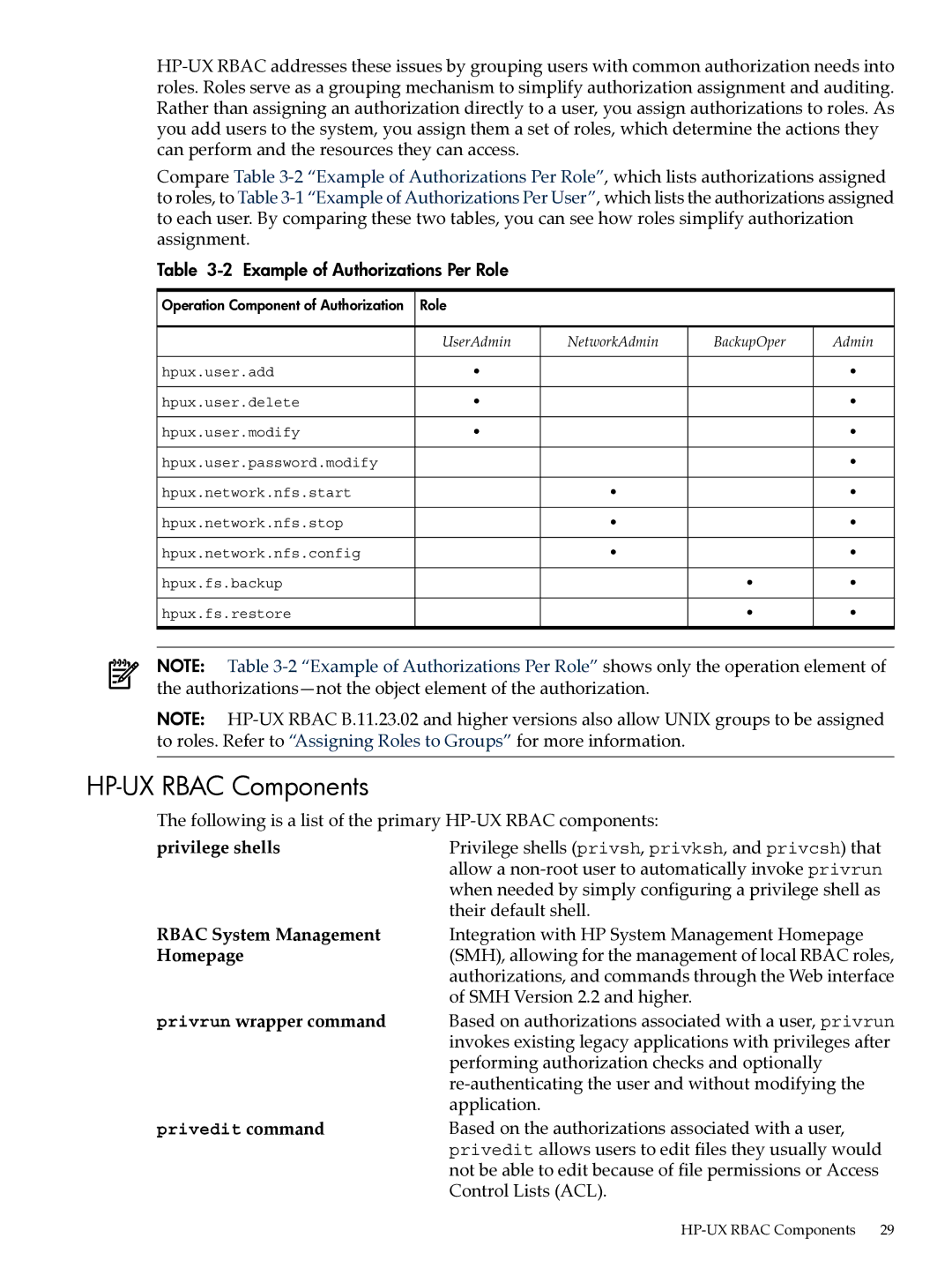
Compare Table
Table 3-2 Example of Authorizations Per Role
Operation Component of Authorization | Role |
|
|
|
| UserAdmin | NetworkAdmin | BackupOper | Admin |
hpux.user.add | • |
|
| • |
hpux.user.delete | • |
|
| • |
hpux.user.modify | • |
|
| • |
hpux.user.password.modify |
|
|
| • |
hpux.network.nfs.start |
| • |
| • |
hpux.network.nfs.stop |
| • |
| • |
hpux.network.nfs.config |
| • |
| • |
hpux.fs.backup |
|
| • | • |
hpux.fs.restore |
|
| • | • |
NOTE: Table
NOTE:
HP-UX RBAC Components
The following is a list of the primary
Privilege shells (privsh, privksh, and privcsh) that allow a
Integration with HP System Management Homepage (SMH), allowing for the management of local RBAC roles, authorizations, and commands through the Web interface of SMH Version 2.2 and higher.
Based on authorizations associated with a user, privrun invokes existing legacy applications with privileges after performing authorization checks and optionally
Based on the authorizations associated with a user, privedit allows users to edit files they usually would not be able to edit because of file permissions or Access Control Lists (ACL).