User’s Guide
Disclaimer
Trademarks
Table of Contents
Using the Image Engine
Communications
Wireless PAN Wpan Communications with Bluetooth
Applications
Dolphin ChargeBase
Introduction
Overview
Required Safety Labels
Laser Safety Label
Location
Dolphin 7900 Series Wlan 802.11b or Wpan Bluetooth Radio
Parameter Specification
Bluetooth
802.11b
802.11b and Bluetooth
GSM and Bluetooth
GSM, 802.11b, and Bluetooth
Dolphin 7900 Series Wwan Radio GSM MC-45 & MC-46
FCC Compliance
Dolphin 7900 Series Batch Terminal
RF, Regulatory, and Safety Agency Approvals for GSM MC-45
RF, Regulatory, and Safety Agency Approvals for GSM MC-46
Parameter
Care and Cleaning of the Dolphin Terminal
For European Community Users
Microwaves
Waste Electrical and Electronic Equipment Information
Rev D
Getting Started
Data Input
Imaging
Memory
Dolphin 7900 Radio Configuration Options
Standard Configurations
Custom Configurations
Dolphin 7900 Series Peripherals
Dolphin 7900 Accessories
Using the Dolphin 7900 for the First Time
Unpack the Carton and Verify its Contents
To Remove the Main Battery Pack
Charging with Dolphin Peripherals
Align the Screen
Verify Operations with Demos
Resetting the Terminal
Suspend Mode
Soft Reset Warm Boot
Hard Reset Cold Boot
Rev D
System Features
Wireless Radio Options
Hardware Overview
Processor
Front Panel Features
PocketPC
Audio Jack
Speaker
IrDA Port
Scan LED
Back Panel Features
Battery
Image Engine Window
Hand Strap Slot
Stylus and Fastener
Side Panel Features
Opening the Access Door
Access Door
Programmable Side Button
Installing a Mini-SD Card
MSD SIM
Installing a SIM Card
Replacing the Access Door
Bottom Panel Features
Mechanical Connector
Powering Out
Battery Power
Main Battery Pack
Internal Backup Battery
Managing Battery Power
Default Low and Critical Battery Points
Setting Critical and Low Battery Points
Checking Battery Power
Guidelines for Battery Use and Disposal
Storing Batteries
Dolphin 7900 Technical Specifications
Temperature
Temperature Humidity
Resistance Power
Peripherals/Accessories
Using Dolphin Mobile Computers
Command Bar
Today Screen
Navigation Bar and Start Menu
Using the Touch Screen
Selecting Programs
Pop-Up Menus
Adjusting the Backlight
Wireless Radios
Communication Options
IrDA Port
Software Communication Programs
Radio Driver Installation
Radio Options
Radio Combinations
Radio Manager
Using the Soft Input Panel SIP
Using the SIP Keyboard
Using the Letter Recognizer
Using the Block Recognizer
Selecting Text
Input Panel Options
Input tab Word Completion tab Options tab
Writing on the Screen
Drawing on the Screen
To Select Writing
Status Icons
Notifications
Status Icon Meaning
Using Find
Using File Explorer
Using the Image Engine
Image Engine Options
Range Near
Far
Bar Code Symbologies Supported
Symbology Type Symbology Name 1D Symbologies
OCR Codes
Postal Codes
Activating the Engine
Demos
Decoding
Programmable Side Buttons
Sample Bar Codes
Omni-Directional Scanning
Capturing Images
Taking an Image
High-Vis Aiming Pattern
Uploading Images
Rev D
Using the Keyboards
Key Numeric Keyboard
Key Alpha Keyboard
Using the Function Keys
Using the Navigation Keys
Using the Modifier Keys
Name Key Function
Key combination pressed
Alpha Mode
Caps Lock Key in Alpha Mode
Key Numeric Keyboard
Blue Key Combinations
Red Key Combinations
Key Character
Key Combination Function
Red + F10
Key Alpha Keyboard
NUM Lock Key
Caps Lock Functionality
NUM Key Combinations
Numeric Shift in Numeric Mode
Rev D
Settings
Personal Tab System Tab Connections Tab Description
System
Connections
Personal Tab
To Enable HotKeys
Buttons
Button Assignments
Available Applications
Mic Volume
Headset Volume
Headset Control
Stereo headphone
Using System Settings
Using File Explorer
Tap Start Settings Personal tab Menus Start Menu tab
Menus Adding a Program to the Start Menu
Using ActiveSync on the Desktop Computer
System Tab
CPU Speed
To Increase/Decrease RAM Memory
Main tab
Functions
Storage Card Tab
Total storage card
Memory Use
Free
Power
Tab Description Battery Tab
Wireless Tab
Find Link
Regional Settings
Tab Description Advanced Tab
Remove Programs
To Remove Programs
Screen
Alignment tab
ClearType Tab
Text Size Tab
Default Font Size Largest Font Size
Zero-Config Wi-Fi
Connections Tab
Server-Assigned IP Addresses
Com Port Assignment Table
Opening the Connections Manager
Creating an External Modem Connection to an ISP
Task Tab
Tap Start Settings Connections tab Connections Task tab
Tap FInish Advanced Settings
Enter a name for the connection, such as My Connection
Port Settings Tab
General Tab
TCP/IP Tab
Connecting to Your ISP
Creating an External Modem Connection to Your Work
Establishing Exceptions for Work URLs
Servers Tab
Setting up a Proxy Server Connection for Work Connections
Setting Up a VPN Connection for Work Connections
Go to Start Settings Connections tab Connections
Dolphin 7900 Series User’s Guide Rev D
Connecting to a VPN Server
Establishing Dialing Rules
Creating a Wireless Network Connection
Network Cards
Dolphin 7900 Series User’s Guide Rev D
Rev D
General Help on Connecting
Installing Additional Software
Communications
Using ActiveSync
Synchronizing from Your Desktop Computer
Synchronizing from the Terminal
Exploring the Terminal from the Desktop Computer
Adding Programs to the Terminal Using ActiveSync
If the File is an Installer
If the File is Not an Installer
Using Infrared
Verify That the IrDA Port is Enabled
IrDA Port Location on the Terminal
Verify That Beam Settings Are Set to Receive
Sending and Receiving
Sending
Receiving
Troubleshooting
Using an ISP
Adding Programs Directly from the Internet
Wireless LAN Wlan Communications with 802.11b
Configuration Utilities
802.11b Wireless Security Supplement
Enabling the 802.11b Radio Driver
802.11b Settings
Tap Start Settings System tab 802.11b Settings
Status Icons
Icon This icon means…
Status Tab
Config Tab
To Add an Active Ssid to the Preferred Profile Table
To Create a New Profile
Authentication Tab
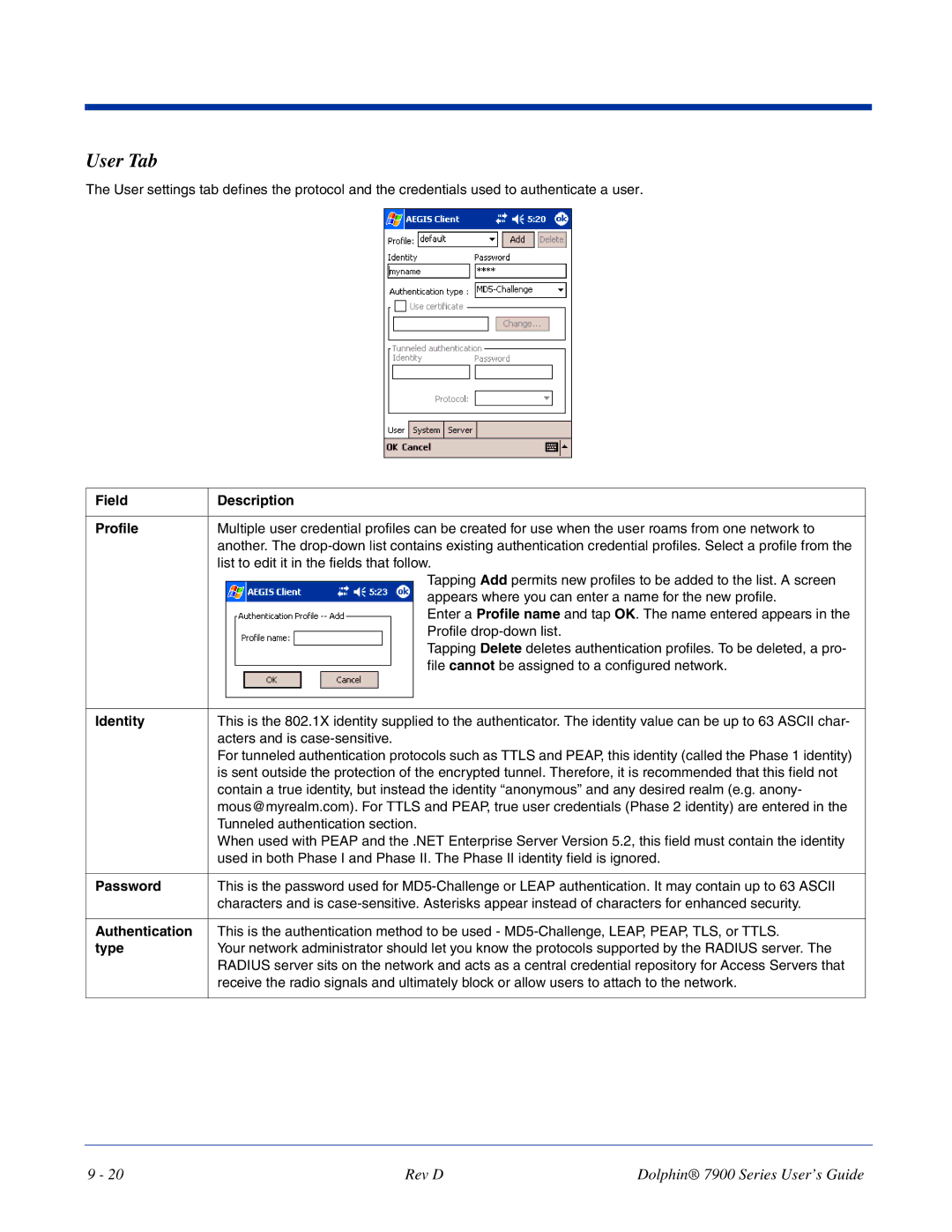
Field Description Authentication
Enable
Algorithm
Field Description Power Save Mode
Preamble Mode
To Delete a Profile
Advanced Tab
Using the Status Icon
About Tab
802.11b Wireless Security Supplement
Required Network Configuration Information Worksheets
Platforms Supported
802.1X Supplicant Protocol Support
MD5 Worksheet
Leap Worksheet
TLS/SmartCard Worksheet
Ttls Worksheet
Peap Worksheet
Icon Indicators
Opening the Client
Gray
Orange
Main Screen
Port Status Icon
Client Menu
Menu Item Tapping this item… Close
Install Protocol
View Menu
Exit
Help Menu
Status Bar
Menu Item Tapping this item…
Configuring the Client
Menu Item Description Enable
Disable
Port Menu
Configuration Screens
Client Configuration Area
Accessing the Client Configuration Area
On this tab You…
Password
User Tab
Field Description Profile
Identity
Tunneled authentication area
Field Description Use certificate
Protocol
System Tab
Port Settings Area
Server Tab
Wireless Networks Tab
Field Description Protocol Settings
Protocol Tab
Display EAP
Notifications
Adding a Wireless Network Configuration
Profile Info Tab
WEP Mgmt Tab
WPA Settings Tab
Field Description WPA Mode
Logging
PSK pass-phrase
Installing Certificates with CertAdd
Installing Certificates
Advice and Workarounds
Key to authenticate with AP
Select Peer-to-Peer Group ad hoc mode and Do active scan
Typical Message Exchange Using MD5 or TLS
How 802.1X Works
Typical Message Exchange Using Ttls and Peap
Central User Administration
Benefits
Relative Merits of Authentication Protocols
Dynamic Session Specific Wireless Encryption Keys
Cisco Leap
Additional Advantages of Ttls and Peap
Differences Between Protocols
Wireless PAN Wpan Communications with Bluetooth
Enabling the Bluetooth Radio
Setting Up Your Bluetooth Card
Assign COM Ports
Discover Bluetooth Devices
Bond With Discovered Devices
Rev D
Set Up Your Favorite Device
View Device Properties
Tap Tools My Favorites
Change Views
Delete a Device From the Folder
Bluetooth ActiveSync
Turn Radio Transmitter ON/OFF
Rev D
Bluetooth LAN Access
Rev D
Obex
Exchange Business Cards
Send a Contact
Send a File
Browse Remote Device
Prepare for File Transfer
Dolphin 7900 Series User’s Guide Rev D
Send/Receive Files or Folders
Create a Folder
Delete Files or Folders
Refresh Remote View
Connect/Disconnect
Tap Device Connect
Using the Dialer
Enable File Sharing
Exit Bluetooth File Explorer
Receive Contact or File
Using the Dialer
Tap Start Settings System tab Dialer
Assign a Dialing Prefix
Tap Start Contacts
Get Connected Wizard
Ericcson, Nokia 6210, NTT DoCoMo, Sony Phones
Accept
Motorola Timeport 270C, Nokia 3650/6310/7650/8910/8910i
Dial Up Connection
Tap Start Settings Connections tab Connections
Uncheck Wait for dial tone before dialing. Tap Finish
Automatic Connections for Motorola Timeport 270C
Automatic Connections for Nokia 3650/7650
Automatic Connections for Nokia 6310/8910/8910i
Wireless WAN Wwan Communications with GSM/GPRS
Installing a SIM Card
SIM Card
Audio Modes
Keyboard Combinations for Calls
Using uPhone
Accessing uPhone
Navigation Bar Icons
Icons and Bubble Messages
Tap Call Answerphone to dial
Using the Dialler
Making a Call
Entering a Phone Number
Sending a Call
Receiving a Call
Answering a Call
Rejecting a Call
Call Waiting
Ending a Call
Call Waiting
Placing the Current Call on Hold
Making Conference Calls
Dialler Menus
Touchtones
Tools Menu
Settings Menu
Phonebook
Menu Item Description See
Mic mute
Ringtone Configuration
Tap Start Settings Personal tab Ringtones icon or
WAV Files
Previewing Tones
Charging
Ussd
Call Log
Tap Start Programs uPhone Call Log or
Dialed
Exit Closes the Call Log
UPhone Configuration
Accessing uPhone Configuration
Tap Start Settings System tab uPhone icon
Tab Windows
General Tab
Network Tab
Divert Tab
Not Diverted
Bar Tab
Card can be made
All outgoing calls Bar all outgoing calls
Not barred
Messaging Tab
Request Delivery Reports
SMS Manager
Opening the SMS Manager
Inbox
Tap Start Programs uPhone SMS Manager, or
Sent Folder
Outbox Folder
Sending an SMS Message
Icons at the Top of the Message Screen
Edit Menu
Icon Description
Select All
Gprs Settings
Configuring the Gprs Connection
Service Provider Information
No ActiveSync
Tap Manage existing connections
Rev D
Dolphin 7900 Series User’s Guide Rev D
Rev D
Applications
Calendar
Creating an Appointment
Using the Summary Screen
Contacts
Creating Meeting Requests
Scheduling a Meeting
Creating a Contact
Searching for Contacts
Tasks
Creating a Task
Messaging
Creating a Note
Synchronizing E-mail Messages
Connecting Directly to an E-mail Server
Receiving Messages
Using the Message List
Composing Messages
Managing E-mail Messages and Folders
Accessing Pocket Internet Explorer
Pocket Internet Explorer
ActiveSync
Default View One Column View
Browse the Internet on Your Terminal
View Options
Mobile Favorites Folder
Using Mobile Favorites and Channels
Creating and Synchronizing Mobile Favorites
Using AvantGo Channels
Using Pocket Word
Pocket Word
Tap the AvantGo Channels link
Typing Mode
Drawing Mode
Pocket Excel
Creating a Word File
Creating an Excel File
Tips for Working in Pocket Excel
Windows Media Player for Pocket PC
Setting Up
MSN Messenger
Tap Start Programs MSN Messenger
Pictures
Tap Tools Options Account tab
To begin, tap Start Programs Pictures
Rev D
Intelligent Battery Charging
Power Supply
Dolphin HomeBase
Convenient Storage
AUX Battery LED
Front Panel
Terminal Well
Auxiliary Battery Well
DC Power Jack
Back Panel
RS-232 Port
RS-232 Serial Connector
Powering the Dolphin HomeBase
Charging the Main Battery
To Power a Terminal and Charge its Main Battery
Charging a Spare Battery in the Auxiliary Battery Well
Required Equipment for Setup
To Install the HomeBase Using USB
Setting up the Terminal for ActiveSync Communications
ActiveSync Communications with the HomeBase
Setting up the PC for ActiveSync Communications
Connecting the Cables
RS-232 Communications
RS-232 Pin Configuration HomeBase /Host Port
Pin / Input Signal
Modem DB25
Communicating with the Dolphin Terminal
Verifying Communication
Verifying Data Transfer
Mounting the HomeBase
Desk Mounting
Wall Mounting
Dolphin 7900 Series User’s Guide Rev D
Rev D
Dolphin Mobile Base
Communications
Convenient Storage
Capacity
Spring Arm Assembly
Dolphin Mobile Base Hardware Overview
Front Panel
Latch
Power Supply Connector
Bottom Panel
Comm LED Color Indicates that… Red
Orange Data is being sent at high data rates
TXD RXD DSR GND DTR CTS RTS Volt OUT
RS-232 Serial Communications Port
Back Panel
Ball Joint
Ball Joint Connector
Mounting the Dolphin Mobile Base
To Mount the Dolphin Mobile Base
Turnscrew
Powering the Dolphin Terminal
Setting Up the Mobile Base for Communications
RS-232 Pin Configuration
Charging the Dolphin Terminal
Configuring the Terminal for ActiveSync Communications
Dolphin ChargeBase
Dolphin ChargeBase Parts and Functions
Terminal Wells
Supplying Power to the ChargeBase
Dock LED
Charge LEDs
Inserting and Removing Terminals
Charging Terminals in the ChargeBase
Mounting the Dolphin ChargeBase
Using the DIN Rail
Using the Mounting Brackets
Dolphin 7900 Series User’s Guide Rev D
Rev D
Dolphin QuadCharger
Dolphin QuadCharger Parts and Functions
Battery Capacity Indicator LEDs
Power Switch
Rear Panel
Analyze Button
Supplying Power to the QuadCharger
Inserting and Removing Battery Packs
Recommendations for Storing Batteries
Charging Batteries in the QuadCharger
Using the Battery Analyzer
To Analyze a Battery
Location
Analyze Cycle
Mounting the QuadCharger
Troubleshooting
Problem Issue
Product Service and Repair
Online Product Service and Repair Assistance
Customer Support
Technical Assistance
Online Technical Assistance
North America/Canada
Limited Warranty
How to Extend Your Warranty
Rev D
Page
Hand Held Products, Inc