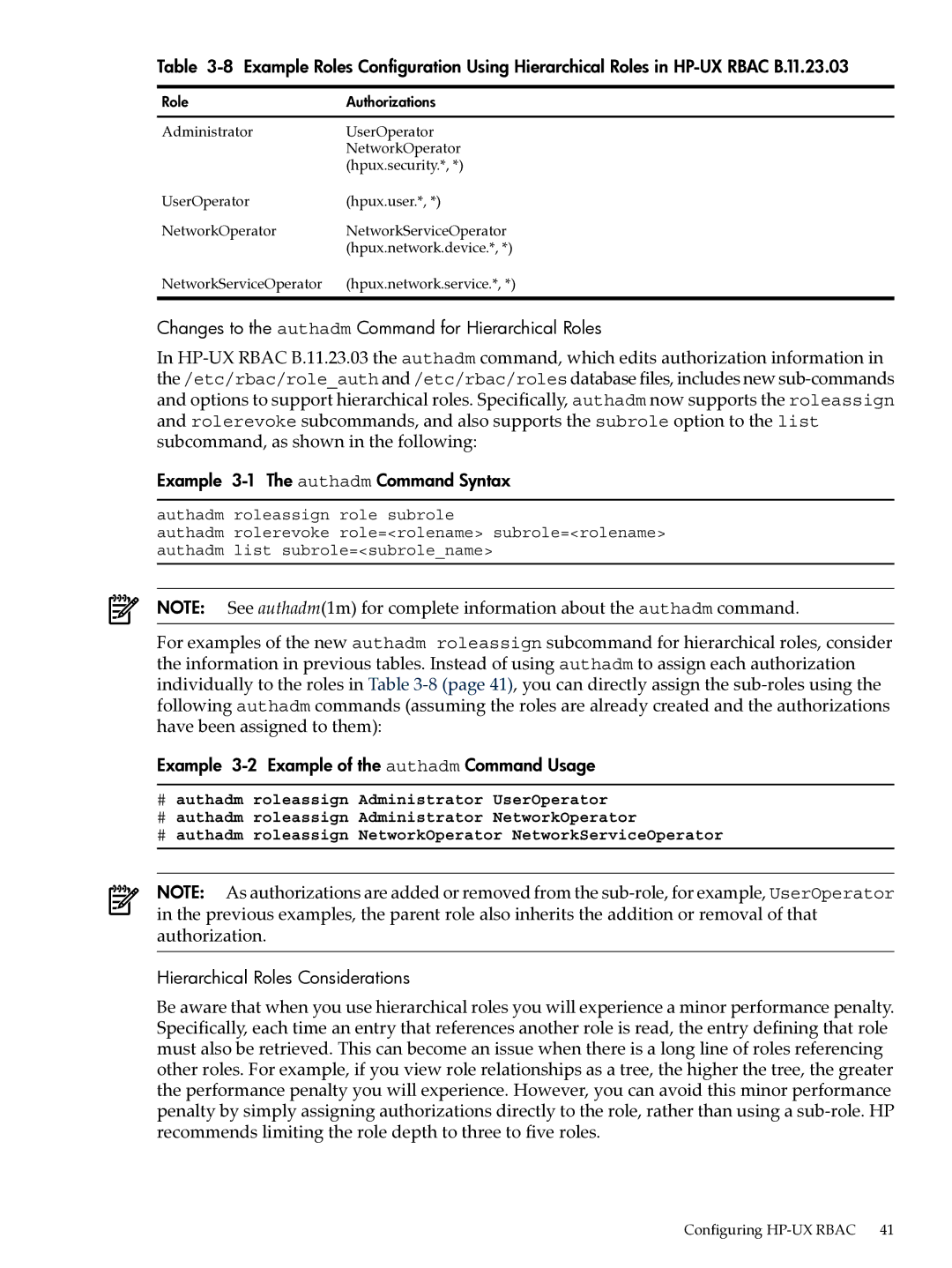
Table
Role | Authorizations |
Administrator | UserOperator |
| NetworkOperator |
| (hpux.security.*, *) |
UserOperator | (hpux.user.*, *) |
NetworkOperator | NetworkServiceOperator |
| (hpux.network.device.*, *) |
NetworkServiceOperator | (hpux.network.service.*, *) |
Changes to the authadm Command for Hierarchical Roles
In
Example 3-1 The authadm Command Syntax
authadm roleassign role subrole
authadm rolerevoke role=<rolename> subrole=<rolename> authadm list subrole=<subrole_name>
NOTE: See authadm(1m) for complete information about the authadm command.
For examples of the new authadm roleassign subcommand for hierarchical roles, consider the information in previous tables. Instead of using authadm to assign each authorization individually to the roles in Table
Example 3-2 Example of the authadm Command Usage
#authadm roleassign Administrator UserOperator
#authadm roleassign Administrator NetworkOperator
#authadm roleassign NetworkOperator NetworkServiceOperator
NOTE: As authorizations are added or removed from the
Hierarchical Roles Considerations
Be aware that when you use hierarchical roles you will experience a minor performance penalty. Specifically, each time an entry that references another role is read, the entry defining that role must also be retrieved. This can become an issue when there is a long line of roles referencing other roles. For example, if you view role relationships as a tree, the higher the tree, the greater the performance penalty you will experience. However, you can avoid this minor performance penalty by simply assigning authorizations directly to the role, rather than using a
Configuring