
Operation
WAN application, but you can also bridge across an X.25 WAN
Mixed LAN Bridging
MAC Addressing
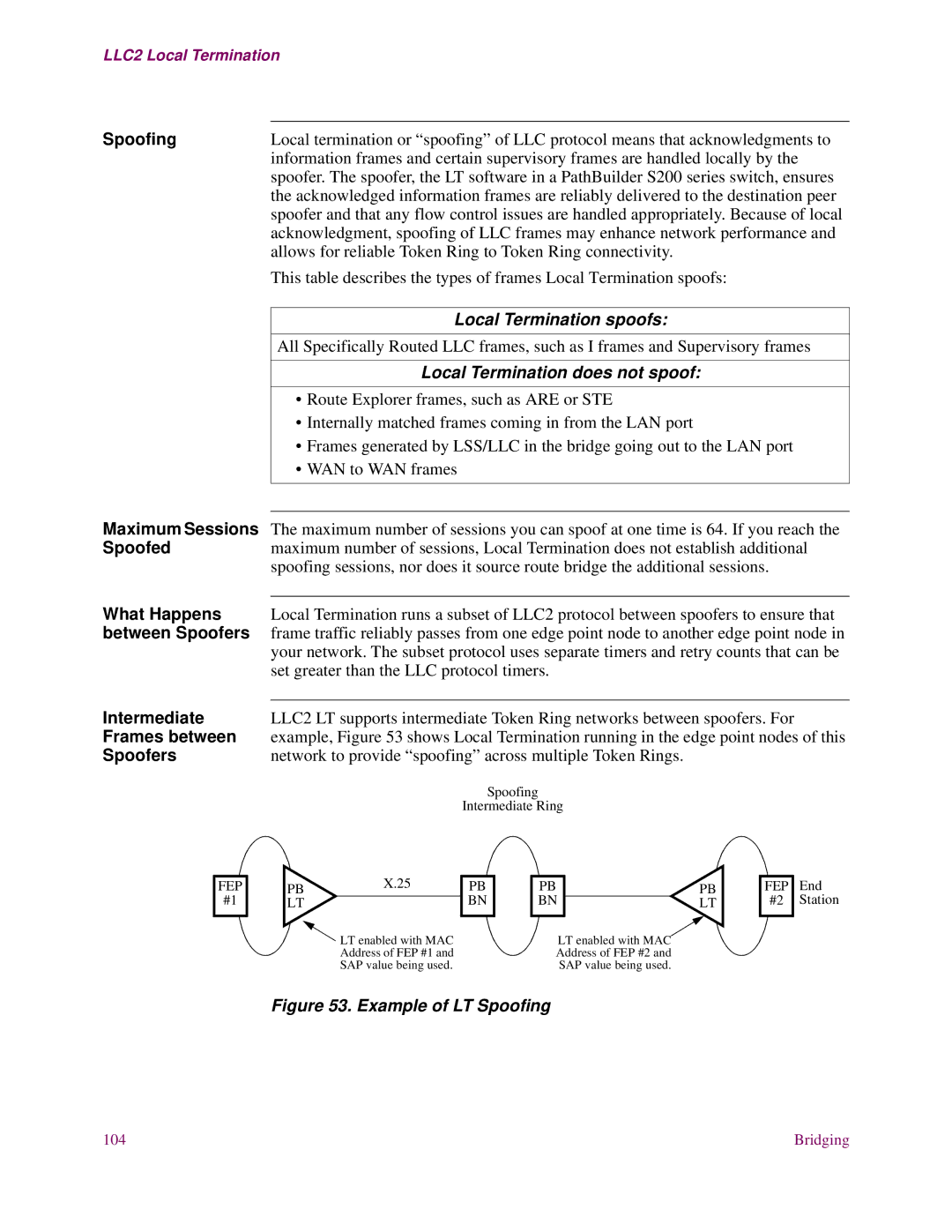
LLC2 Local Termination
LLC2 Local
Termination
LT Example
Autolearn for Local Termination
NetBIOS Name
Filtering
Mac Address
Filtering
What Is It? Automatic Manual Spanning Tree Support
Spanning Tree Protocol
Dual Ethernet LANs
Basic Remote Bridging Examples
Across a WAN
WAN or Permanent Virtual Circuit PVC for Frame Relay
Example of Bridges in an SVC Arrangement
Bridge
Connections
LAN Interface
Support
Bridging
Setting Up WAN Operation for Bridging
Interface Connections Between WAN and LAN
Setting Up WAN Operation for Bridging
Configure
Bridge Parameters
Parameters
These parameters make up the Bridge Parameter Record
Maximum Number of Bridge Links
Bad Hello Timeout
Stpe Control
AUTO, MAN
MAN
Learn Only Period used for Ethernet only
Aging Period used for Ethernet only
Bridge WAN Data Priority used for Ethernet only
Bridged Protocols
Parameters control the characteristics of this connection
Bridge Link Parameters
Bridge links as links to the networks attached to it
Bridge Link
These parameters make up the Bridge Link Record
Entry Number
BridgeType
SR, TB, Bothsrandtb
Hop Count Limit
Largest Frame Size
MAC Address Filter Action
NONE, PASS, Block
Netbios Name Filter Action
Protocol Filter Action
Stpe Link State
Link Mode
NORMAL,RFC1294, Trans
Normal
Virtual Ring Number
LAN Connection Table
Over the WAN
LAN Connection
Table Parameters
LAN Forwarder Type
ROUT, BRID, Brout
Rout
LAN Connection Type
Encapsulation Type
Codex
Autocall Mnemonic
Lcon Queue Limit
Billing Records
OFF, on
OFF
Traffic Priority
Where bridging is done remotely across a WAN
Limiting Bridge Frame Sizes
Overview
Transmission times for large frames become significant
Standard Frame
Sizes
Maximum frame size
Max Frame Size Line Speed Range kbps
Configuring Translational Bridging
Translational Bridging Example
Bridge Frame Handling
Configuring Source Route Bridging Operation
Configuring
Node for SRB
Individual Bridge
Bridging
Connecting a Station to a Server in Source Route Bridging
Procedure
LAN for a Source Route Bridging operation
Located on remote LAN CCC Figure
Server’s Destination MAC Address Not on LAN AAA
LAN Bridge Link
WAN Adapter Transmits Each are Frame Across the WAN
Server Responds with Specifically Routed Test Frame
Step Action Result/Description
Then
Transparent Bridging for Ethernet LANs
Learning
Forwarder
LAN link WAN link Link error
Forwarder Example
Statistics
Filtering
Hardware
Accelerator LAN/WAN Handlers
Hardware Accelerator Functions
Forwarder Functions Forwarder Initialization
Learn Only Period
Aging
Forwarder Database and Spanning Tree
Using Filters
Multicast Link
Frame is dropped
List, the frame is dropped
Control menu located in the Main menu
Transparent Bridge Configuration Parameters
TB Forwarding
Local MAC Address
Bridge Link Number
What is It? How Filtering is Used
Bridge Filtering
MAC Address Filtering
Parameter Action
Parameter
Parameter Action Value
MAC Filtering
Process
Mac Filtering Process Incoming and Outgoing Frames
Example of a Frame Passing on a Bridge Link
How To Configure Example
Configuring the Bridge Link Record
MAC Address Filtering Examples
First Example
Configuring the MAC Address Filter Table
Why it is Important
Identifying Address Links for MAC Addressing
Address Links
Series Switch Support
MAC Wildcard Filtering
Filtering works
Configuring the MAC Address Filter Table
Broadcast frames in the LAN network
Categories
These parameters make up the MAC Address Filter Table
Incoming Source Address Link Action
PASS, BLOCK, PASSLIST, Blocklist
Pass
Outgoing Source Address Link Action
Incoming Destination Address Link Action
Outgoing Destination Address Link Action
List of Links
Protocol Filtering
Protocol Filter
These parameters make up the Protocol Filter Table Record
Protocol Type
Protocol SAP hex value
Protocol OUI/IP hex value
Protocol Value
Incoming Protocol Link Action
Outgoing Protocol Link Action
Dsap Values
Parameter Actions
NetBIOS Name Filtering
Broadcasts to and from the SVR* name pattern
Transparent Bridging
Checking NetBIOS
Forcing a Local
Domain With
Filters
Configuring NetBIOS Name Filtering
How to Configure
NetBIOS Name Filtering
Step Action
Select Configure Configure
Step Action Result
Entry Number 1 appears
Bridge Bridge Link
Configure NetBIOS
NetBIOS Name Filter Table
Bridge -NetBIOS Name Filter
Name Filter Table
Typical Filtering
String Type
Ascii
Incoming NetBIOS Name Link Action
Incoming NetBIOS Name List of Links
Outgoing NetBIOS Name Link Action
Outgoing NetBIOS Name List of LInks
NetBIOS Name Filtering Statistics
NetBIOS broadcasts filtered on the link
Each bridge link
Check Detailed
NetBIOS Packet Formats
IBM NetBIOS Formats When to Use NetBIOS Name Filtering
All of the following are true
Either one of the following is true
Configuration Stpe Control= Auto Stpe Control = Manual Menu
Spanning Tree Protocol Entity Stpe
Spanning Tree
Tree
Bridge Links
Spanning Tree Protocol Entity Stpe
Stpe Parameter Setting Considerations
Example of a
Bridge Network
Setting the Root Bridge Spanning Tree
Bridge ID equals Bridge Priority Value in hex + MAC Address
Determining Root Links Designated Links
Type of Network Speed Stpe Path Cost
Consider
Nature
Expected Number
SVCs
Two Bridge Links Between B3 and B4
Spanning Tree Protocol Entity Stpe
Spanning Tree Timers
Timer Parameters
Hello Timer
Max Age
Other
Considerations
Bridge Forward Delay Timer
Message Events in Network
Spanning Tree Protocol Entity Stpe
Aging Timer
Bridges can adjust to the change
Location and forwards packets to it properly
Preventing session timeouts in a Bridging application
LLC2 Local Termination
Well as network delays
Terminal session, causing
Before Local
After Local
Supported
Topologies
Improper LT
Proper LT configuration
LLC Protocol LLC Frame Description LLC2 Frame Description
Type Name Description
Local Termination spoofs
Local Termination does not spoof
Bridging 105
Configuring Local Termination
Local Termination
Boot Type LLC LT Station
Step
Station Table Entry Number
WAN Parameters T1Reply Timer
T2 Rx Ack Timer
Local SAP
LLC Profile Name
Boot Type LLC LT WAN Parameters
Ti Inactivity Timer
N3 ACK Delay Count
N2 Retry Count
Configuration Entry Number
Tx Window Size
LCC LT WAN Data Priority
HIGH, MEDIUM, LOW
T1 Reply Timer
112 Bridging
Deleting LT Configuration Records
27x switch, as shown in Figure
Mixed LAN Operation
Mixed LAN Environment Limitations
Select Configure Bridge
Bridge Link Parameters menu
Bridge Link Parameters from
CTP Main menu, to activate Bridge link
Bothsrandtb
System powerup
Dual LAN Ethernet
Routing
Supported
Dual Ethernet LAN
Cmem
For Details on
Parameters
LAN Server Subsystem
Alarms
Configuring the LSS Record
Example of LCC
Record
Virtual Port’s MAC Address
ENABLE, Disable
Disable
Virtual Bridge ID
Path Trace Control
Bridge Statistics
Statistics Menu screen
Spanning Tree Statistics
Stpe Status
Status report
Term Description
Disabled The Stpe is disabled. If Stpe Control
State
Are
Parameter is MAN
Detailed Bridge Link Statistics
Detailed Bridge Link Statistics First
Screen Terms
RIF
Bridge Link Filter Summary
Link Filter
Summary
Description
Bridging 131
Transparent Bridge Forwarding Table Statistics
Stats Example
Stats Descriptions
Shown in Figure
Bridging 133
Transparent Bridge Detailed Bridge Link Statistics
Terms-Transparent Bridge Second
FF-FF-FF-FF-FF-FF
Frame Totals This is a count of the number of frames
Received/transmitted of all types on this link
LAN Connection Statistics
Statistics Menu
Detailed LAN Connection Statistics
Detailed LAN Connection Statistics Second
Explains why the last call was cleared
Last clear diagnostic code This is the diagnostic code
Connection and explains why the call was cleared
SVCs. The possible states are Blank for PVCs blank
Bridging 139
Example of LAN shows the LAN Connection Summary Statistics
Connection Summary Statistics
LLC2 LT Session Summary Statistics
Heading Description
SAP
Remote MAC Addr
Heading
LLC2 LT Detailed Session Statistics
Session Statistics
Last Statistics Last time statistics were reset Reset
Routing information field used in all frames transmitted
Field, ring number, and bridge number information
Heading Description Local Station Session Summary
Heading Description Remote Spoofer Session Summary
Reset Statistics
148 Bridging
Technical Support
Access by Analog Modem
3ComFacts Automated Fax Service
Access by Digital Modem
Country Data Rate Telephone Number
Support from
3Com
Country Telephone Number
Country Telephone Number Fax Number
Index
Numerics
LAN
OUI
URL A-1
Index-5

![]() LT enabled with MAC Address of FEP #1 and SAP value being used.
LT enabled with MAC Address of FEP #1 and SAP value being used.