Hp procurve series 2500 switches
Page
Management and Configuration Guide
HP ProCurve Switches 2512
Publication Number
Preface
Use of This Guide and Other ProCurve Switch Documentation
Preface
Page
Contents
Tasks for Your First HP Web Browser Interface Session
Using a Standalone Web Browser in a PC or Unix Workstation
Globally Assigned IP Network Addresses
Viii
Chapter Contents Overview
Operating and Troubleshooting Notes
Web Displaying and Configuring Port Security Features
Menu Viewing and Configuring IP Authorized Managers
Web Configuring IP Authorized Managers
Rmon Support Extended Rmon
Advanced Management Rmon and HP Extended
Another Stack Monitoring Stack Status
Vlan Support and the Default Vlan
Multimedia Traffic Control with IP Multicast Igmp
Igmp Operating Features
10-9
10-8
Using the Event Log To Identify Problem Sources
Daylight Savings Time on HP ProCurve Switches
Xvi
Selecting a Management Interface
Chapter Contents
Selecting a Management Interface
Overview
Understanding Management Interfaces
Selecting a Management Interface
Advantages of Using the Menu Interface
Advantages of Using the Menu Interface
Menu interface also provides access for
Enables Telnet in-band access to the menu functionality
HP2512
Advantages of Using the CLI
HP2512config#
CLI Usage
Advantages of Using the HP Web Browser Interface
Advantages of Using the HP Web Browser Interface
Advantages of Using HP TopTools for Hubs & Switches
Advantages of Using HP TopTools for Hubs & Switches
Interface
Selecting a Management Interface
Screen Structure and Navigation
Using the Menu Interface
Starting and Ending a Menu Session
Menu Interface
Configure these features
Using the Menu Interface
Using
Starting and Ending a Menu Session
Starting and Ending a Menu Session
Menu Interaction with Other Interfaces
Results
How To Start a Menu Interface Session
Password
HP2512# menu Enter
Main Menu with Manager Privileges
How To End a Menu Session and Exit from the Console
Using the Menu Interface
Main Menu Features
Main Menu Features
Using the Menu Interface
Screen Structure and Navigation
Screen Structure and Navigation
TaskActions
How To Navigate in the Menu Interface
Example Showing How To Display Help
Rebooting the Switch
Rebooting the Switch
Reboot Switch option
Indication of a Configuration Change Requiring a Reboot
Logout
Menu Features List
Menu Features List
Option Where To Turn
Where To Go From Here
Using the Menu Interface
Displaying Help for an Individual Command
Use Tab To Search for or Complete a Command Word
Conventions for Command Option Displays
CLI commands are not case-sensitive
Accessing the CLI
Using the CLI
Privilege Levels at Logon
Using the CLI
Operator Privileges
Location, such as a locked wiring closet
Privilege Level Operation
Manager prompt
HP2512 Enable
HP2512config# vlan HP2512vlan-10#
Manager Privileges
Menu
Setup
Enable
Privilege Level Hierarchy
Change in Levels Example of Prompt , Command, and Result
How To Move Between Levels
? at the Operator level produces this listing
Listing Commands and Command Options
Listing Commands Available at Any Privilege Level
Typing ? at the Manager level produces this listing
Example of the Manager-Level Command Listing
HP2512config# portTab HP2512config# port-security
Command Option Displays
Displaying CLI Help
Example of How To List the Options for a Specific Command
Interface CLI
Example of Context-Sensitive Command-List Help
HP2512# interface help Invalid input interface
Configuration Commands and the Context Configuration Modes
HP2512eth-5-8# ?
10. Context-Specific Commands Affecting Port Context
HP2512vlan-100# ?
HP2512config# vlan
HP2512vlan-100#
CLI Control and Editing
Tasks for Your First HP Web Browser Interface Session
Using the HP Web Browser Interface
HP Web Browser Interface
Agent Enabled parameter setting to No
Using Using the HP Web Browser Interface
General Features
General Features
PCs
Web Browser Interface Requirements
PCs
Platform Entity and OS Version Minimum Recommended
Enable Java and Enable JavaScript options
Using a Standalone Web Browser in a PC or Unix Workstation
Http
Using HP TopTools for Hubs & Switches
Example of Status Overview Screen
Window displayed for the selected device, as shown in figure
HP Web Browser
Viewing the First Time Install Window
Tasks for Your First HP Web Browser Interface Session
Tasks for Your First HP Web Browser Interface Session
Creating Usernames and Passwords in the Browser Interface
String
Device Passwords Window
If You Lose a Password
Using the Passwords
Using the User Names
Server URL on
Online Help for the HP Web Browser Interface
Support/Mgmt URLs Feature
Support/Mgmt URLs Feature
If Online Help Fails To Operate. Do one of the following
Support URL
Help and the Management Server URL
How To Access Web Browser Interface Online Help
Overview Window
Status Reporting Features
Status Reporting Features
Port Utilization
Port Utilization and Status Displays
10. Changing the Graph Area Scale
Port Status
12. The Port Status Indicators and Legend
Alert The specific event identification
Alert Log
Sorting the Alert Log Entries
Each alert has the following fields of information
Alert String Alert Description
Alert Types
Alert Strings and Descriptions
Console interface
Viewing Detail Views of Alert Log Entries
Blue
Status Indicator Key
Color Switch Status
Status Bar
16. The Fault Detection Window
Setting Fault Detection Policy
Using the HP Web Browser Interface
Using
Interface Access Console/Serial Link, Web
IP Addressing Access,
Feature Default Menu
IP Configuration
IP Configuration Features
IP Configuration
IP Addressing with Multiple VLANs
HP2512# setup
Remove it from the switch
Just Want a Quick Start?
IP Addressing in a Stacking Environment
Following screen
To Configure IP Addressing
Switch Configuration IP Configuration
From the Main Menu, Select
Show ip
IP Commands Used in This Section
Address Ip default-gateway Ip ttl No ip timep
Syntax show ip
HP2512config# ip ttl
Click on the Configuration tab
Web Configuring IP Addressing
How IP Addressing Affects Switch Operation
Configure the Optional Timep Server
Servers
DHCP/Bootp Operation
Features Available Without an IP Address
Network
Process immediately
Address received via Dhcp or Bootp
Reply
Is the IP address to be assigned to the switch or Vlan
J2512switch
Network Preparations for Configuring DHCP/Bootp
Company Name/Address
Globally Assigned IP Network Addresses
Country
Locked environment
Interface Access Features
Switch Configuration System Information
Menu Modifying the Interface Access
To Access the Interface Access Parameters
Interface Access Commands Used in This Section
CLI Modifying the Interface Access
Two parameters
To disable web browser access
To re-enable web browser access
Configuration will take effect
Configuring Interface
Example of Executing a Series of Console Commands
System Information
System Information Features
At last Power reset
System Information
Enter, then press S for Save and return to the Main Menu
Menu Viewing and Configuring System Information
On configuration options for these features
Press E for Edit. The cursor moves to the System Name field
System information settings
CLI Viewing and Configuring System Information
System Information Commands Used in This Section
HP2512config# mac-age-time
For example, to configure the age interval to seven minutes
Configure System Parameters in the Web Browser Interface
Web Configuring System Parameters
For example, to set the switch to 345 p.m. on October 1
HP2512config# time 1545 10/01/00
Configuring Interface
Port Trunking
Viewing port status Configuring ports 10/100TX
Viewing Port Status and Configuring Port Parameters
Port Status and ConfigurationFeatures
Status or Description Parameter
Status and Parameters for Each Port Type
Status or Description
From the Main Menu, Select
Menu Viewing Port Status and Configuring Port Parameters
Using the Menu To Configure Ports
Trunking on
Show interfaces Below Show interface config Interface
CLI Viewing Port Status and Configuring Port Parameters
Port Status and Configuration Commands
Example of a Show Interface Command Listing
Viewing Port Status and Configuring Port Parameters
Click on Port Configuration
Web Viewing Port Status and Configuring Port Parameters
Web browser interface Click on the Configuration tab
Mbps Links
Viewing port trunks Configuring a static trunk None Group
Port Trunking
Port Trunking
T e U t i o n C P N o t e
Switch 2512 and 2524 Port Trunk Features and Operation
Trunk Types Used in Static and Dynamic Trunk Groups
Trunk Configuration Methods
HP2512config# Int e
Lacp passive
Protocol Trunking Options
Trunk Configuration Protocols
See Trunk Group Operation Using Lacp on
See Trunk Operation Using the FEC Option on
General Operating Rules for Port Trunks
Monitor Port
Switch Configuration Port/Trunk Settings
CLI To Configure Ports on
Example of the Configuration for a Two-Port Trunk Group
Show trunks Below Show lacp Trunk Interface lacp
Using the CLI To View Port Trunks
Trunk Status and Configuration Commands
Example of a Show Trunk Listing Without Specifying Ports
Using the CLI To Configure a Static or Dynamic Trunk Group
Yes Trunk
You can configure trunk group types as follows
Trunk Type Trunk Group Membership
Trk1 Static Dyn1 Dynamic
HP2512config# interface 5-6 lacp active
Click on Port Status
HP2512config# no interface 1 lacp
HP2512config# interface 1 lacp passive
Web Viewing Existing Port Trunk Groups
Lacp Trunk Types
Trunk Group Operation Using Lacp
Trunk group
Lacp trunk status include
Lacp Port Status Data
Default Port Operation
Particular switch, execute the following command in the CLI
HP2512 show lacp
Lacp Notes and Restrictions
Disabled The port cannot carry traffic
Trunk Operation Using the FEC Option
Trunk Group Operation Using the Trunk Option
Outbound Traffic Distribution Across Trunked Links
How the Switch Lists Trunk Data
Node a Node W Node B Node C Node Y Node D Node Z
11. Example of Port-Trunked Network
Through Traffic Control Optimizing Port Usage
CLI Port Security Command Options and Operation
Chapter Contents
Using Passwords, Port
Overview
Level Actions Permitted
Using Password Security
Password Features Default Menu
Menu Setting Manager and Operator passwords
Continue Deletion of password protection? No
To set a new password
Syntax password manager operator no password
CLI Setting Manager and Operator Passwords
Password Commands Used in This Section
Password below
Click on the Security tab
Web Configuring User Names and Passwords
Click on Device Passwords
Cast traffic
Configuring and Monitoring Port Security
Configuring Port Security Disabled
Basic Operation
Blocking Unauthorized Traffic
Configuring and Monitoring Port Security
Trunk Group Exclusion
Planning Port Security
Configuring and Monitoring Port Security
Acquires and maintains authorized addresses
CLI Port Security Command Options and Operation
Port Security Commands Used in This Section
Commands
Ethernet port-list
Port Security Parameters
Clear-intrusion-flag
Address-limit integer
Mac-address mac-addr
Using the CLI To Display Port Security Settings
CLI Displaying Current Port Security Settings
CLI Configuring Port Security
Using Passwords, Port Security, and Authorized IP
HP2512config# port-security 1 mac-address 0c0090-456456
U t i o n T e
Click on Port Security
Web Displaying and Configuring Port Security Features
How the Intrusion Log Operates
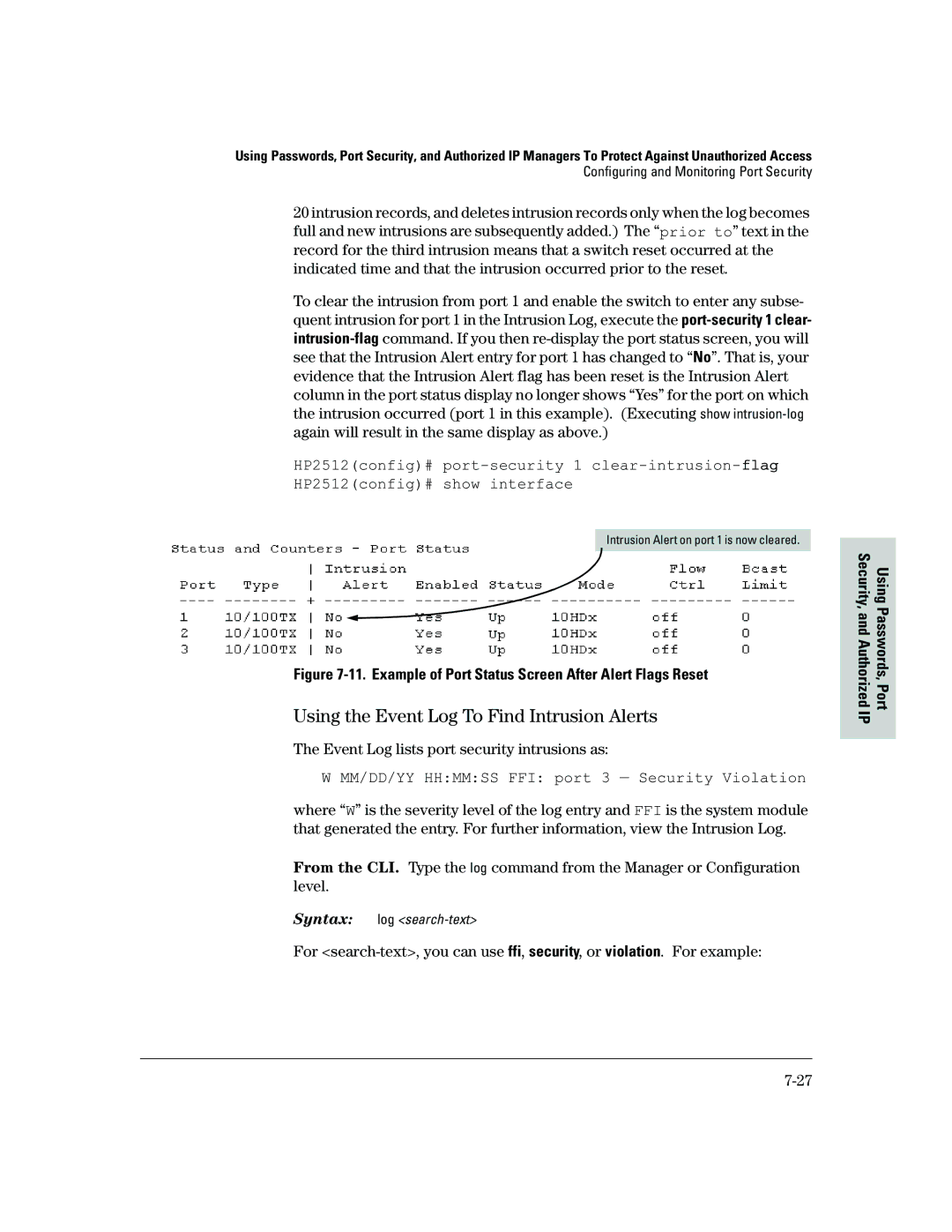
Reading Intrusion Alerts and Resetting Alert Flags
Example of Multiple Intrusion Log Entries for the Same Port
Keeping the Intrusion Log Current by Resetting Alert Flags
Status and Counters Port Status
Type I Intrusion log to display the Intrusion Log
Configuring and Monitoring Port Security
Clear Intrusion flags on all ports
List Intrusion Log content
List Intrusion Alert status
Event Log lists port security intrusions as
Using the Event Log To Find Intrusion Alerts
Operating Notes for Port Security
Configuring and Monitoring Port Security
Authorized IP Manager Features
Using IP Authorized Managers
Defining Authorized Management Stations
Access Levels
Using IP Authorized Managers
Masks on
Overview of IP Mask Operation
From the console Main Menu, select
Menu Viewing and Configuring IP Authorized Managers
Switch Configuration IP Authorized Managers
IP Mask
CLI Viewing and Configuring Authorized IP Managers
Listing the Switch’s Current Authorized IP Managers
Authorized IP Managers Commands Used in This Section
HP2512config# ip authorized-managers
Configuring IP Authorized Managers for the Switch
Address of the authorized manager you want to delete
Web Configuring IP Authorized Managers
Configuring One Station Per Authorized Manager IP Entry
Building IP Masks
Manager IP
Analysis of IP Mask for Single-Station Entries
Authorized 227 125
Analysis of IP Mask for Multiple-Station Entries
Port IP
Authorized
Operating and Troubleshooting Notes
Additional Examples for Authorizing Multiple Stations
Results
Security, and Authorized IP Using Passwords, Port
Monitoring and Managing the Switch
Configuring for Network Management Applications
Monitoring Configuring for Network Management Applications
Managing Switch
Snmp Management Features
Snmp Management Features
HP Entity MIB entity.mib
Configuring for Snmp Access to Switch
Switch Configuration Snmp Community Names
Configuring for Snmp Access to the Switch
To Restricted
To View, Edit, or Add Snmp Communities
Snmp Community Features
Write access for the public community to Restricted
Snmp Communities
Snmp Add or Edit Screen
Snmp Communities Screen Default Values
Community community-str
CLI Viewing and Configuring Community Names
Community Name Commands Used in This Section
Listing Current Community Names and Values
HP2512# show snmp-server public
Configuring Identity Information
Configuring Community Names and Values
Opotions are used with the snmp-server host command
Trap Receivers and Authentication Traps
Trap Features
Regardless of the trap receiver configuration
Syntax show snmp-server
CLI Configuring and Displaying Trap Receivers
Using the CLI To List Current Snmp Trap Receivers
Trap Receiver Commands Used in This Section
Using the CLI To Enable Authentication Traps
Using the CLI To Enable Authentication Traps
Configuring Trap Receivers
Extended Rmon
Advanced Management Rmon and HP Extended Rmon Support
Monitoring
Advanced Management Rmon and HP Extended Rmon Support
Features
Using the CLI To View Stack Status and Configure Stacking
Configuring Advanced Features
Configuring Advanced Features
109
103
105
108
Overview
Reduce the number of IP addresses needed in your network
Stacking Features Default Menu
Configure stacking
HP ProCurve Stack Management
Which Devices Support Stacking?
HP ProCurve Switch 8000M
HP ProCurve Switch 4000M
Stacking Definitions
Components of HP ProCurve Stack Management
General Stacking Operation
Network Backbone
Operating Rules for Stacking
General Rules
Specific Rules
Stack Name N/A
IP Addr Optional
Overview of Configuring and Bringing Up a Stack
No Manager password Or fewer stack members at the moment
Stacking Configuration Guide
General Steps for Creating a Stack
Use of System Name to Help Identify Individual Switches
Configuring Advanced Features
Default Stacking Menu
Default Stack Configuration Screen
Using the Menu To Manage a Candidate Switch
Seconds Range 1 to 300 seconds
Candidate Configuration Options in the Menu Interface
Parameter Default Setting Other Settings Stack State
Candidate Commander, Member, or Disabled
Using the Commander To Manage The Stack
Stacking Stack Management
Using the Commander’s Menu To Manually Add a Candidate to a
To add a Member, start at the Main Menu and select
You will then see the Stack Management screen
10. Example of Candidate List in Stack Management Screen
Stacking Status All
Stacking
Member MAC Addresses
You will then see the Stacking Status All screen
Member listed
Commander
14. Example of Selecting a Member for Removal from the Stack
Stacking Stack Access
You will then see the Stack Access screen
Stacking
From the Main Menu of the switch you want to move, select
Stacking Status All Features
Press Return
Stack Status Environments
Stack Configuration
Screen Name Commander Member Candidate
Monitoring Stack Status
Stacking Stacking Status All
You will then see the Commander’s Stacking Status screen
Stacking Stacking Status This Switch
You will then see the Member’s Stacking Status screen
19. Example of the Commander’s Stacking Status Screen
You will then see the Candidate’s Stacking Status screen
Configuring Advanced
Interface
CLI Commands for Configuring Stacking on a Switch
Commander’s CLI
CLI Command Operation No stack member
Manager password
Used In Commander Only
Viewing the Status of Candidates the Commander Has Detected
Using the CLI To View Stack Status
Viewing the Status of the Commander and Current Members
Features Configuring Advanced
Using the CLI To Configure a Commander Switch
26. Example of the Commander’s Show Stack Screen with Only
Commander Discovered
Adding to a Stack or Moving Switches Between Stacks
28. Example of How To Determine Available Switch Numbers SNs
Using the Commander’s CLI To Manually Add a Candidate to
Candidate
HP2512config# stack member 2 mac-address 0060b0-dfla00
HP2512config# no stack auto-join
HP 2512config# stack auto-join
31. Example of Pushing a Candidate Into a Stack
Using the Destination Commander CLI To Pull a Member from
32. Example of Stack Listing with Two Stacks in the Subnet
HP2524config# stack member 1 mac-address 0060b0-df1a00
Or the Member
Using the CLI To Remove a Member from a Stack
Access to the Commander
Member
Using the Member’s CLI To Remove the Member from a Stack
HP2512config# no stack member 3 mac-address 0030c1-7fc700
HP2512config# telnet
North Seaconfig# no stack join 0030c1-7fec40
Snmp Community Operation in a Stack
Snmp Management Station Access to Members Via the Commander
Commander Switch
Member Switch
Snmpget MIB variable 10.31.29.100 blue@sw2
Using the CLI To Disable or Re-Enable Stacking
Transmission Interval
38. Example of the Web Browser Interface for a Commander
Web Viewing and Configuring Stacking
Message Condition Action or Remedy
Status Messages
Stacking screens and listings display these status messages
Address would normally belong to the same Vlan
Vlan Features Default Menu
Disabled See Gvrp on VLANs
Port-Based Virtual LANs Static VLANs
39. Example of Routing Between VLANs via an External Router
40. Example of Overlapping VLANs Using the Same Server
Which Vlan Is Primary?
Overview of Using VLANs
Vlan Support and the Default Vlan
Per-Port Static Vlan Configuration Options
Forbid
Tagged
Untagged
Auto
General Steps for Using VLANs
You will then see the following screen
Menu Configuring Vlan Parameters
To Change Vlan Support Settings
Switch Configuration Vlan Menu Vlan Support
To the Vlan Menu screen
Space bar to select from the existing options
Gvrp on
802.1Q Vlan ID Name
Switch Configuration Vlan Menu Vlan Names
Adding or Editing Vlan Names
Adding or Changing a Vlan Port Assignment
Switch Configuration Vlan Menu Vlan Port Assignment
Untagged, or Forbid
48. Example of Vlan Port Assignment Screen
49. Example of Vlan Assignments for Specific Ports
CLI Configuring Vlan Parameters
No tagged port-list No untagged port-list No forbid
Vlan Commands Used in this Section
9-67 Available if Gvrp enabled
Static-vlan vlan-id 9-67 Available if Gvrp enabled
51. Example of Show Vlan for a Specific Static Vlan
For example, to make Vlan 22 the primary Vlan
For example, to reconfigure the switch to allow 10 VLANs
HP2512config# primary-vlan
For example, to create a new static Vlan with a VID
HP2512vlan-100# vlan defaultvlan
Creating a New Static Vlan Changing the Vlan Context Level
That static Vlan
HP2512config# static-vlan
HP2512vlan-100# no tagged
Web Viewing and Configuring Vlan Parameters
HP2512config# no vlan 100 tagged
At the Vlan 100 context level, use
Vlan Tagging Information
Click on Vlan Configuration Click on Add/Remove VLANs
54. Example of Tagged and Untagged Vlan Port Assignments
For the Red VID in switch Y
Untagged Tagged
Switch Switch Y
Port Red Vlan Green Vlan
To summarize
Effect of VLANs on Other Switch Features
Spanning Tree Protocol Operation with VLANs
IP Interfaces
Port Monitoring
Vlan MAC Addresses
Port Trunks
Vlan to another Vlan
Vlan Restrictions
IP Host-Only
Supported
Symptoms of Duplicate MAC Addresses in Vlan Environments
On a GVRP-enabled switch
View Gvrp configuration
Vlan Advertising and Joining on
General Operation
To allow tagged packets to pass through
Switch D Gvrp On
Switch C Gvrp On
Switch E Gvrp On
Per-Port Options for Handling Gvrp Unknown VLANs
Mode
Options for Handling Unknown Vlan Advertisements
Tagged or Untagged2 Auto2 Forbid2
Per-Port Static Vlan Options Gvrp Configuration
Per-Port Options for Dynamic Vlan Advertising Joining
Controlling Vlan Behavior on Ports with Static VLANs
To generate advertisements
Gvrp and Vlan Access Control
Port-Leave From a Dynamic Vlan
Dynamically joining other VLANs
Planning for Gvrp Operation
Configuring Gvrp On a Switch
Menu Viewing and Configuring Gvrp
60. The Vlan Support Screen Default Configuration
Show gvrp Below Gvrp Unknown -vlans
CLI Viewing and Configuring Gvrp
Gvrp Commands Used in This Section
HP2512config# interface 1-2 unknown-vlans block
HP2512config# gvrp
HP2512config# no gvrp
VLAN-222 VLAN-33
64. Example of Listing Showing Dynamic VLANs
Gvrp Operating Notes
Web Viewing and Configuring Gvrp
HP2512config# static
Configuring Advanced
Multimedia Traffic Control with IP Multicast Igmp
Igmp Features Default Menu
View igmp configuration
Multimedia Traffic Control with IP Multicast Igmp
Address Information screen
Igmp Operating Features
IGMP. Refer to IP Configuration on
How Igmp Operates on
CLI Configuring and Displaying Igmp
Indicating whether querier functionality is enabled
Igmp Commands Used in This Section
Including per-port data
Igmp configuration for all
VLANs on the switch
Igmp configuration for a
HP2512vlan-1# ip igmp
HP2512config# vlan 1 ip igmp
HP2512config# no vlan 1 ip igmp
Configuring Per-Port Igmp Packet Control. Use this command
How Igmp Operates
Web Enabling or Disabling Igmp
Role of the Switch
67. The Advantage of Using Igmp
68. Isolating IP Multicast Traffic in a Network
Per Vlan in which it is used
Be flooded instead of filtered by the switch
Number of IP Multicast Addresses Allowed
Interaction with Multicast Traffic/Security Filters
Cast storm that can bring down the network
STP Features Default Menu
Spanning Tree Protocol STP
Switch Configuration Spanning Tree Operation
Menu Configuring STP
Actions line
69. Example of the STP Configuration Screen
STP Commands Used in This Section
CLI Configuring STP
Default
Default configuration, STP appears as shown here
10.General STP Operating Parameters
HP2512config# spanning tree
107
HP2512config# spanning tree maximum-age 30 hello-time
Default See -11, above
11.Per-Port STP Parameters
How STP Operates
Web Enabling or Disabling STP
71. Example of Redundant Paths Between Two Nodes
STP Fast Mode
Ing network loops
To Configure Fast Mode for a Switch Port
HP2512config# spanning-tree ethernet 1-3,5 mode fast
STP Operation with 802.1Q VLANs
72. Example of Using a Trunked Link with STP and VLANs
112
10-1
Switch Operation
Internet Group Management Protocol Igmp Status
10-2
Ing. See Diagnostic Tools on
Monitoring Switch Monitoring and Analyzing Switch Operation
Analyzing Operation
Interface Purpose
Window under the Configuration tab
Status and Counters Data
10-3
Status and Counters
Menu Access To Status and Counters
10-5
Menu Access
CLI Access
General System Information
10-6
Switch Management Address Information
Monitoring Switch
Menu Displaying Port Status
Web Access
Status and Counters . . .3. Port Status Switch Operation
Port Status
For all ports
Particular port or trunk Resetting counters
Viewing Port and Trunk Group Statistics
Status and Counters Port Counters
Menu Access to Port and Trunk Statistics
To access this screen from the Main Menu, select
Click on Port Counters
CLI Access To Port and Trunk Group Statistics
Web Browser Access To View Port and Trunk Group Statistics
Mand provides traffic details for the port you specify
10-11
Viewing the Switch’s MAC Address Tables
Enter MAC address
Menu Access to the MAC Address Views and Searches
Status and Counters Address Table
To page through the listing, use Next page and Prev
Listing MAC Addresses for a Specific Port
Example of Menu Indicating Located MAC Address
To Find the Port On Which the Switch Learned a Specific MAC
CLI Access for MAC Address Views and Searches
Status and Counters Spanning Tree Information
Menu Access to STP Data
Spanning Tree Protocol STP Information
10-16
CLI Access to STP Data
HP2512 show spanning-tree
10-17
Show Command Output
10-18
Switch uses the CLI to display the following Vlan status
Vlan Information
Ports
10-19
Listing the Vlan ID VID and Status for Specific Ports
Listing Individual Vlan Status
10-20
Web Browser Interface Status Information
10-21
Port Monitoring Features
Port Monitoring Features Default Menu
Switch Configuration Network Monitoring Port
Menu Configuring Port Monitoring
Monitoring and Analyzing
To monitor individual ports
To monitor all ports in a Vlan
Port Monitoring Commands Used in This Section
CLI Configuring Port Monitoring
To turn off port monitoring
HP2512config# mirror-port
HP2512config# no mirror-port
For example, to assign port 12 as the monitoring port
Click on Apply Changes
Web Configuring Port Monitoring
To enable port monitoring Click on the Configuration tab
Click on Monitor Port
11-1
Troubleshooting
Menu Entering and Navigating in the Event Log
Troubleshooting
11-3
Troubleshooting Approaches
Troubleshooting Approaches
Browser or Console Access Problems
Browser or Console Access Problems
Cannot access the web browser interface
11-5
11-6
General Problems
Unusual Network Activity
Ip Invalid ARP source IP address on IP address
11-7
IGMP-Related Problems
Switch Cannot Find the Timep Server or the Configured
Problems Related to Spanning-Tree Protocol STP
Stacking-Related Problems
Timep or Gateway Problems
Tagged Monitor
VLAN-Related Problems
11-9
Within Same Outside Tagged Vlan
11-10
11-11
Using the Event Log To Identify Problem Sources
08/05/98 105232 Ports Port 1 enabled
Date Time System Module
11-12
Menu Entering and Navigating in the Event Log
Event Log System Modules
From the Main Menu, select Event Log
HP2512 show logging -a system
Event Log Control Keys
Ping and Link Tests
Diagnostic Tools
Diagnostic Features
Diagnostic Tools
11-15
Web Executing Ping or Link Tests
To halt a ping test before it concludes, press Ctrl C 11-16
CLI Ping or Link Tests
11-17
14.Example of Link Tests Troubleshooting
Click on Configuration Report
Displaying the Configuration File
CLI Viewing the Configuration File
Web Viewing the Configuration File
Toggles the paging mode for
Currently running on the switch
Displays the switch shutdown
Displays the current command
Clear/Reset Resetting to the Factory-Default Configuration
Restoring the Factory-Default Configuration
CLI Resetting to the Factory-Default Configuration
Appendix Contents
Downloading an Operating System OS
Model. See Transferring Switch Configurations on page A-10
Downloading an Operating System OS
Using Tftp To Download the OS File from a Server
Console Main Menu, select Download OS to display this screen
Menu Tftp Download from a Server
Validating and Writing System Software to Flash
CLI Tftp Download from a Server
Check the Firmware revision line
Menu Switch-to-Switch Download
Using the SNMP-Based Software Update Utility
Series 2500 Switch-to-Switch Download
Syntax
Using Xmodem to Download the OS File From a PC
CLI Switch-To-Switch Download
Menu Xmodem Download
HP2512 show system
CLI Xmodem Download from a PC or Unix Workstation
HP2512# show log tftp
Troubleshooting Tftp Downloads
Troubleshooting Tftp Downloads
Session in which the download was attempted
Transferring Switch Configurations
Tftp Retrieving a Configuration from a Remote Host
Transfer Features Default Menu
Tftp Copying a Configuration to a Remote Host
Syntax copy xmodem startup-config pc unix
MAC Address Management
Appendix B Contents
Determining MAC Addresses
MAC Address Viewing Methods Feature Default Menu
Determining MAC Addresses
MAC Address Management
Configured on the Switch
Menu Viewing the Switch’s MAC Addresses
Base switch default Vlan VID =
Any additional VLANs configured on the switch
HP2512# walkmib ifPhysAddress
CLI Viewing the Port and Vlan MAC Addresses
Switch Memory and Configuration
Switch Memory and Configuration
Startup-Config File
Overview of Configuration File Management
Overview of Configuration File Management
Any of the following actions reboots the switch
HP2512config# interface ethernet 5 disable
HP2512config# write memory
Using the CLI To Implement Configuration Changes
Using the CLI To Implement Configuration Changes
Syntax write memory
HP2512config# interface e 5 speed-duplex auto-10
With the factory-default startup configuration
Do you want to save current configuration y/n?
Changes on page C-9
Syntax erase startup-config
Changes
Memory in the CLI before rebooting the switch
Using Save and Cancel in the Menu Interface
Cancelled
73.The Reboot Switch Option in the Main Menu
Rebooting from the Menu Interface
Config file and the startup-config file
Using the Web Browser Interface To Implement
Configuration Changes
Canada and Continental US
2524 2400M 224M Switches 2424M
Daylight Savings Time on HP ProCurve Switches
Alaska
Western Europe
ProCurve Switches
Middle Europe and Portugal
Southern Hemisphere
Daylight Savings Time on HP ProCurve Switches
Page
Index
Index
See FEC
Garp
Lacp
See Igmp
See Vlan
See MIB
See also IP
VID
Xmodem OS download … A-7 XNS …