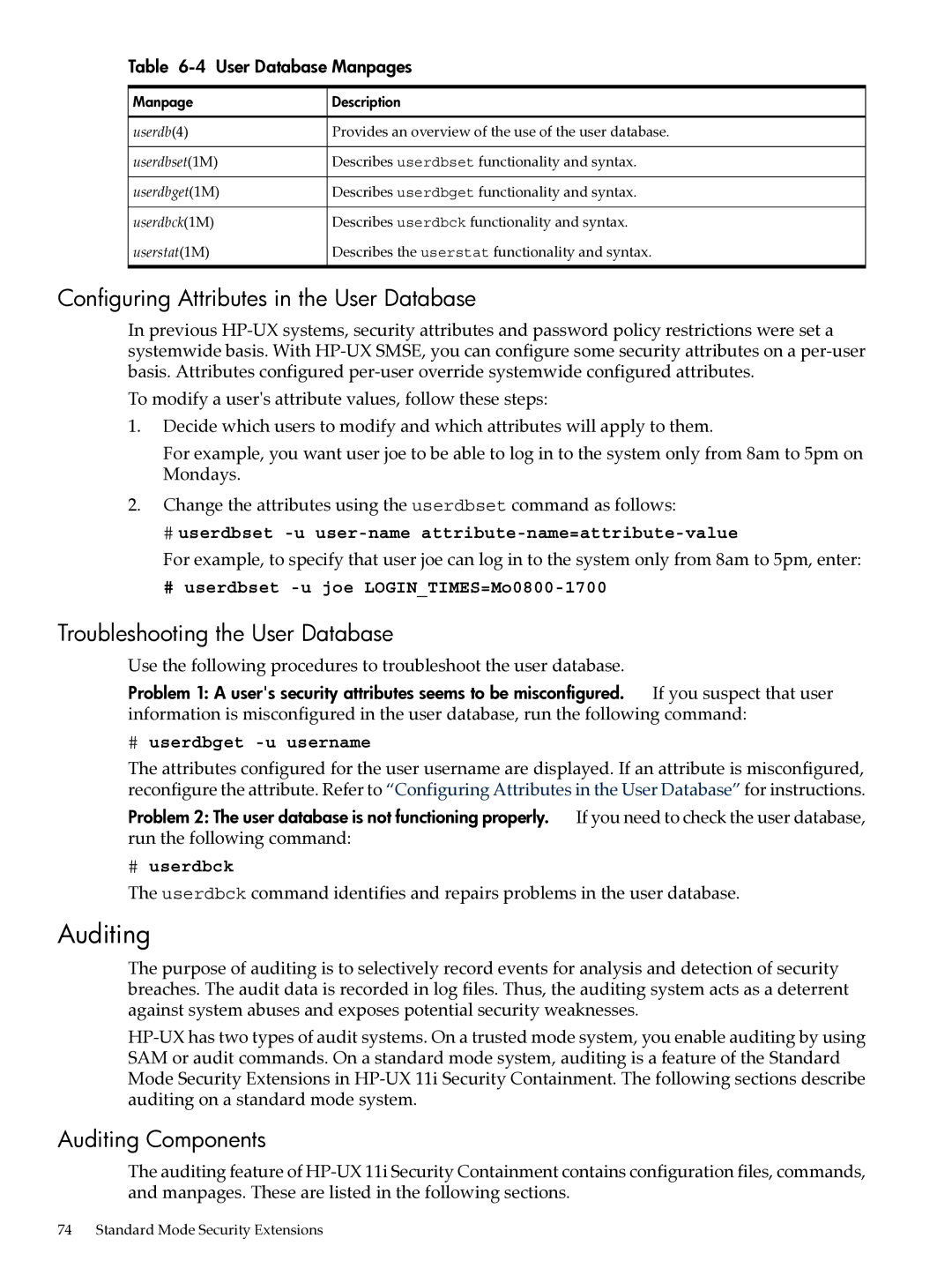
Table 6-4 User Database Manpages
Manpage | Description |
userdb(4) | Provides an overview of the use of the user database. |
userdbset(1M) | Describes userdbset functionality and syntax. |
userdbget(1M) | Describes userdbget functionality and syntax. |
userdbck(1M) | Describes userdbck functionality and syntax. |
userstat(1M) | Describes the userstat functionality and syntax. |
Configuring Attributes in the User Database
In previous
To modify a user's attribute values, follow these steps:
1.Decide which users to modify and which attributes will apply to them.
For example, you want user joe to be able to log in to the system only from 8am to 5pm on Mondays.
2.Change the attributes using the userdbset command as follows:
#userdbset -u user-name attribute-name=attribute-value
For example, to specify that user joe can log in to the system only from 8am to 5pm, enter:
# userdbset
Troubleshooting the User Database
Use the following procedures to troubleshoot the user database.
Problem 1: A user's security attributes seems to be misconfigured. If you suspect that user information is misconfigured in the user database, run the following command:
#userdbget -u username
The attributes configured for the user username are displayed. If an attribute is misconfigured, reconfigure the attribute. Refer to “Configuring Attributes in the User Database” for instructions.
Problem 2: The user database is not functioning properly. If you need to check the user database, run the following command:
#userdbck
The userdbck command identifies and repairs problems in the user database.
Auditing
The purpose of auditing is to selectively record events for analysis and detection of security breaches. The audit data is recorded in log files. Thus, the auditing system acts as a deterrent against system abuses and exposes potential security weaknesses.
Auditing Components
The auditing feature of
74 Standard Mode Security Extensions