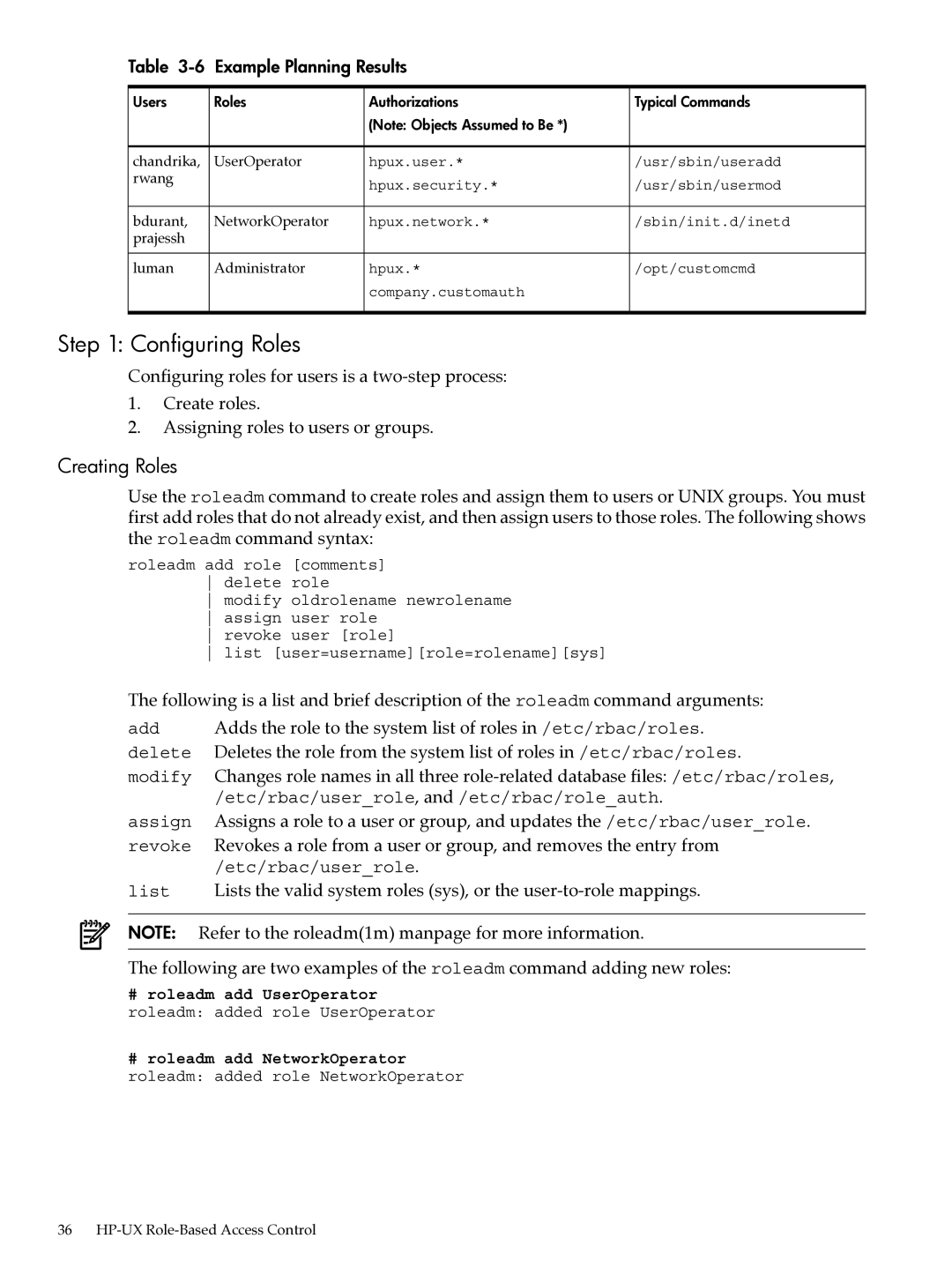
Table | Example Planning Results |
| |
Users | Roles | Authorizations | Typical Commands |
|
| (Note: Objects Assumed to Be *) |
|
chandrika, | UserOperator | hpux.user.* | /usr/sbin/useradd |
rwang |
| hpux.security.* | /usr/sbin/usermod |
|
| ||
bdurant, | NetworkOperator | hpux.network.* | /sbin/init.d/inetd |
prajessh |
|
|
|
luman | Administrator | hpux.* | /opt/customcmd |
|
| company.customauth |
|
Step 1: Configuring Roles
Configuring roles for users is a
1.Create roles.
2.Assigning roles to users or groups.
Creating Roles
Use the roleadm command to create roles and assign them to users or UNIX groups. You must first add roles that do not already exist, and then assign users to those roles. The following shows the roleadm command syntax:
roleadm add role | [comments] | |
delete | role | |
modify | oldrolename newrolename | |
assign | user role | |
revoke | user [role] | |
list [user=username][role=rolename][sys]
The following is a list and brief description of the roleadm command arguments:
add Adds the role to the system list of roles in /etc/rbac/roles. delete Deletes the role from the system list of roles in /etc/rbac/roles.
modify Changes role names in all three
assign Assigns a role to a user or group, and updates the /etc/rbac/user_role. revoke Revokes a role from a user or group, and removes the entry from
/etc/rbac/user_role.
list Lists the valid system roles (sys), or the
NOTE: Refer to the roleadm(1m) manpage for more information.
The following are two examples of the roleadm command adding new roles:
#roleadm add UserOperator roleadm: added role UserOperator
#roleadm add NetworkOperator roleadm: added role NetworkOperator
36